Teradata Data Audit Trail
Introduction
In today’s data-driven world, maintaining database security and integrity is crucial. The Teradata Data Audit Trail plays a vital role in monitoring and tracking database activities, ensuring compliance with regulatory standards and detecting security threats. While Teradata offers robust native auditing, integrating advanced solutions like DataSunrise can enhance your database security strategy.
Native Teradata Data Audit Trail
Teradata’s native auditing capabilities, through its Database Auditing Facility (DBAF), log a wide range of activities. This helps database administrators (DBAs) track user actions, monitor changes, and detect unauthorized access. These logs are essential for compliance with regulations like GDPR and HIPAA.
Setting Up Audit Rules
Teradata uses the BEGIN LOGGING statement to define logging rules, stored in the DBC.AccLogRuleTbl table. These rules determine which privilege
checks generate log entries in the DBC.AccLogTbl table.
1. Logging Specific Actions on a Table
To log actions like SELECT, INSERT, and UPDATE on a table, use:
BEGIN LOGGING ON EACH SELECT, INSERT, UPDATE ON TABLE "DatabaseName"."TableName";This ensures every operation on the specified table is logged, helping track data access and modifications.
2. Logging All Actions by a Specific Role
To log all actions by users with a specific role, use:
BEGIN LOGGING ON EACH ALL BY ROLE "RoleName";This logs every action by users in the specified role, useful for monitoring privileged roles.
Monitoring Administrative Actions
Administrative actions like creating or dropping databases, users, or tables are critical to monitor. Use:
BEGIN LOGGING ON EACH CREATE DATABASE, DROP DATABASE, CREATE USER, DROP USER
ON DATABASE "DBC"; This logs all CREATE and DROP operations, ensuring
administrative actions are tracked.
Querying System Views for Enhanced Auditing
Teradata provides system views like DBC.AccessLogV for detailed
auditing. For example:
SELECT LogonUser, ObjectName, AccessResult, AccessTime, SQLText
FROM DBC.AccessLogV
WHERE AccessResult = 'Denied'
AND AccessTime > CURRENT_DATE - 7; This retrieves denied access attempts in the last seven days. Similarly, use DBC.LogOnOffV to monitor logon activities:
SELECT LogDate, LogTime, UserName, Event
FROM DBC.LogOnOffV
WHERE Event LIKE '%Failed%'
AND LogDate > CURRENT_DATE - 30;This returns failed logon attempts in the last 30 days.
Logging Access to Sensitive Data
To comply with regulations like PCI-DSS, log access to sensitive data:
BEGIN LOGGING ON EACH SELECT, INSERT, UPDATE, DELETE
ON TABLE "SensitiveDatabase"."SensitiveTable";This logs all access attempts to the specified sensitive table.
Logging System-Level Object Changes
To log changes to system-level objects, use:
BEGIN LOGGING ON EACH CREATE TABLE, DROP TABLE, CREATE VIEW, DROP VIEW
ON DATABASE "DBC"; This logs all CREATE and DROP operations on tables
and views. To eplore more data audit trail options in teradata, consult the Teradata documentation.
Enhancing Teradata Data Audit Trail with DataSunrise
While Teradata’s native auditing is robust, integrating DataSunrise enhances database security and compliance.
How DataSunrise Strengthens Teradata Auditing
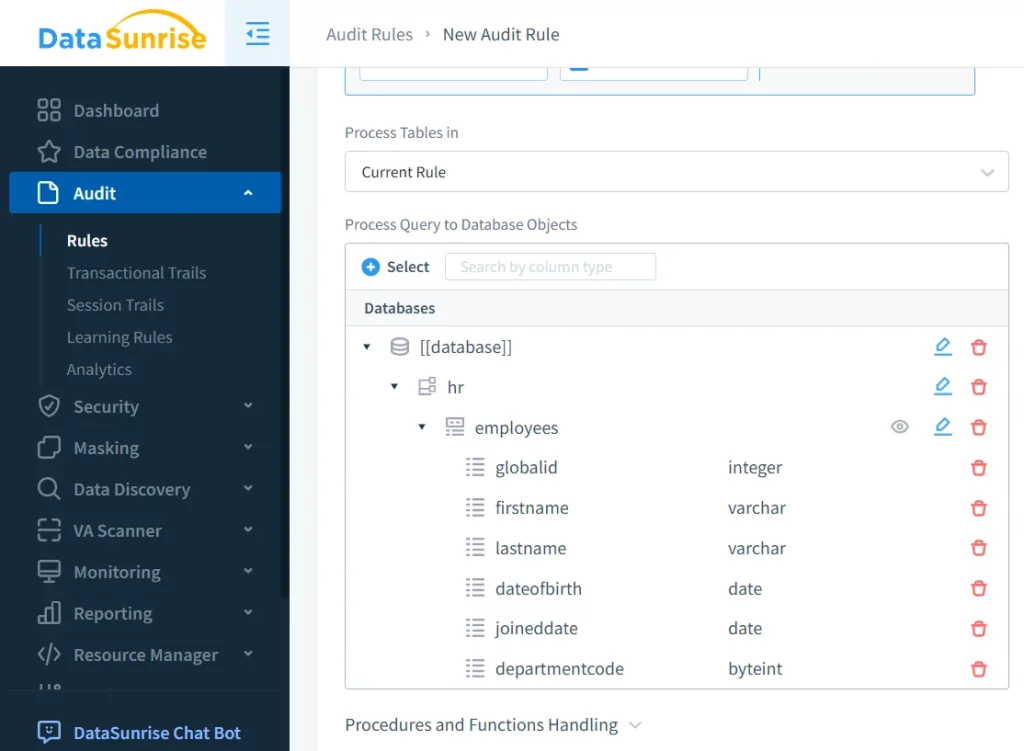
1. Customizable Audit Rules for Compliance
DataSunrise allows granular audit rules tailored to regulations like GDPR or HIPAA. These rules monitor specific users, tables, or actions, ensuring compliance.
2. Real-Time Monitoring and Alerts
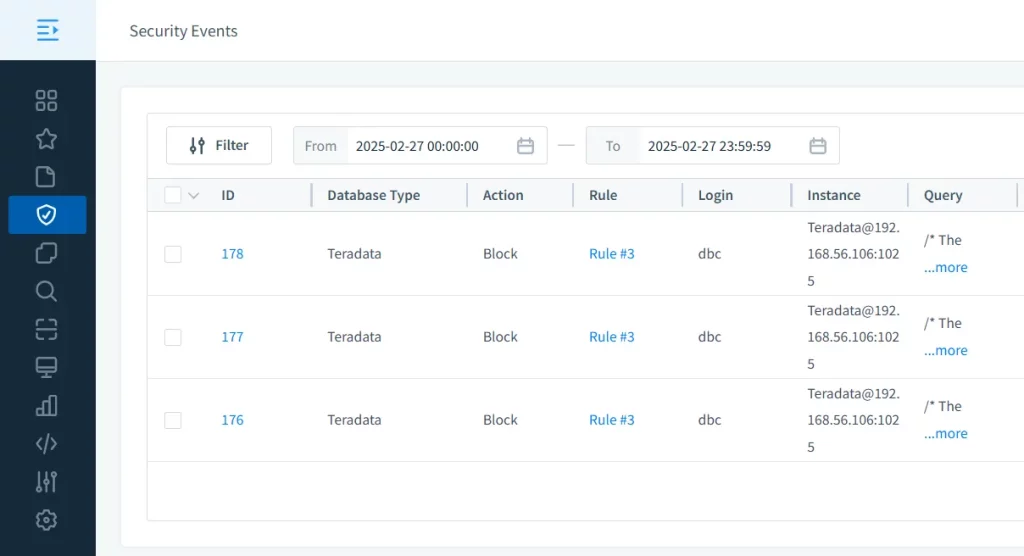
DataSunrise provides real-time monitoring, detecting unauthorized access or suspicious behavior. Automated alerts notify stakeholders of potential security incidents.
3. Advanced Reporting and Dashboards
DataSunrise generates comprehensive audit logs and visual dashboards, simplifying audit data analysis. Reports can be customized to meet regulatory or organizational needs.
4. Dynamic Data Masking for Sensitive Data
DataSunrise offers dynamic data masking, obscuring sensitive data from unauthorized users while maintaining database functionality.
5. Proactive Threat Detection
Combining real-time monitoring with customizable rules and alerts, DataSunrise enables proactive threat detection, addressing risks before they escalate.
Why Choose DataSunrise for Teradata?
DataSunrise enhances Teradata’s native auditing and provides a unified solution for data security, compliance, and monitoring. Its flexibility and advanced features make it invaluable for strengthening data protection strategies.
Conclusion
A thorough Teradata Data Audit Trail is essential for data security and compliance. While Teradata offers robust native auditing, integrating DataSunrise significantly enhances your database security strategy. From real-time monitoring to advanced reporting, DataSunrise addresses modern business needs, making it a valuable addition to any data security framework.
Elevate your database auditing capabilities by booking a personal demo or downloading DataSunrise trial today. A comprehensive auditing solution is just a step away from fortifying your data security strategy.
