
Rate Limiting: Protecting Web Applications and Databases from DDoS Attacks

Introduction
Websites and online services face a significant risk from Distributed Denial of Service (DDoS) attacks. This type of attacks pose a major threat to data infrastructure. These malicious attacks aim to overwhelm servers with a flood of requests, rendering them unresponsive to legitimate users. Fortunately, rate limiting provides an effective first line of defense against DDoS attacks. In this article, we’ll explore what rate limiting is, how it works, and some tools and techniques for implementing it in web application frameworks.
What is Rate Limiting?
Rate limiting is a technique for controlling the rate at which a user or client can access a server or resource. The core idea is to set limits on how many requests a given user or IP address can make within a certain time period. Once the user exceeds that limit (see below), further requests are blocked or throttled until the time window resets. This prevents any single client from monopolizing server resources and disrupting service for others.
For example, you might configure your server to allow a maximum of 100 requests per minute per IP address. The 101st request within that minute would be blocked. Rate limits can be applied at various levels – per user account, per IP address, per geographic region, and so on. The optimal configuration depends on the nature of your application and the expected usage patterns.
Why is Rate Limiting Important for DDoS Prevention?
DDoS attacks typically involve a large number of coordinated clients (often a botnet of compromised machines) sending a high volume of requests to a target server. The goal is to consume the server’s resources (CPU, memory, network bandwidth) to the point that it can no longer respond to legitimate traffic.
By implementing strict rate limits, you can mitigate the impact of a DDoS attack. Even if the attackers control a large number of machines, each individual client will be restricted in how many requests it can send. This prevents the attackers from overwhelming your server resources.
Of course, rate limiting is not a complete DDoS protection solution on its own. Determined attackers may still be able to cause disruptions by controlling an extremely large botnet. But rate limiting is an important component of a defense-in-depth approach, working in concert with other measures like traffic filtering, blacklisting malicious IPs, and using specialized DDoS mitigation services.
Rate Limiting in Web Applications
Most web application frameworks provide mechanisms for rate limiting HTTP requests. These can be used to implement a strong first line of defense against DDoS attacks.
The exact implementation varies between frameworks, but the general principle is the same. The framework middleware tracks the number of requests from each client (usually identified by IP address) within a rolling time window. If a client exceeds the predefined limit, server blocks their requests until the time window resets.
For example, a simple rate limiting configuration might allow 100 requests per minute per IP address. Server meets the 101st request within a minute with a “429 Too Many Requests” HTTP response code. The same principle works with database connections. A bit later in this article we provide an example for the DataSunrise Security Rule which can serve as the rate limiting tool. The administrator chooses blocking method as follows:
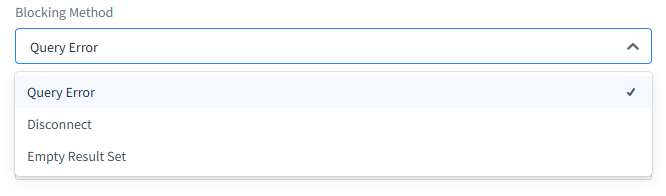
Figure 1 – DataSunrise blocking method in Security Rule setup. It also allows for the custom blocking message setup.
More advanced rate limiting setups can take into account additional factors, such as the specific route or endpoint being requested, or authenticated user information. This allows for more granular control over resource usage.
Server and User Rate Limits
When setting up rate limiting, it’s important to consider the different levels at which you can apply limits. Two common approaches are server-level limits and user-level limits.
Server-level rate limits apply to all requests coming into a server, regardless of the specific user or client making the request. These are useful for protecting against DDoS attacks that involve a large number of different IP addresses. Server-level limits ensure that the total traffic to your server stays within manageable levels.
User-level rate limits, on the other hand, apply to individual user accounts or API keys. These are useful for preventing abuse by individual users, even if their request volume wouldn’t be enough to disrupt the entire server. User-level limits can help maintain fair usage and prevent individual users from consuming more than their share of resources.
Ideally, a robust rate limiting setup will involve a combination of server-level and user-level limits, providing multiple layers of protection.
DataSunrise: Comprehensive Database Security and DDoS Protection
For organizations looking for a comprehensive solution to secure their databases and defend against DDoS attacks, DataSunrise offers a powerful set of tools. DataSunrise provides a database firewall that can monitor and block unwanted activity on a per-user or per-host basis.
With DataSunrise, you can set up granular security rules to prevent DDoS attacks, SQL injection, brute force attacks, and other threats. The tool allows you to define rate limits and thresholds for various types of database activities, ensuring that no single user or host can overwhelm your system.
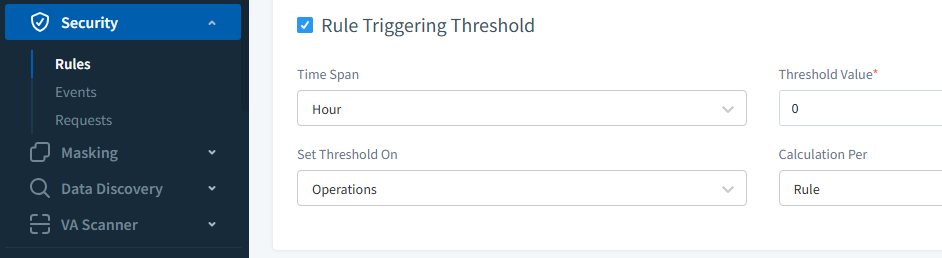
Figure 2 – Common for all the rules in DataSunrise. Threshold enables event firing only if query frequency exceeds predefined limit.
Below you can see DDoS attack prevention rule setup.
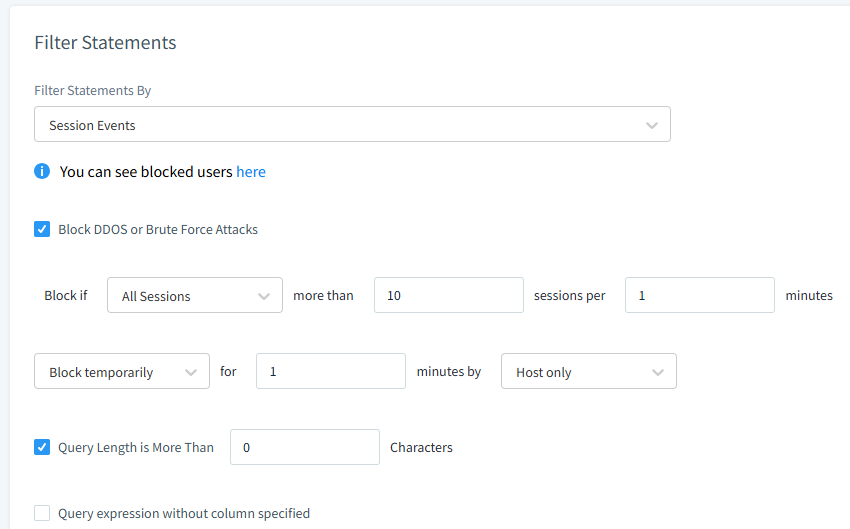
Figure 3 – Rate limiting with DataSunrise. Security rule setup.
DataSunrise supports a wide range of databases, including PostgreSQL, MySQL, SQL Server, and Oracle, and provides an intuitive web-based interface for managing your security settings. The tool also offers features for compliance auditing, data masking, and real-time activity monitoring.
Summary and Conclusion
Rate limiting is a crucial technique for defending against DDoS attacks and ensuring fair usage of web applications and APIs. By throttling the request rate from individual clients, rate limiting prevents malicious actors from overwhelming server resources.
We’ve seen how to implement rate limiting at various levels, including in web application frameworks and at the server level. An effective rate limiting strategy involves setting appropriate limits at multiple levels and regularly monitoring and adjusting these limits based on observed traffic patterns.
For a comprehensive database security and DDoS protection solution, consider DataSunrise. With its powerful database firewall and granular security rules, DataSunrise can help defend your databases against a wide range of threats, including DDoS attacks, SQL injection, and brute force attacks.
Used in combination with other security measures like traffic filtering and IP blacklisting, rate limiting and tools like DataSunrise can greatly enhance your application’s resilience against DDoS attacks.
To learn more about how DataSunrise can secure your databases and protect against DDoS attacks, reach out to our team for an online demo. We’ll be happy to show you the tool in action and discuss how we can tailor it to your specific needs.
