Teradata Database Activity History
Introduction
In today’s data-driven world, maintaining a comprehensive Teradata Database Activity History is essential for ensuring database security and regulatory compliance. By tracking and analyzing user activities, organizations can detect potential threats, enforce security policies, and meet compliance requirements. Teradata, a leading data warehousing solution, provides robust native capabilities for monitoring database activities. However, to achieve a more advanced and flexible solution, integrating tools like DataSunrise can significantly enhance your database security strategy. Consequently, businesses can gain better control over their database security.
Native Teradata Database Activity History
Teradata provides robust native features for tracking and logging database
activities, enabling organizations to monitor user actions, detect
unauthorized access attempts, and maintain compliance with regulatory
requirements. The Teradata Database Activity History is
primarily managed through system views and tables, such as DBC.AccessLogV and DBC.LogOnOffVX, which offer
detailed insights into user activities and access patterns. Therefore,
leveraging these system views can help strengthen database security.
Monitoring Logon and Logoff Activities
By default, Teradata logs all user logon and logoff attempts in the DBC.LogOnOffVX view. This view provides critical information
about user sessions, including successful and unsuccessful logon attempts,
session duration, and the source of the logon. For example, to retrieve a list
of failed logon attempts in the last seven days, you can use the following
query:
SELECT LogDate, LogTime, UserName, Event
FROM DBC.LogOnOffVX
WHERE Event NOT LIKE ('%Logo%') AND LogDate > DATE - 7
ORDER BY LogDate, LogTime;Example LogOnOff Table Output
This query helps identify potential security threats, such as brute-force attacks or unauthorized access attempts. Consequently, organizations can take proactive measures to mitigate risks. The output might look like this:
| LogDate | LogTime | UserName | Event |
|---|---|---|---|
| 2023-10-01 | 08:55:22 | Non-existent User | Auth Failed |
| 2023-10-05 | 09:30:15 | user1 | Bad Account |
Tracking Privilege Checks with Access Logs
Teradata’s DBC.AccessLogV view records the results of privilege
checks performed on user requests. This view is particularly useful for
auditing user actions and ensuring compliance with security policies.
Therefore, organizations can utilize it for comprehensive security monitoring.
For example, to track all privilege checks for a specific user, you can run:
SELECT UserName, LogDate, LogTime, StatementText, AccessResult
FROM DBC.AccessLogV
WHERE UserName = 'DBADMIN'
ORDER BY LogDate, LogTime;
Example Access Log Table Output
This query retrieves all privilege checks for the user DBADMIN,
showing whether access was granted or denied. Consequently, administrators can
ensure that access policies are enforced effectively. The output might
include:
| UserName | LogDate | LogTime | StatementText | AccessResult |
|---|---|---|---|---|
| DBADMIN | 2023-10-01 | 10:00:00 | SELECT * FROM sensitive_table | Granted |
| DBADMIN | 2023-10-01 | 10:05:00 | DROP TABLE sensitive_table | Denied |
Compliance and Regulatory Requirements
Teradata’s native logging capabilities support compliance with various regulatory standards, such as PCI-DSS and Sarbanes-Oxley. Additionally, organizations can implement advanced logging techniques to enhance compliance further. For example, to log all unsuccessful access attempts, you can use:
BEGIN LOGGING DENIALS ON EACH ALL;This command logs all denied access attempts, helping organizations meet regulatory requirements for tracking unauthorized access. Consequently, businesses can demonstrate their commitment to data security.
For more detailed information on setting up and managing activity logging, refer to the official Teradata documentation.
Enhancing Activity History with DataSunrise
While Teradata’s native capabilities are robust, integrating DataSunrise can provide additional layers of security and flexibility. Consequently, businesses can strengthen their database activity monitoring framework.
Key Features of DataSunrise for Activity History
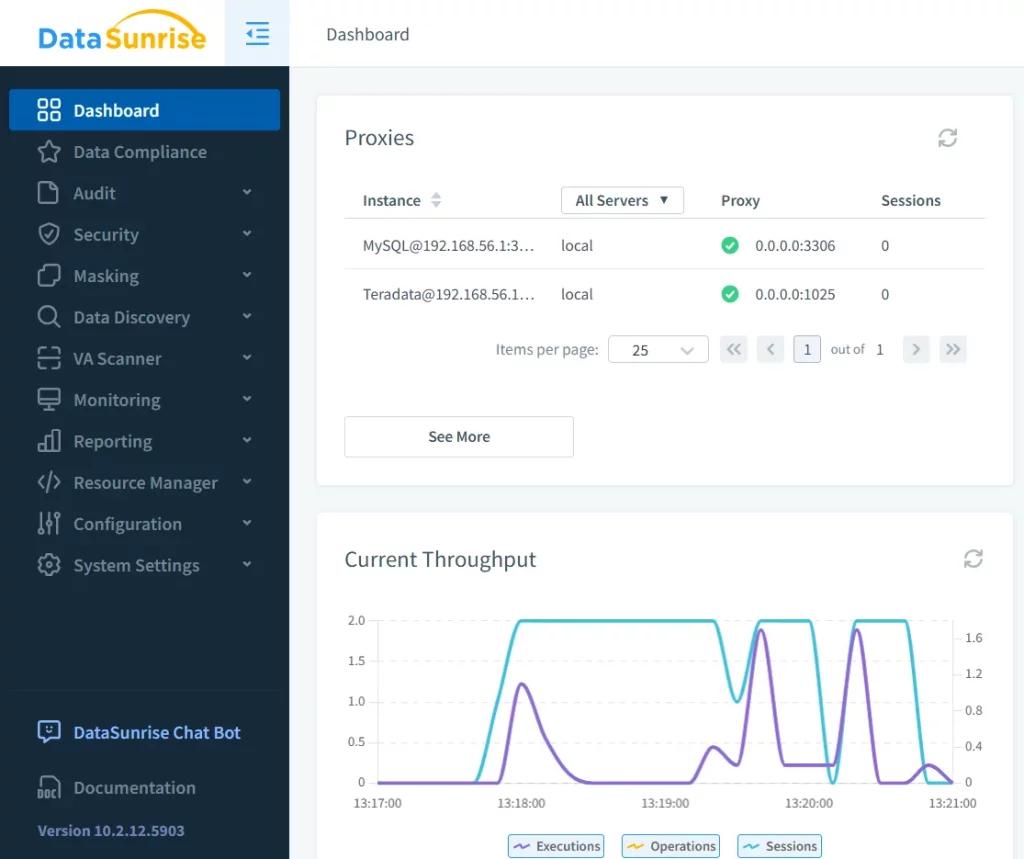
1. Real-Time Monitoring
DataSunrise offers real-time monitoring of database activities, enabling instant detection of unauthorized access attempts or suspicious activities. Additionally, it provides detailed insights into user behavior, helping organizations identify potential security risks. Therefore, security teams can act swiftly in response to threats.
2. Customizable Activity Logging
With DataSunrise, you can create custom logging rules tailored to your specific compliance needs, such as GDPR or HIPAA. Furthermore, these rules can be granularly defined to monitor specific users, tables, or actions. Consequently, compliance processes become more efficient.
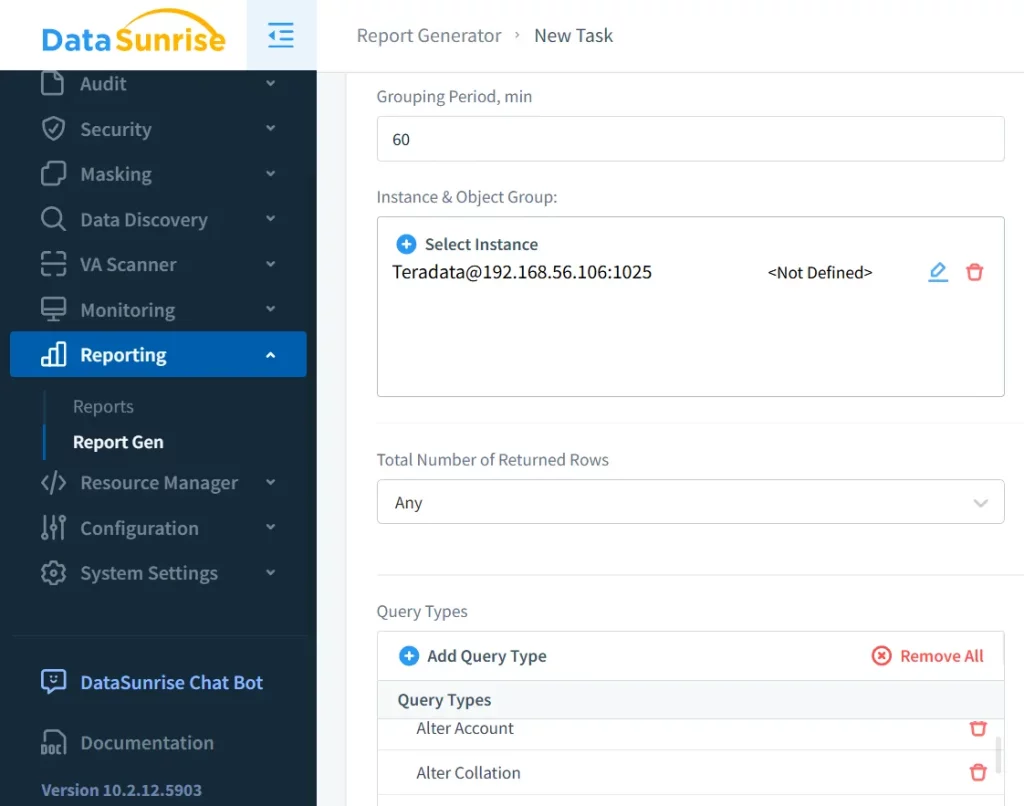
3. Advanced Reporting
DataSunrise generates detailed activity logs and visual dashboards, making it easier to analyze and interpret activity data. Moreover, these reports can be customized to meet specific regulatory requirements. Consequently, organizations gain deeper insights into their security landscape.
Conclusion
Maintaining a comprehensive Teradata Database Activity History is essential for ensuring database security and compliance. While Teradata offers robust native capabilities, integrating an advanced solution like DataSunrise can significantly enhance your database security strategy. Therefore, businesses should consider leveraging both for maximum protection.
If you’re ready to elevate your database activity monitoring capabilities, consider booking a personal demo or downloading DataSunrise trial today. Consequently, taking this step will ensure your data security strategy remains strong and effective.
