
Self-Service Data Access

Introduction
The McKinsey Global Institute suggests that by 2025, nearly all organizations will naturally and regularly leverage data to support their work. Even today, data is embedded in every decision, interaction, and process. In this data-driven world, organizations face a constant challenge: how to provide employees with the information they need while maintaining data security and compliance. Enter self-service data access, a game-changing approach that’s revolutionizing how businesses handle data access control. This article delves into the world of new approach in data access, exploring its benefits, potential drawbacks, and implementation strategies.
It is worth mentioning that DataSunrise includes a feature called SSAR (Self-Service Access Request), which is intended for robust control of data access. When a DataSunrise administrator receives a request, they can decide whether to approve or decline it.
What is Self-Service Data Access?
Before we dive deep into the topic, let’s briefly touch on some fundamental concepts.
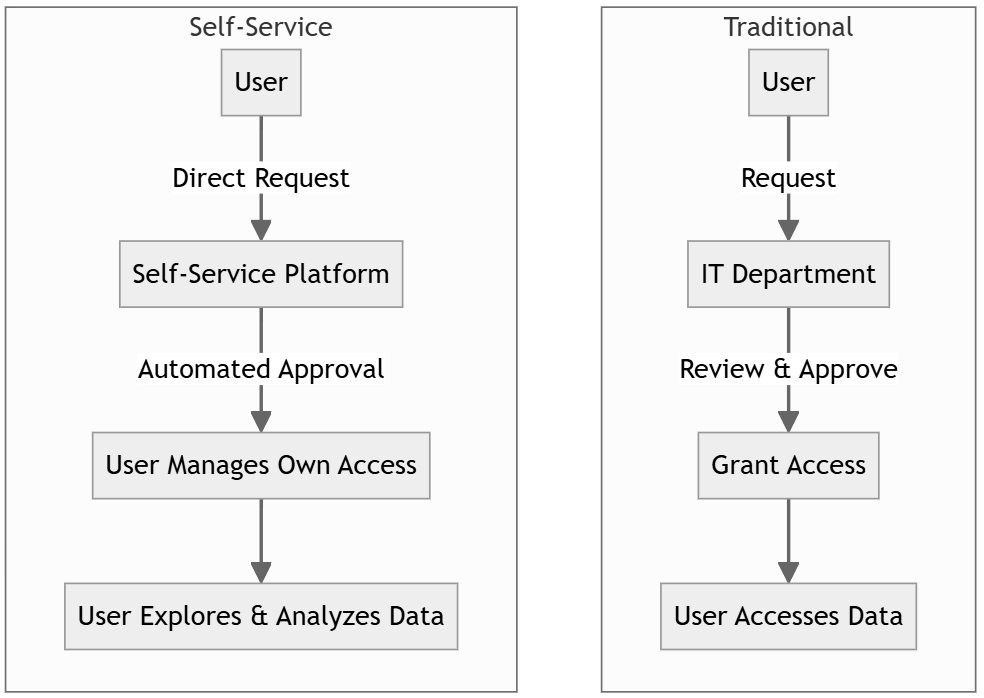
Data Access Service: A Quick Overview
Data access service refers to the systems and protocols that allow users to retrieve and interact with data stored in databases or other storage systems. These services act as a bridge between users and data, ensuring smooth and secure data flow.
Self-Service Data Access: Putting Users in Control
Self-service data access control is an approach that empowers users to manage their own data access privileges within predefined boundaries. Instead of relying solely on IT departments or database administrators, users can request, modify, or revoke their access to specific data sets.
The Benefits of User Activity
Implementing this data access model offers several advantages:
- Increased Efficiency: Users can quickly obtain the data they need without waiting for IT approval, speeding up decision-making processes.
- Reduced IT Workload: By shifting some responsibility to users, IT teams can focus on more strategic tasks.
- Enhanced Data Literacy: As users become more involved in data access, they develop a better understanding of data structures and governance.
- Improved Compliance: With proper controls in place, self-service models can enhance data governance and regulatory compliance.
- Flexibility: Users can adapt their access privileges as project needs change, promoting agility in data-driven initiatives.
Potential Drawbacks and Challenges
While this approach to data access offers many benefits, it’s not without its challenges:
- Security Risks: If not properly implemented, self-service models could lead to overly broad access or data breaches.
- Complexity: Setting up a robust self-service system requires careful planning and potentially complex infrastructure.
- User Education: Employees need training to understand their responsibilities in managing data access.
- Oversight: Organizations must maintain visibility into who has access to what data, which can be challenging in a self-service environment.
The Middleware Approach: A Robust Solution for Self-Service Data Access
One effective way to implement self-service data access is through a middleware approach. This method involves using a reverse proxy for data access rules, masking, and audit purposes.
How Middleware Facilitates Self-Service Data Access
The middleware sits between users and data sources, acting as an intermediary that enforces access policies, masks sensitive data, and logs all data access attempts. Here’s how it works:
- User Authentication: When a user attempts to access data, they first authenticate through the middleware.
- Access Control: The middleware checks the user’s permissions against predefined access rules.
- Data Masking: If necessary, the middleware applies data masking to protect sensitive information.
- Audit Logging: All access attempts and actions are logged for later review and compliance purposes.
- Data Delivery: If all checks pass, the requested data is delivered to the user.
Please note that points 1 to 4 are incorporated into the DataSunrise software. This integration makes it extremely easy to create and manage a wide variety of data access policies, including cases where users control their own data access.
Example: Implementing Middleware for Self-Service Data Access
Let’s consider a practical example of how a middleware solution might work in a fictional company, DataCorp.
// This example is written in JavaScript using Node.js and Express.js
const express = require('express');
const { createProxyMiddleware } = require('http-proxy-middleware');
const app = express();
// Define access rules
const accessRules = {
'/sales': ['sales_team', 'managers'],
'/hr': ['hr_team', 'managers'],
'/finance': ['finance_team', 'managers']
};
// Middleware to check user permissions
const checkPermissions = (req, res, next) => {
const userRole = req.headers['user-role'];
const path = req.path;
if (accessRules[path] && accessRules[path].includes(userRole)) {
next();
} else {
res.status(403).send('Access denied');
}
};
// Set up proxy with permission check
const proxy = createProxyMiddleware({
target: 'http://internal-data-server',
changeOrigin: true,
onProxyReq: (proxyReq, req, res) => {
// Log access attempt
console.log(`User ${req.headers['user-id']} attempted to access ${req.path}`);
}
});
app.use(checkPermissions);
app.use('/', proxy);
app.listen(3000, () => console.log('Proxy server running on port 3000'));In this example, the middleware checks the user’s role against predefined access rules before allowing the request to proceed to the internal data server. It also logs all access attempts for audit purposes.
Best Practices for Implementing Data Access
To ensure a successful implementation of self-service data access, consider the following best practices:
- Start Small: Begin with a pilot program involving a limited set of data and users.
- Establish Clear Policies: Define and communicate clear data access policies to all users.
- Provide Training: Offer comprehensive training on data governance and the self-service system.
- Implement Strong Authentication: Use multi-factor authentication to enhance security.
- Regular Audits: Conduct regular audits of access patterns and permissions.
- Automate Where Possible: Use automation tools to streamline access requests and approvals.
- Monitor and Adjust: Continuously monitor the system and adjust policies as needed.
The Future of Self-Service Data Access
As data continues to grow in volume and importance, self-service data access is likely to become increasingly prevalent. In the future, we will have improved tools for controlling access. We will also see smarter anomaly detection using AI. Additionally, there will be closer connections with cloud data platforms.
With DataSunrise, you can implement self-service data solutions by leveraging our market-leading tools for the following aspects:
Access Management: Our Security Rules can be seamlessly integrated into a self-service system in reverse proxy mode.
Dynamic Data Masking: DataSunrise’s flexible and easy-to-use data masking can be applied dynamically based on user permissions in a self-service scenario.
Comprehensive Auditing: Our exceptional auditing capabilities provide valuable monitoring for self-service access.
Summary and Conclusion
Self-service data access represents a significant shift in how organizations manage data access control. Companies can improve efficiency and reduce IT workload by letting users control their own data access within set limits. However, successful implementation requires careful planning, robust security measures, and ongoing monitoring.
Middleware can control who can access data, protect sensitive information, and monitor user activity. This makes it a reliable choice for granting users access to their own data. As organizations continue to grapple with the challenges of data management in the digital age, self-service models are likely to play an increasingly important role.
For organizations looking to implement robust data access solutions, DataSunrise offers user-friendly and flexible tools for database audit, masking, and compliance. Visit our website at DataSunrise.com for an online demo and discover how we can help you empower your users while maintaining strict data security and compliance.
