
Static Data Masking in MySQL

MySQL, a widely used database management system, often stores critical and sensitive data for organizations worldwide. As data privacy concerns grow, companies need robust solutions to protect this information. Static data masking in MySQL offers an effective way to safeguard critical data while maintaining its utility. This article explores how static data masking works in MySQL, its benefits, and implementation strategies.
Understanding Static Data Masking and Its Importance
Static data masking is a technique that permanently alters sensitive data in a database copy. It replaces actual information with realistic but false data.
This process creates a secure duplicate that developers can use for testing, development, or analyzing. The original information remains unchanged. This approach is crucial for MySQL databases that often contain personal details, financial records, and other confidential information.
One cannot overstate the importance of static data masking. It enhances security by making masked data useless to attackers if a breach occurs. It also helps organizations meet compliance requirements like GDPR, HIPAA, and CCPA. Furthermore, it allows development and testing teams to work with realistic data without risking exposure of actual sensitive information.
Implementing Static Data Masking in MySQL
Implementing static data masking involves several steps. First, you need to identify sensitive data within your database. Then, you create masking rules for each type of sensitive data. Finally, you apply these rules to create a masked copy of the database.
Here’s an example of how to implement static data masking in MySQL:
-- Create a new table for masked data
CREATE TABLE masked_customers LIKE customers;
-- Insert masked data into the new table
INSERT INTO masked_customers
SELECT
id,
CONCAT(LEFT(name, 1), REPEAT('*', LENGTH(name) - 1)) AS name,
CONCAT(SUBSTRING(email, 1, 2), '***@', SUBSTRING_INDEX(email, '@', -1)) AS email,
CONCAT(LEFT(phone, 3), '-***-', RIGHT(phone, 4)) AS phone,
CONCAT(SUBSTRING_INDEX(address, ' ', 1), ' ', REPEAT('*', 5), ' ', SUBSTRING_INDEX(address, ' ', -1)) AS address
FROM customers;
-- Verify the masked data
SELECT * FROM masked_customers LIMIT 5;
This example creates a new table called `masked_customers` with the same structure as the original `customers` table. It then inserts masked data into this new table.
We mask names by keeping the first letter and replacing the rest with asterisks. They partially mask emails, preserving the domain. Phone numbers keep the first three and last four digits visible. We mask addresses by keeping the first and last words and replacing the middle with asterisks.
Implementation with DataSunrise
MySQL has built-in options for static masking, but it can be difficult to use with large amounts of data. At these times, we suggest using third-party solutions. To mask statically using DataSunrise, you must take several steps:
Firstly, an instance of MySQL database is to be created:
This feature assists in establishing security, masking, and auditing rules. It also helps in creating static masking tasks for the proxy to use with the source database. Next, we must specify the task.
This process has three parts: managing servers, choosing data sources, and setting up masking rules. When you select the target, truncate it before starting the task for integrity reasons. As for the masking rules, we will mask the ‘test_table’ table in ‘test’ schema.
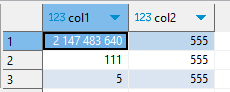
The result we get is as follows:
Best Practices and Challenges
When implementing static data masking in MySQL, it’s crucial to follow best practices. Use consistent masking rules across all instances of sensitive data to maintain data integrity. Preserve database relationships when masking to avoid breaking application functionality. Thoroughly test the masked data in your applications to identify any issues before deployment.
Document your masking process and rules for future reference and consistency. Regularly check and update your masking strategy to make sure it fits your organization’s needs and follows changing regulations.
However, static data masking in MySQL also presents some challenges. Masking large databases can be time-consuming and resource-intensive. Some data types may require complex masking rules, adding to the implementation difficulty.
Maintaining data relationships across masked databases can be tricky and requires careful planning. It’s also worth noting that masked databases might perform differently than their original counterparts, necessitating performance testing.
The Future of Static Data Masking in MySQL
As privacy concerns continue to grow, we can expect further advancements in MySQL static data masking. Future developments might include more sophisticated masking techniques, improved performance for large-scale masking operations, and easier configuration options.
We may also see better integration with other MySQL tools and processes, enhancing overall data management strategies. As new data protection laws emerge, we can anticipate enhanced features to ensure compliance with evolving regulations.
Conclusion
Static data masking in MySQL is a powerful tool for protecting sensitive information. It allows organizations to safeguard critical data without sacrificing functionality or performance. By using MySQL static data masking, companies can improve data security, comply with regulations, and keep user trust.
Remember, effective data masking is not a one-time task but an ongoing process. Check your MySQL data masking methods regularly.
Update them as needed. This will help ensure they meet your company’s needs and comply with new regulations.
You can enhance data protection in MySQL by using static data masking. This method helps safeguard your data while maintaining the usefulness and importance of your databases. Static data masking allows you to conceal sensitive information without compromising the overall functionality of your databases.
As we move forward, we cannot overstate the importance of such protective measures. Data masking in MySQL is important for protecting data privacy and security. A crucial tool for organizations to safeguard their data exists.
