
SAP HANA Data Activity History

Cisco’s 2024 Cyber Threat Trends Report shows that modern businesses deal with about 50 database security incidents every day. Of these incidents, 76% target sensitive business data in systems like SAP HANA. As organizations handle large amounts of sensitive data, tracking and auditing database activities is now essential. It is not just a compliance requirement; it is a key security need. Understanding Data Activity History in SAP HANA provides organizations with the visibility and control needed to protect their valuable data assets.
Introduction to SAP HANA Data Activity History
SAP HANA provides essential features that allow users to capture data activity logs, which can be invaluable for troubleshooting, compliance audits, and ensuring data security. These logs track every change in the database. This includes data modification, creation, and deletion. They provide a detailed audit trail. By capturing who interacted with the data, when they did, and what specific actions they performed, businesses can maintain a higher level of accountability and transparency in their operations.
SAP HANA does this by using built-in SQL tools. These include SQL language features, views, and stored procedures. These tools help administrators watch and track all database activities.
Audit Capabilities in SAP HANA
In a different article about SAP HANA Audit, we discussed how SAP HANA can monitor database events. It can also track user activities. These capabilities form the foundation for data activity tracking. Audit logs give important information about who accessed certain data. They show when the access happened, how it was done, and any changes made to the data.
Native SAP HANA Data Auditing
SAP HANA provides powerful native tools to configure and manage auditing. These tools include SQL auditing, system views, triggers, and stored procedures. You can customize them to capture specific actions or events in the database.
1. Enabling and Configuring Auditing in SAP HANA
Auditing is not enabled by default in SAP HANA. To activate it, administrators must first enable the auditing service and then configure specific audit policies.
Activating Auditing via SAP HANA Cockpit:
- Login to SAP HANA Cockpit: Use the SAP HANA Cockpit to manage and configure audit logging.
- Enable Auditing: Navigate to the “Auditing” section and enable audit logging for the system database or specific tenant databases. Note that the system database controls audit configurations for tenant databases, which cannot modify audit trail targets independently.
- Configure Audit Policies: Define audit policies that specify the types of actions to be tracked, such as SQL statements or system configurations.
You can set up audit policies using an easy wizard in the SAP HANA Cockpit. This wizard uses SAP’s recommended settings for common auditing situations. You can then customize these policies based on the specific needs of the organization.
Sample SQL for Enabling Audit Policies:
To enable auditing using SQL, you can execute the following commands:
CREATE AUDIT POLICY policy_UserRoleManagement AUDITING ALL CREATE USER, DROP USER, CREATE ROLE, DROP ROLE LEVEL Critical; ALTER AUDIT POLICY policy_UserRoleManagement ENABLE;
This policy tracks the creation and deletion of users and roles in SAP HANA, and logs events at the Critical level.
2. Audit Actions in SAP HANA
SAP HANA allows you to audit a wide range of actions, such as:
- User Management: Creating or dropping users and roles, granting or revoking privileges.
- Data Access: Tracking read or write operations on sensitive data (e.g., SELECT, INSERT, UPDATE, DELETE statements).
- Configuration Changes: Monitoring modifications to system parameters, such as changes to .ini files or system settings related to encryption.
Audit actions can be defined by several parameters. These include the action status, which can be either successful or unsuccessful. They also involve target objects, such as tables, views, and schemas. Additionally, the users involved in the actions are considered. Some examples of audit actions include:
- Create or drop user and create or drop role
- Grant or revoke privileges on database objects
- Database queries (e.g., SELECT, UPDATE)
- System configuration changes, such as modifications to license keys or encryption settings.
You can record both successful and failed actions to provide a complete audit trail.
3. Managing Audit Trail Targets
Audit entries are stored in audit trails, which can be directed to different storage locations. SAP HANA supports the following targets for storing audit trails:
- Internal Database Table: This offers a safe place to store data in the database. It allows easy access to audit logs from SAP HANA.
- Linux Syslog: Secure logging system that is separate from the database. This adds extra protection. It ensures that the database administrator cannot change audit records.
- CSV File: Typically used for testing purposes, but not recommended for production environments.
Each audit policy can link to a specific target. This depends on how serious the event is. For example, critical actions might be logged in an internal table and also in a syslog.
For production systems, it is best to use Linux Syslog or the internal database table for audit logs. These options offer secure and tamper-proof storage.
4. Viewing and Analyzing the Audit Trail
Once audit policies are activated, you can view the audit trail to analyze events that have been recorded.
- Using SAP HANA Cockpit: The “Auditing” tile in the SAP HANA Cockpit provides an interface for reviewing audit logs. You can filter and sort the audit entries based on various criteria such as timestamp, user, or event type.
- Using SQL: You can also query the audit logs directly using SQL by querying the AUDIT_LOG view:
SELECT * FROM "PUBLIC"."AUDIT_LOG";
This system view allows you to access all audit log entries, which are stored securely and are read-only. Only users with AUDIT OPERATOR privileges can delete old audit entries from the underlying table.
5. Retaining and Managing Audit Logs
To prevent the audit table from growing indefinitely, administrators can configure retention periods for audit logs. After the retention period has expired, old audit entries are automatically deleted. This ensures that the system does not run out of space and helps maintain compliance with data retention policies.
The default minimum retention period lasts seven days, but organizations can customize it based on their needs. The following SQL command can be used to truncate the audit log:
ALTER SYSTEM CLEAR AUDIT LOG ALL;
This command completely clears the audit log, but it should be used cautiously to avoid losing valuable audit information.
Enhanced Security with DataSunrise for SAP HANA Data Activity History
While SAP HANA’s native capabilities are powerful, DataSunrise offers additional features for comprehensive Data Activity History management. DataSunrise provides:
- Centralized activity monitoring across multiple databases
- Advanced data masking capabilities
- Real-time alerting and reporting
- Simplified compliance management
Setting Up DataSunrise for SAP HANA
To set up DataSunrise’s audit features for SAP HANA, follow these steps:
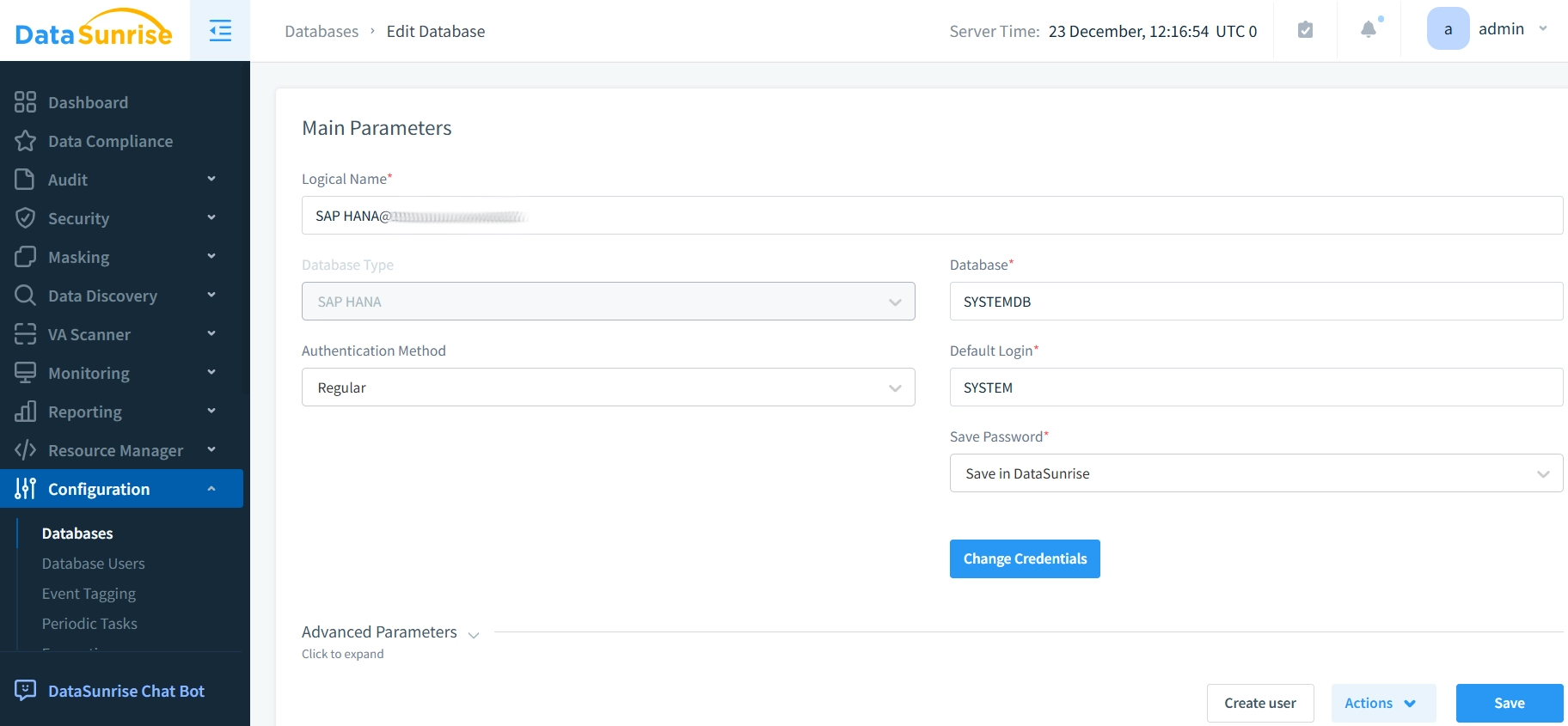
- Set up a DataSunrise SAP HANA instance.
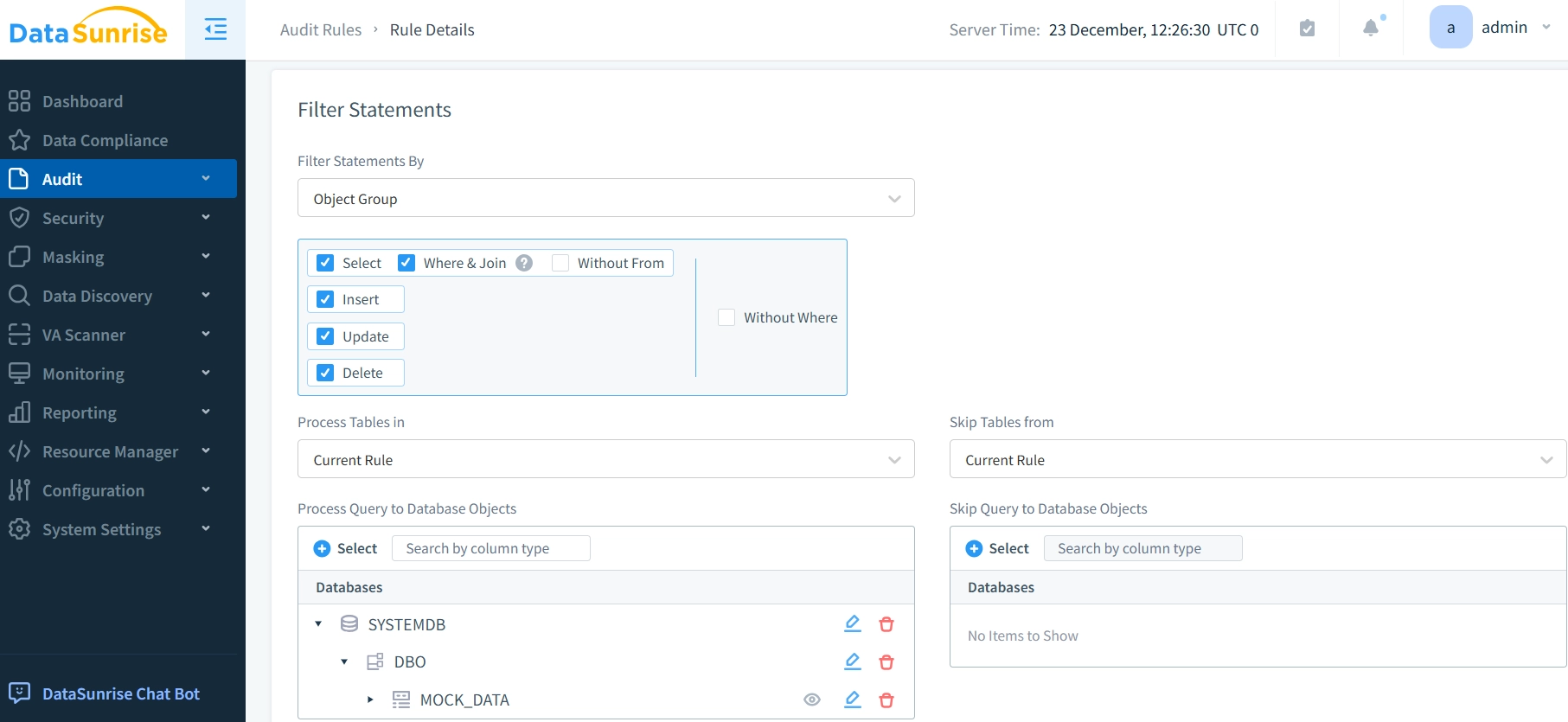
- Configure audit rules using the DataSunrise interface.
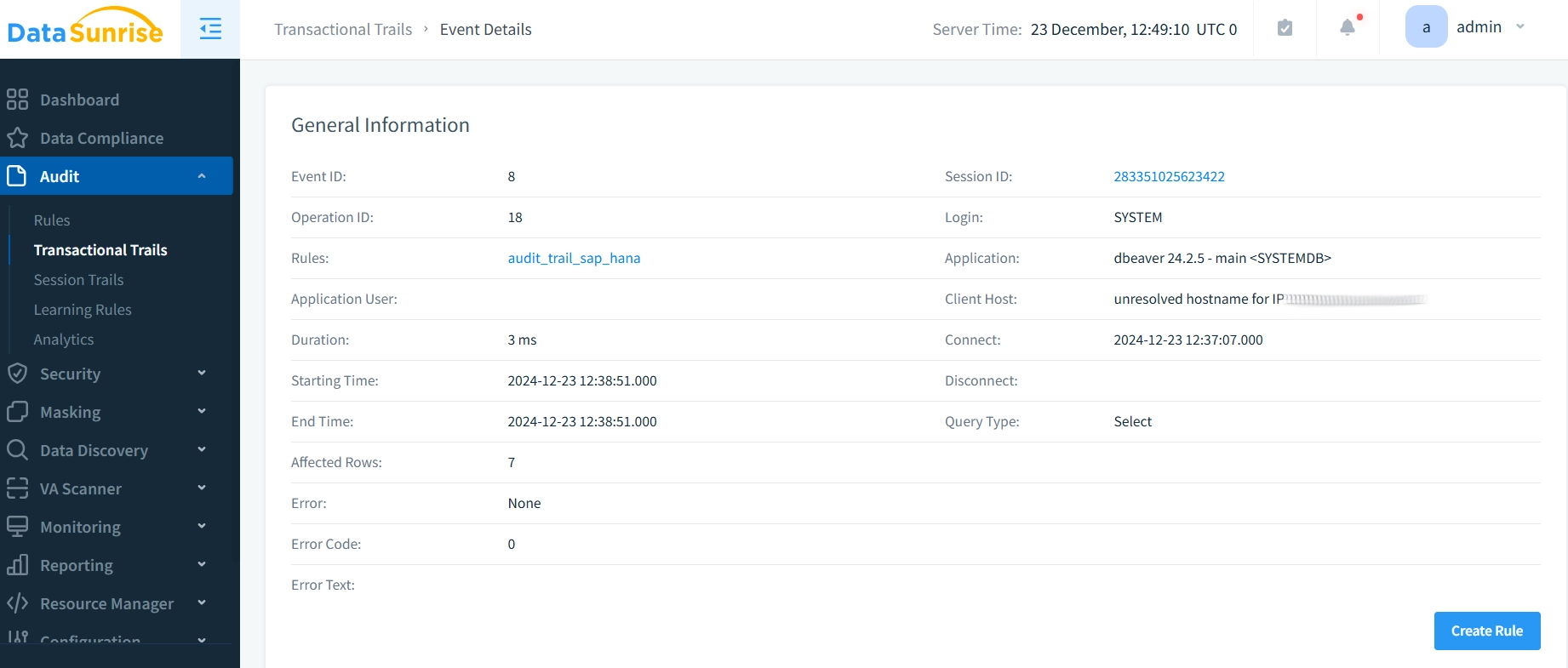
- Monitor database events in the “Transactional Trails” tab. Click on the event to see detailed information
Best Practices for Data Activity Monitoring
Effective data activity monitoring in SAP HANA requires a multi-layered approach.
- Policy Management: Start with policy management by establishing comprehensive monitoring policies and reviewing them quarterly to align with evolving security requirements. For access control, implement role-based permissions that restrict data visibility based on user responsibilities and organizational hierarchy.
- Documentation Management: Documentation plays a crucial role in maintaining security standards. Create and maintain detailed logs of all system changes, policy updates, and security incidents. This documentation serves as both a compliance tool and a reference for future security assessments.
- Third-Party Integration: Integration of third-party solutions like DataSunrise enhances monitoring capabilities beyond native features. These tools add extra security with advanced masking, real-time alerts, and detailed audit trails. They work well with SAP HANA’s built-in features.
- Automated Monitoring: Implement automated monitoring systems to track unusual data access patterns and potential security breaches. Set up alerts for suspicious activities and configure automated responses for critical security events.
- Data Classification: Establish clear data classification guidelines to determine appropriate monitoring levels for different types of data. Apply stricter monitoring rules to sensitive data categories and adjust activity tracking based on data importance.
- User Activity Analysis: Conduct regular analysis of user behavior patterns to identify potential security risks. Monitor privileged user actions with extra scrutiny and implement session recording for critical operations.
- Compliance Management: Align monitoring practices with relevant compliance requirements such as GDPR, HIPAA, or SOX. Regularly update monitoring procedures to reflect changes in compliance standards and maintain detailed compliance reports.
Conclusion
Tracking and auditing data activity is key to database security. SAP HANA Data Activity History offers strong tools to see who accessed data, when they did it, and why. Businesses can use built-in features in SAP HANA. These include SQL views, stored procedures, and audit tools. This helps them manage data clearly and responsibly.
Additionally, DataSunrise offers a comprehensive suite of security tools to further enhance data protection and compliance. DataSunrise is a great partner for businesses. It has centralized management, dynamic data masking, and audit trail features. These tools help protect sensitive data and ensure compliance with industry rules.
For more information about DataSunrise’s data security solutions for SAP HANA, visit our website and schedule an online demo. By using SAP HANA’s features and DataSunrise’s tools, businesses can build a strong and secure data environment. This setup helps them meet their auditing and compliance needs.
