
Sybase Database Activity History: Advanced Auditing and Compliance Solutions

As organizations grow increasingly reliant on digital systems, robust database management becomes a non-negotiable requirement. Sybase, a prominent relational database management system, empowers organizations to manage their data effectively. However, with great power comes great responsibility—ensuring data security, regulatory compliance, and operational transparency is crucial. Auditing Sybase database activity is one of the most effective ways to achieve these goals.
This guide explores Sybase’s capabilities for tracking database activity, dives into SQL techniques to enhance auditing processes, and highlights how advanced tools like DataSunrise can elevate security and compliance measures.
What Is Sybase Database Activity History?
Sybase database activity history encompasses the processes of recording, monitoring, and analyzing operations within the database. These operations include, but are not limited to, user logins, schema alterations, and data modifications. The benefits of maintaining a robust activity history include:
- Regulatory Compliance: Adhering to standards such as GDPR, HIPAA, and PCI-DSS mandates comprehensive audit logs.
- Security Enforcement: Tracking database events helps identify unauthorized access and detect anomalies.
- Operational Insights: Understanding user activity supports troubleshooting and facilitates accountability.
By leveraging Sybase’s native features and supplementary tools, organizations can establish a secure and efficient audit framework tailored to their needs.
Key Features for Sybase Database Activity Auditing
- Triggers: Automating the Audit Process
Triggers are database objects that automatically execute specified actions when certain events occur within a table. They are an invaluable tool for automating the collection of audit data.
Example: Monitoring Changes to a Key Table
To capture insertions, updates, and deletions in a critical table (e.g., Employees), you can define a trigger like this:
CREATE TRIGGER LogEmployeeChanges ON Employees FOR INSERT, UPDATE, DELETE AS BEGIN INSERT INTO AuditLog (event_type, user_id, timestamp, table_name) SELECT CASE WHEN EXISTS (SELECT * FROM inserted) AND EXISTS (SELECT * FROM deleted) THEN 'UPDATE' WHEN EXISTS (SELECT * FROM inserted) THEN 'INSERT' ELSE 'DELETE' END, SYSTEM_USER, GETDATE(), 'Employees'; END;
This trigger ensures that every modification to the Employees table is logged, providing critical information for audits and forensic investigations.
- Views: Streamlining Data Analysis
SQL views offer a convenient way to aggregate and filter audit data for quick analysis. By consolidating key information, views reduce the time and effort required to identify noteworthy events.
Example: Summarizing Audit Data
Create a view to highlight critical events such as updates, inserts, and deletes:
CREATE VIEW CriticalAuditSummary AS
SELECT event_time, username, event_type, object_name
FROM sybsecurity..sysaudits_01
WHERE event_type IN ('INSERT', 'UPDATE', 'DELETE');This view simplifies the task of identifying trends and pinpointing suspicious activities without wading through excessive details.
- Stored Procedures: Efficient Log Management
Stored procedures automate routine tasks, making the management of audit logs both scalable and efficient.
Example: Archiving Historical Logs
Here’s how you can archive older audit logs to maintain database performance:
CREATE PROCEDURE ArchiveAuditLogs AS BEGIN INSERT INTO AuditLogArchive SELECT * FROM AuditLog WHERE event_time < DATEADD(month, -6, GETDATE()); DELETE FROM AuditLog WHERE event_time < DATEADD(month, -6, GETDATE()); END;
This procedure ensures that logs older than six months are archived, preserving historical records without cluttering the active audit table.
Enhancing Sybase Auditing with DataSunrise
While Sybase’s built-in auditing tools are comprehensive, managing complex environments often demands advanced features. DataSunrise, a database security solution, enhances Sybase auditing by providing centralized monitoring, advanced analytics, and compliance tools.
Key Benefits of DataSunrise:
- Centralized Auditing: Manage multiple Sybase instances from a single interface.
- Real-Time Alerts: Respond to suspicious activity immediately.
- Detailed Reports: Generate customizable logs tailored to specific compliance requirements.
- Ease of Integration: DataSunrise integrates seamlessly with Sybase, minimizing setup complexity.

DataSunrise Dashboard displaying the status of proxies and their instances
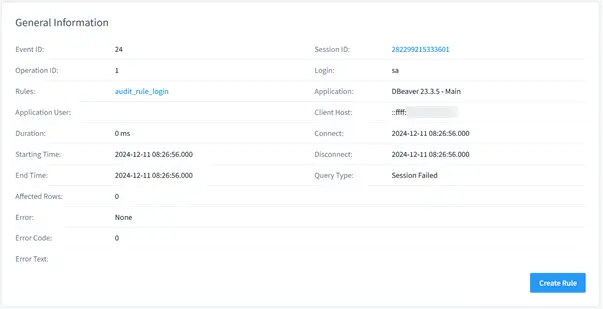
Example result of a login attempt audit rule
Setting Up DataSunrise for Sybase Auditing
- Connect to Sybase: Add your Sybase instance to the DataSunrise.
- Define Rules: Specify auditing rules, such as tracking failed login attempts or schema modifications.
- Analyze Logs: Use DataSunrise’s filtering capabilities to identify and review key events quickly.
Best Practices for Building a Comprehensive Audit Framework
To maximize the effectiveness of your Sybase auditing system, consider the following:
- Use Triggers: Automate data collection for critical tables.
- Leverage Views: Consolidate audit data into easily interpretable formats.
- Develop Stored Procedures: Streamline log management and reporting.
- Integrate Advanced Tools: Complement native Sybase capabilities with solutions like DataSunrise for enhanced monitoring and compliance.
Conclusion
Auditing Sybase database activity is essential for maintaining data security, meeting compliance requirements, and gaining operational insights. By utilizing triggers, views, and stored procedures, organizations can build a reliable and efficient audit framework. For those managing complex environments, integrating solutions like DataSunrise provides additional layers of functionality, including real-time monitoring, data masking, discovery and centralized control over all the security setup.
Start strengthening your database auditing strategy today. Visit the DataSunrise website to learn more and request an online demonstration. Equip your organization with the tools needed to ensure robust security and compliance in an ever-evolving digital landscape.
