
Snowflake Database Audit
Introduction
In today’s data-driven world, ensuring the security and proper usage of your Snowflake database is crucial. It’s worth mentioning that DataSunrise provides exceptional audit capabilities. For robust audit control, you should definitely consider trying it. However, in this article, we will focus on discussing built-in Snowflake database audit capabilities.
Monitoring access to your Snowflake database is an essential aspect of maintaining data integrity and preventing unauthorized access. In this article, we will explore the basics of Snowflake database audit, data access analysis, and access monitoring. We will also provide examples of how to research Snowflake database usage over a period of time and query the workload from the Snowflake database servers.
What is Snowflake Access Monitoring?
Snowflake access monitoring involves tracking and analyzing the activity of users within your Snowflake database. It helps you understand who is accessing your data, when they are accessing it, and what actions they are performing. By monitoring access, you can detect suspicious behavior, identify potential security breaches, and ensure compliance with data privacy regulations.
Data Available for Access Analytics in Snowflake
Snowflake offers a wealth of data that organizations can use for access analytics. Some of the key data points available include:
- Login attempts and successful logins
- Query execution details, including the user, role, and timestamps
- Data access patterns, such as the tables and columns accessed
- Resource consumption, including CPU and memory usage
These data points can be accessed through various system tables and views provided by Snowflake.
Researching Snowflake Database Audit
To research Snowflake database usage over a period of time, you can leverage the QUERY_HISTORY view. This view contains information about the queries executed in your Snowflake account. Let’s look at an example of how to query this view to analyze user activity.
SELECT USER_NAME, ROLE_NAME, COUNT(*) AS QUERY_COUNT FROM SNOWFLAKE.ACCOUNT_USAGE.QUERY_HISTORY WHERE START_TIME >= '2023-01-01' AND START_TIME < '2024-06-01' GROUP BY USER_NAME, ROLE_NAME ORDER BY QUERY_COUNT DESC;
This query retrieves the user name, role name, and the count of queries executed by each user within the specified time range. It helps you understand which users are most active and what roles they are using. The result can be as follows:
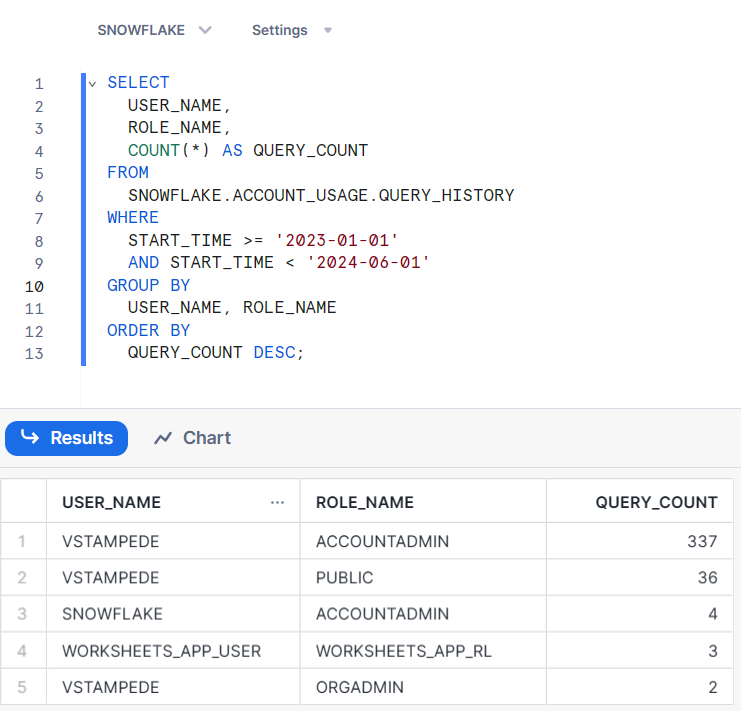
Querying Workload from Snowflake Database Servers
To analyze the workload on your Snowflake database servers, you can use the WAREHOUSE_LOAD_HISTORY table. This table provides insights into the resource consumption of your warehouses. Here’s an example query:
SELECT WAREHOUSE_NAME, AVG(AVG_RUNNING) AS AVG_QUERIES_RUNNING, AVG(AVG_QUEUED_LOAD) AS AVG_QUERIES_QUEUED, AVG(AVG_BLOCKED) AS AVG_QUERIES_BLOCKED FROM SNOWFLAKE.ACCOUNT_USAGE.WAREHOUSE_LOAD_HISTORY WHERE START_TIME >= '2023-01-01' AND START_TIME < '2024-06-01' GROUP BY WAREHOUSE_NAME ORDER BY AVG_QUERIES_RUNNING;
This query retrieves the averaged resources consumed by each warehouse within the specified time range. It helps you identify the most resource-intensive warehouses and optimize your Snowflake setup accordingly. The result of the query given above is as follows:
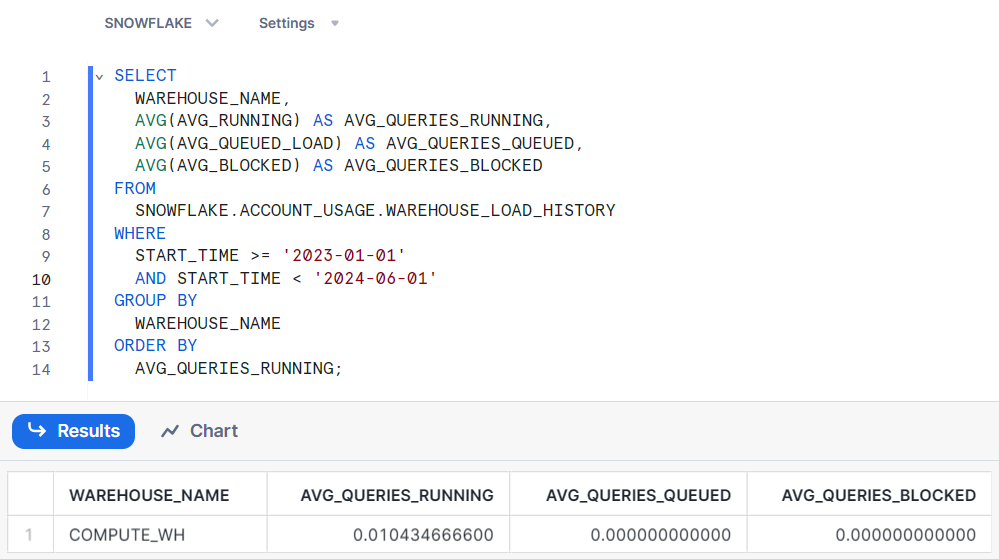
Best Practices for Snowflake Access Monitoring
To effectively monitor access to your Snowflake database, consider the following best practices:
- Regularly review user activity logs and access patterns
- Set up alerts for suspicious or unauthorized access attempts
- Implement role-based access control (RBAC) to ensure users have appropriate permissions
- Use multi-factor authentication (MFA) to strengthen user authentication
- Encrypt sensitive data at rest and in transit
Follow these tips to make your Snowflake database more secure and protect your important data.
DataSunrise: User-Friendly Tools for Snowflake Database Audit
Snowflake has access management features, but using DataSunrise can make the process much easier. DataSunrise offers user-friendly and flexible tools for Snowflake database usage analysis, masking, and compliance. With DataSunrise, you can gain deep insights into user activity, detect anomalies, and ensure adherence to data privacy regulations.
We invite you to schedule an online demo with our DataSunrise team to see how our solutions can enhance your Snowflake access monitoring capabilities. Our experts will provide you with a personalized walkthrough and answer any questions you may have.
Conclusion
Monitoring access to your Snowflake database is crucial for maintaining data security and compliance with data protection regulations. You can use data from Snowflake to track what users are doing and how resources are being used. This data is available in tables such as QUERY_HISTORY and WAREHOUSE_METERING_HISTORY. Implementing best practices and utilizing tools like DataSunrise can further strengthen your access monitoring efforts.
Remember, proactive monitoring and analysis of your Snowflake database access is essential in today’s data-driven landscape. Take the necessary steps to safeguard your data and ensure its proper usage.
