
Sybase Audit Logs

Maintaining robust audit logs is essential for securing your database environment and ensuring compliance with regulatory standards. A comprehensive audit log for Sybase not only tracks critical events such as user logins, schema modifications, and data updates but also serves as a key tool in identifying unauthorized access or suspicious activities that could jeopardize your sensitive data. For an in‐depth understanding of the importance of audit trails, you can refer to the Audit Trails documentation.
This article details how you can implement, manage and improve your audit logging system using Sybase’s own tools, such as isql and sp_audit, as well as advanced solutions offered by DataSunrise.
The Importance of a Sybase Audit Log
An effective audit log plays a pivotal role in ensuring database security and operational transparency. By systematically recording every critical action—like login attempts, data modifications, and administrative operations—a well-maintained audit trail allows administrators to quickly detect and investigate anomalies.
Compliance and Security:
Regulatory frameworks like GDPR and HIPAA mandate stringent monitoring of data access and modifications. An audit log not only helps you meet these standards but also protects your sensetive data from unauthorized access. For example, exploring the HIPAA Compliance guidelines can offer insights on structuring your audit strategies.
Operational Transparency:
Audit logs serve as an essential tool for troubleshooting issues and verifying transactions. Detailed records—as explained in the Audit Logs resource—ensure you have a clear history of activities to analyze when unexpected changes occur.
In your day-to-day administration, referring to Audit Guide insights and reviewing the Compliance Regulations can provide both strategic and tactical advantages.
Sybase Native Audit Log
Sybase offers a range of built-in tools and utilities to implement an effective audit log. These native capabilities allow administrators to capture, manage, and analyze audit data, ensuring that every critical operation is logged and monitored.
Leveraging sp_audit for Configuring Audits
At the core of Sybase’s native auditing system is the sp_audit stored procedure. This command provides granular control over what is recorded in the audit logs. With sp_audit, you can choose to monitor a wide range of activities—from user login attempts to specific data modifications. For example, the command:
sp_audit "login", "all", "all", "on"
activates auditing for all login attempts, ensuring that every access—successful or failed—is logged. More details on configuring these events can be found in the Audit Trails documentation.
You can also tailor your audit settings to capture specific actions. Consider this example for auditing updates on default tables:
sp_audit "update", "all", "default table", "on"
This setup logs all update operations on any new table created within the current database, providing critical insights into data modifications.
Check system tables and views:
Query results from syslogins and sysprocesses tables.
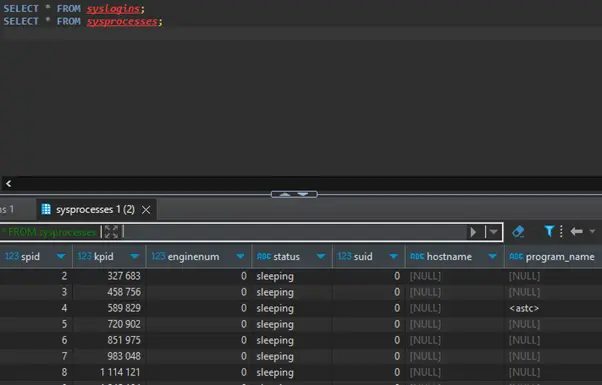
For additional technical details, refer to the official Sybase Security Administration documentation.
Using isql for Command-Line Auditing
The isql utility is a powerful command-line tool that facilitates direct execution of SQL scripts on your Sybase server. It is particularly useful for automating routine audit log management tasks. For instance, to archive older audit records, you might create a stored procedure like this:
CREATE PROCEDURE ArchiveOldLogs AS BEGIN INSERT INTO AuditArchive (event_id, event_type, user_id, event_time, table_name) SELECT event_id, event_type, user_id, event_time, table_name FROM AuditTrailWHERE event_time < DATEADD(month, -6, GETDATE()) DELETE FROM AuditTrail WHERE event_time < DATEADD(month, -6, GETDATE()) END;
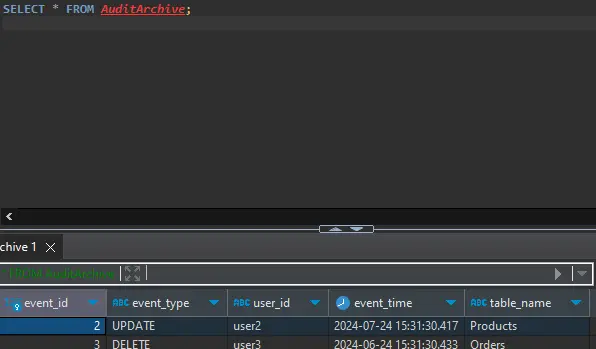
Running such a script via isql ensures that your audit logs remain both comprehensive and efficient. Insights into maintaining secure database environments can be further explored in the Database Security best practices resource.
Automation with Triggers, Stored Procedures, and SQL Views
In addition to sp_audit and isql, Sybase’s native auditing tools include triggers and stored procedures that capture changes in real time. For example, a trigger on the Employees table to log every insert, update, or delete operation may look like this:
CREATE TRIGGER AuditEmployeeChanges
ON dbo.Employees
FOR INSERT, DELETE, UPDATE
AS
BEGIN
IF (SELECT COUNT(*) FROM inserted) > 0 AND (SELECT COUNT(*) FROM deleted) = 0
BEGIN
INSERT INTO AuditTrail (event_type, user_id, event_time, table_name)
SELECT 'INSERT', suser_name(), GETDATE(), 'Employees'
END
IF (SELECT COUNT(*) FROM deleted) > 0 AND (SELECT COUNT(*) FROM inserted) = 0
BEGIN
INSERT INTO AuditTrail (event_type, user_id, event_time, table_name)
SELECT 'DELETE', suser_name(), GETDATE(), 'Employees'
END
IF (SELECT COUNT(*) FROM inserted) > 0 AND (SELECT COUNT(*) FROM deleted) > 0
BEGIN
INSERT INTO AuditTrail (event_type, user_id, event_time, table_name)
SELECT 'UPDATE', suser_name(), GETDATE(), 'Employees'
END
END
GO
This trigger reinforces your audit strategy by documenting every change made to the Employees table. For further technical details, consult the Sybase System Procedures documentation.
Additionally, SQL views can simplify the analysis of audit data. For example:
CREATE VIEW AuditSummary AS
SELECT event_time, user_id AS username, event_type, table_name AS object_name
FROM AuditTrail
WHERE event_type IN ('INSERT', 'UPDATE', 'DELETE');
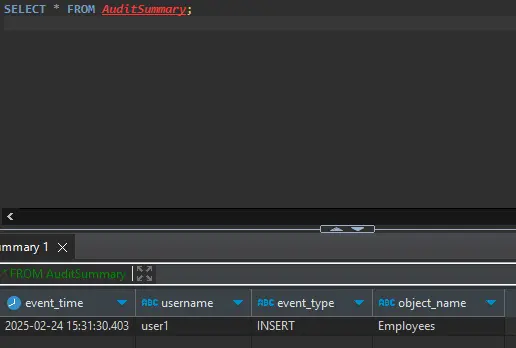
This view focuses on key operations, making it easier to identify anomalies that might impact your sensetive data. For more guidance on securing audit data, refer to the Security Policies documentation.
Finally, for a broader perspective on configuration and optimization, the IBM Sybase Configuration Guide offers comprehensive technical details.
Sybase Audit Log with DataSunrise
While native tools provide a solid foundation for auditing, organizations managing multiple instances or large-scale environments often require enhanced capabilities. DataSunrise is an advanced database security platform that complements Sybase’s built-in features by offering centralized management, real-time monitoring, and advanced reporting—all crucial for a modern audit log.
Overview of DataSunrise
DataSunrise seamlessly integrates with Sybase to capture audit logs while adding features like data masking, SQL injection detection, and centralized log management. For organizations focused on audit optimization, detailed information on audit storage can be found in the Audit Storage documentation.
Configuring DataSunrise with Sybase
Setting up DataSunrise to work with your Sybase environment is straightforward:
Step 1: Adding a Sybase Instance
Access the DataSunrise web interface, click “Add New Instance,” and select Sybase as the database type. Enter your connection details (hostname, port, and authentication credentials) to enable DataSunrise to pull audit data directly from your Sybase server. Detailed configuration instructions are available in the Audit Guide.
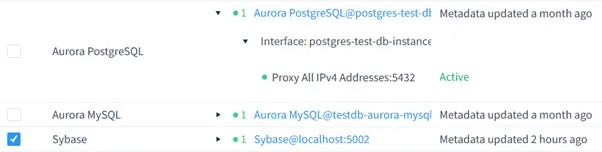
Step 2: Defining Audit Rules
With your Sybase instance connected, navigate to the auditing configuration panel within the DataSunrise dashboard. Here, you can set up rules to monitor events such as schema modifications, failed login attempts, and unauthorized data access.
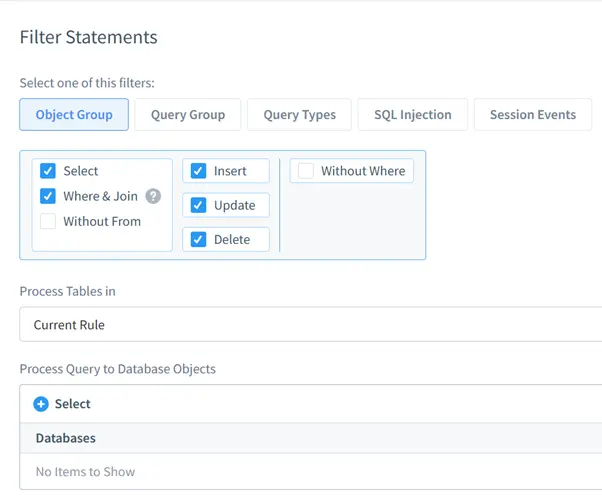
Step 3: Managing and Reviewing Logs
DataSunrise offers powerful tools for audit log management:
- Real-Time Monitoring: View live updates of database activities to quickly spot security issues.
- Custom Alerts: Configure notifications (via email or SMS) for critical events.
- Advanced Reporting: Generate detailed compliance reports aligned with industry standards, as outlined in GDPR Compliance.
- Log Archiving: Automate the archiving of older logs to maintain system performance.
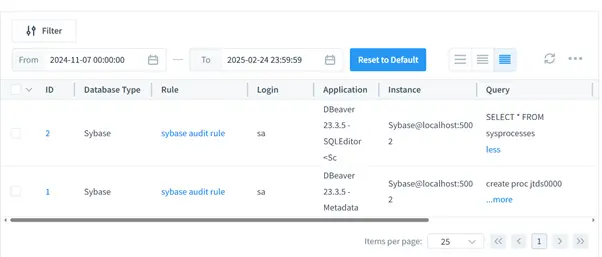
These features create a robust framework for audit log management that integrates seamlessly with your existing Sybase environment.
Conclusion
A comprehensive audit log for Sybase is vital for ensuring database security, maintaining compliance, and achieving operational transparency. Leveraging native tools—such as sp_audit, isql, triggers, and SQL views—allows administrators to build a robust audit trail that captures every critical action. This foundation is further strengthened by integrating advanced solutions like DataSunrise, which offers centralized management, real-time alerts, and sophisticated reporting capabilities.
By adopting these best practices, your organization can proactively safeguard its sensitive data, swiftly detect and respond to potential security incidents, and ensure a resilient database environment. Embrace these best practices today to build a secure, transparent, and efficient auditing framework that meets the evolving challenges of modern data management. To learn more about how DataSunrise can transform your database security strategy, visit our website to learn more and request an online demonstration.
