Teradata Data Activity History
Introduction
In today’s data-driven world, maintaining a comprehensive Teradata Data Activity History is essential for ensuring database security and regulatory compliance. Organizations must track user activities, monitor data access, and detect potential security threats to protect sensitive information. Teradata, a leading data warehousing solution, offers robust native features to capture and analyze data activity history. Additionally, integrating advanced solutions like DataSunrise can further enhance your database security strategy. This article explores Teradata’s native capabilities for tracking data activity history and how DataSunrise can provide additional layers of security and flexibility.
Native Teradata Data Activity History
Teradata provides powerful native tools to track and log user activities, ensuring organizations can maintain a detailed Teradata Data Activity History. These logs are essential for monitoring user behavior, auditing access to sensitive data, and meeting compliance requirements. Below, we explore key features and examples of how to leverage Teradata’s logging capabilities.
Logging Privilege Checks
Teradata logs privilege checks in the DBC.AccLogTbl table
whenever a user attempts to access an object or perform an action. These logs
capture whether the privilege was granted or denied, providing a clear audit trail of user activity.
Example: Logging Privilege Checks for Specific Users
To log privilege checks for specific users, you can use the following command:
BEGIN LOGGING ON EACH ALL BY "admin1", "admin2"; This command logs all privilege checks for the users admin1 and admin2, ensuring their actions are tracked.
Querying Privilege Check Logs
To retrieve privilege check logs, you can query the DBC.AccLogTbl table:
SELECT LogonUser, ObjectName, AccessResult, AccessTime, SQLText
FROM DBC.AccLogTbl
WHERE LogonUser IN ('admin1', 'admin2');This query retrieves all privilege check logs for the specified users, helping you monitor their activity.
Logging Failed Access Attempts
Teradata allows you to log failed access attempts, which is crucial for identifying potential security breaches or unauthorized access attempts.
Example: Logging Denied Access Attempts
To log all denied access attempts, use the following command:
BEGIN LOGGING DENIALS ON EACH ALL;This command logs every denied access attempt across the system, providing visibility into potential security issues.
Logging Access to Audit Trails
Teradata allows you to log access to audit trails, ensuring that attempts to view or modify audit logs are themselves logged.
Example: Logging Access to Audit Trails
To log access to audit trails, use the following command:
BEGIN LOGGING ON EACH ALL ON TABLE DBC.AccessLogTbl;
BEGIN LOGGING ON EACH ALL ON VIEW DBC.AccessLogV; These commands log all access to the DBC.AccessLogTbl table and DBC.AccessLogV view, ensuring that audit trail access is tracked.
Querying Audit Trail Access Logs
To retrieve logs of access to audit trails, you can query the DBC.AccLogTbl table:
SELECT LogonUser, ObjectName, AccessResult, AccessTime, SQLText
FROM DBC.AccLogTbl
WHERE ObjectName IN ('DBC.AccessLogTbl', 'DBC.AccessLogV');This query retrieves all logs related to access to audit trails, helping you monitor who is viewing or modifying audit logs.
Example Output
Here’s an example of what the output might look like for a query retrieving administrative action logs:
| LogonUser | ObjectName | AccessResult | AccessTime | SQLText |
|---|---|---|---|---|
| admin1 | DBC.Users | Granted | 2023-10-01 10:00:00 | CREATE USER user1 |
| admin2 | DBC.Tables | Granted | 2023-10-01 10:05:00 | DROP TABLE table1 |
| admin1 | DBC.AccessLogTbl | Denied | 2023-10-01 10:10:00 | SELECT * FROM DBC.AccessLogTbl |
For more detailed information on setting up and managing activity logging in Teradata, you can refer to the official Teradata documentation.
Teradata Data Activity History with DataSunrise
While Teradata’s native capabilities are robust, integrating DataSunrise can provide additional layers of security and flexibility. DataSunrise is a comprehensive database security solution that enhances auditing, monitoring, and data masking capabilities across various database environments.
Real-Time Monitoring
DataSunrise offers real-time monitoring of database activities, enabling instant detection of unauthorized access attempts or suspicious activities. Additionally, it provides detailed insights into user behavior, helping organizations identify potential security risks.
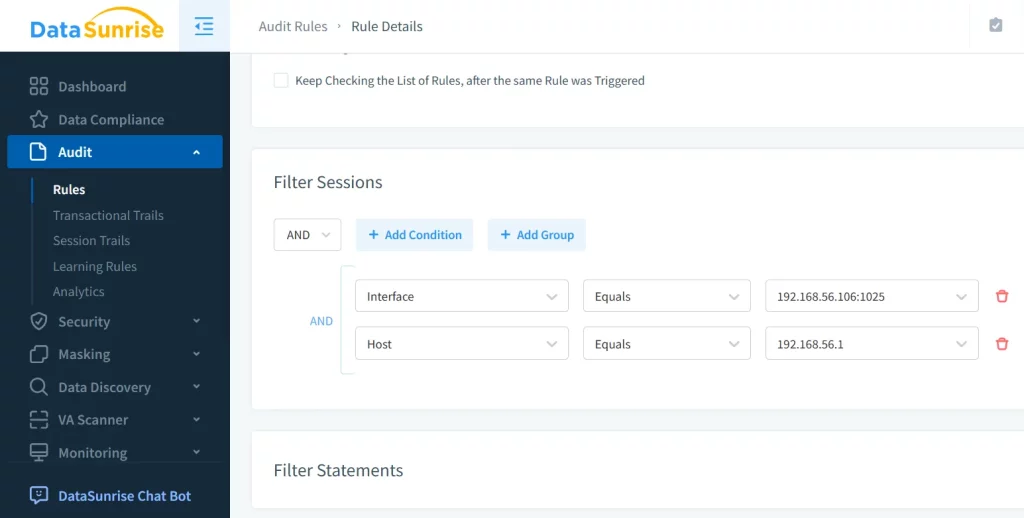
Customizable Audit Rules
With DataSunrise, you can create custom audit rules tailored to your specific compliance needs, such as GDPR or HIPAA. Furthermore, these rules can be granularly defined to monitor specific users, tables, or actions.
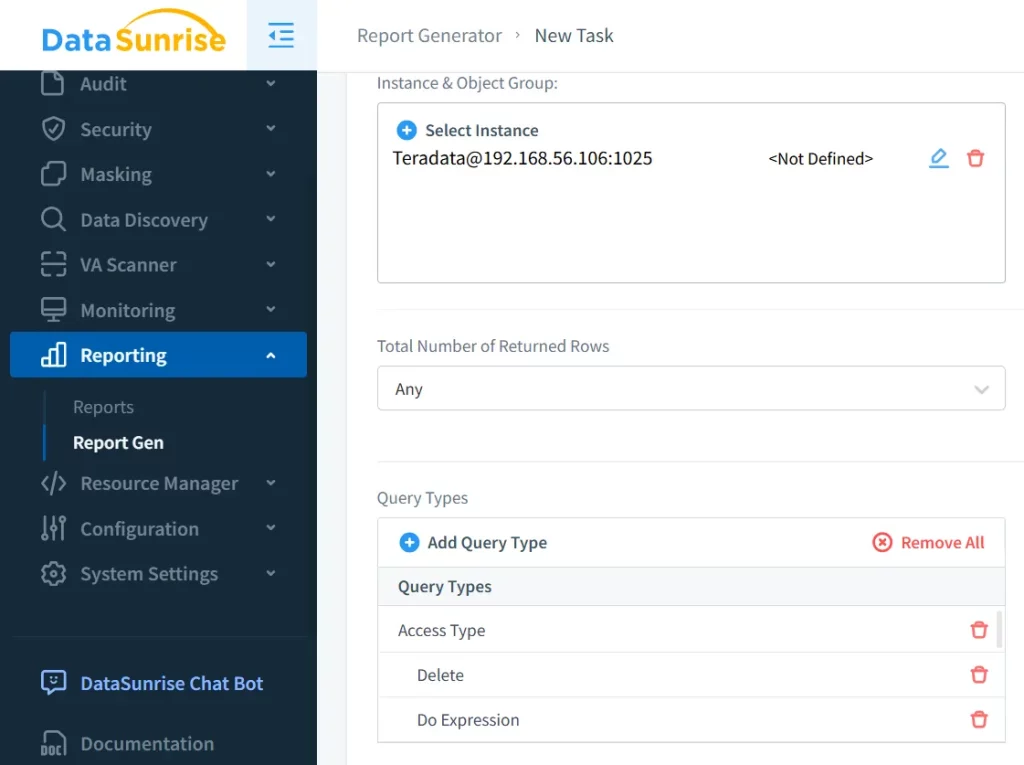
Advanced Reporting
DataSunrise generates detailed audit logs and visual dashboards, making it easier to analyze and interpret audit data. Moreover, these reports can be customized to meet specific regulatory requirements.
Automated Alerts
The platform sends real-time notifications on security incidents, enabling quick response to potential threats. In addition, these alerts can be configured to notify multiple stakeholders simultaneously.
Data Masking
DataSunrise offers dynamic data masking to protect sensitive data without affecting database functionality. Consequently, it ensures that sensitive information remains secure even when accessed by authorized users.
Conclusion
Maintaining a comprehensive Teradata Data Activity History is essential for ensuring the security and compliance of your data. While Teradata offers robust native features, integrating an advanced solution like DataSunrise can significantly enhance your database security strategy. From real-time monitoring to advanced reporting and compliance support, DataSunrise addresses the growing needs of modern businesses. Therefore, it is a valuable addition to any organization’s data security framework.
If you’re ready to elevate your database auditing capabilities, consider booking a personal demo or downloading DataSunrise trial today. A comprehensive and robust auditing solution is just a step away from fortifying your data security strategy.
