
Enhancing Data Security with Static Data Masking in MariaDB

MariaDB, a popular open-source relational database management system, handles vast amounts of data for organizations worldwide. As data privacy concerns grow, static data masking in MariaDB has become an essential technique for safeguarding sensitive information. This article discusses static data masking in MariaDB. It explains why it is important, how to set it up, and the advantages it can bring to your organization.
Understanding Static Data Masking in MariaDB
Static data masking in MariaDB involves creating a permanent, masked copy of your database. This process replaces sensitive data with fictional yet realistic information. The original database is safe, and you can use the masked version for testing, development, or sharing with others.
For example, a financial institution might create a masked copy of their customer database for software testing. The original database contains real names, addresses, and account numbers. The masked version replaces these with fictitious data that maintains the same format and characteristics.
MariaDB databases often store sensitive information such as personal details, financial records, and confidential business data. Protecting this data is crucial for maintaining privacy, complying with regulations, and preventing security breaches. Static data masking provides a safe method to use data. It prevents the exposure of real production information in non-production environments.
Consider a healthcare provider using MariaDB to store patient records. They need to share data with researchers but can’t risk exposing real patient information.
Static data masking makes a fake version of a database. It replaces real names, social security numbers, and medical conditions with made-up data. The overall statistics remain similar to the original.
Implementing Static Data Masking
Several ways of masking data statically in MariaDB exist, both native and third-party. Let’s review native means first.
The first step in implementing static data masking in MariaDB is to identify which data needs protection. This involves analyzing your database schema and pinpointing columns containing sensitive information like names, addresses, or financial data.
Once you’ve identified sensitive data, you need to select appropriate masking techniques. MariaDB static data masking offers several methods, including substitution, shuffling, encryption, and nulling. For instance, you might use substitution to replace real email addresses with fake ones while maintaining a realistic format. Or you could use shuffling to rearrange salary data within a department, preserving overall statistics without revealing individual salaries.
After choosing your masking techniques, you need to set up masking rules in your MariaDB static data masking tool. These rules define which columns to mask and how to mask them. You might create a rule that masks credit card numbers by replacing all but the last four digits with asterisks.
This process might seem and be time-consuming for beginners and when applying to a large-scale storages. An alternative way that simplifies the masking process is to use third-party solutions like DataSunrise.
To create and apply static masking tasks, you must create instances of source and target databases.
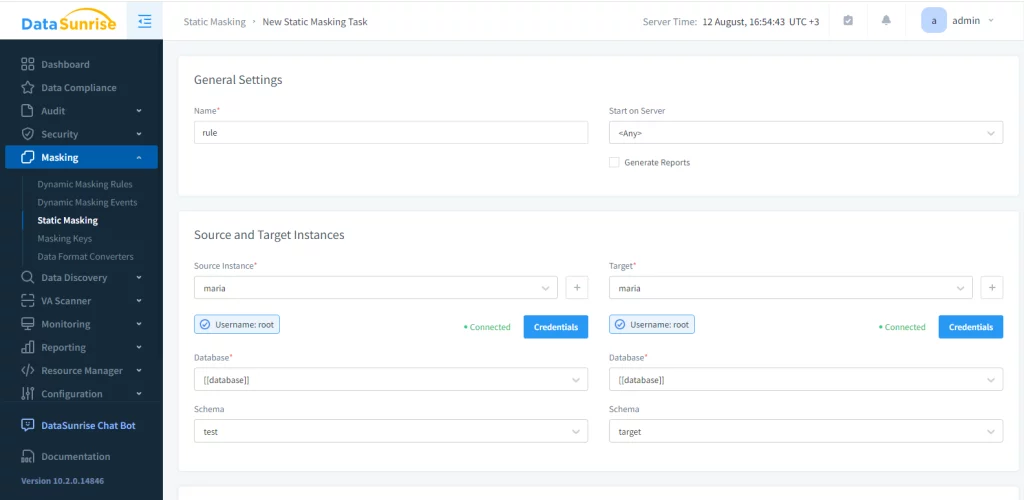
Then, set up a static masking task. During this stage, we select the source and target databases and determine the order in which to launch the task.
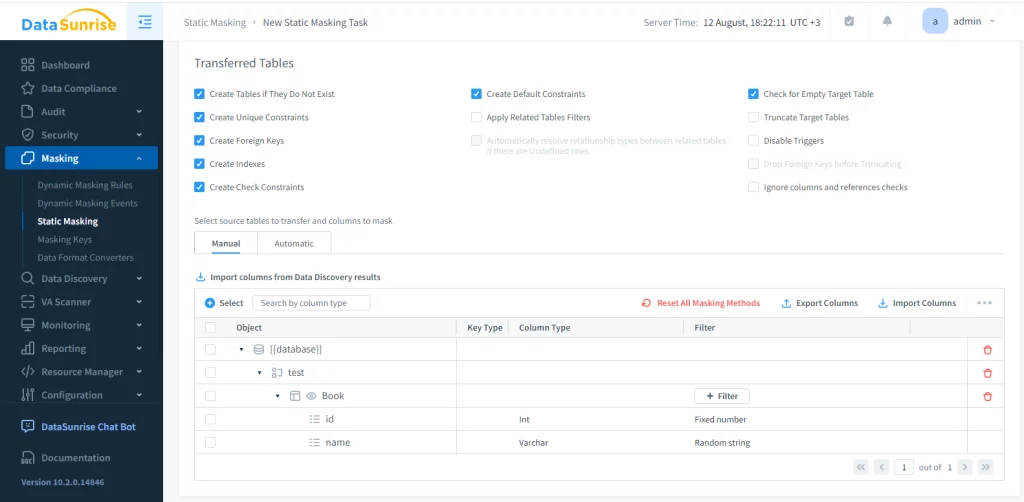
Finally. the masking rules must be configured. You can configure various settings in addition to masking options. One of these settings includes cutting down the target database structure before moving the masked data.
With your rules in place, you can execute the static data masking process. This creates a new, masked copy of your MariaDB database. The process can take time, depending on the size of your database and the complexity of your masking rules.
Benefits and Challenges of Static Data Masking
Static data masking in MariaDB offers several benefits. It enhances data security by reducing the risk of data breaches and unauthorized access. It also helps with compliance, allowing organizations to meet strict data protection regulations. Additionally, it enables safer development and testing practices by providing realistic data without risking exposure of sensitive information.
However, MariaDB static data masking also presents challenges. Maintaining data relationships and referential integrity across tables and columns can be tricky. Balancing realism and privacy in masked data can be challenging, as can managing large datasets during the masking process.
Best Practices for Data Masking in MariaDB
To maximize the effectiveness of your MariaDB static data masking efforts, consider these best practices:
Regularly review and update your masking rules to ensure they align with current security needs and regulations. Use strong encryption for highly sensitive data in addition to masking. Implement strict access controls for masked databases.
Maintain clear documentation of your masking procedures. Periodically test masked data to ensure it remains useful while still protecting sensitive information.
Conclusion
As data protection becomes increasingly important, we can expect to see advancements in static data masking techniques for MariaDB. These may include AI-powered masking, automated compliance checks, and closer integration with data governance platforms.
Static data masking in MariaDB is a powerful tool for protecting sensitive information while maintaining data utility. By using strong masking techniques, you can improve security, follow rules, and handle data safely in non-production areas.
Remember, effective static data masking is an ongoing process. Stay informed about the latest techniques and tools to keep your sensitive information secure.
MariaDB static data masking helps organizations protect their data. It allows useful access while keeping data safe. This strategy is important for organizations of all sizes because data protection needs are always changing.
