
What is CockroachDB Audit Trail

In today’s data-driven landscape, organizations face mounting pressure to protect their data assets. According to the World Economic Forum’s 2024 Global Cybersecurity Outlook, 43% of cyber leaders prioritize preventing unauthorized database access, making robust audit trail implementation essential for modern database systems like CockroachDB.
CockroachDB, known for its distributed SQL architecture and exceptional scalability, provides organizations with the tools needed to implement comprehensive audit trails. While CockroachDB offers native auditing capabilities, many enterprises require more sophisticated solutions to meet their compliance regulations and security requirements.
In this article, you’ll discover what constitutes a CockroachDB audit trail, explore its native auditing capabilities, and learn how DataSunrise can enhance your database security posture through advanced monitoring and protection features.
Understanding CockroachDB Audit Trail
A CockroachDB audit trail is a systematic record of all database activities, providing a chronological log of operations performed on your database. It documents who accessed the database, what actions they performed, and when these activities occurred. This comprehensive data activity history serves multiple purposes:
- Security Monitoring: Tracking unauthorized access attempts and suspicious activities
- Compliance Documentation: Meeting regulatory requirements for data governance
- Incident Investigation: Providing forensic evidence in case of security threats
- Operational Insights: Understanding usage patterns and performance bottlenecks
Unlike some database systems with built-in audit logging, CockroachDB requires administrators to implement custom solutions using its SQL features, system tables, and transaction logs to create effective audit logs.
Native CockroachDB Audit Trail Capabilities
CockroachDB provides several methods for implementing audit trails through its native features. While not as comprehensive as dedicated audit systems, these capabilities offer a foundation for basic monitoring and compliance needs.
1. Using SQL-Based Audit Tables
One of the most common approaches to creating a CockroachDB audit trail is establishing custom audit tables. Here’s an example implementation:
CREATE TABLE cockroach_audit_trail ( audit_id UUID DEFAULT gen_random_uuid() PRIMARY KEY, timestamp TIMESTAMPTZ DEFAULT current_timestamp(), user_name STRING NOT NULL, action_type STRING NOT NULL, table_name STRING, query_text STRING, INDEX (timestamp DESC), INDEX (user_name), INDEX (table_name) );
This table structure captures essential audit information, including:
- User identification
- Action performed (SELECT, INSERT, UPDATE, DELETE)
- Affected database objects
- Query text for analysis
2. Implementing Triggers for Automatic Audit Logging
To automate the database activity history process, you can create triggers that populate the audit table whenever changes occur in monitored tables:
CREATE FUNCTION record_audit_data() RETURNS TRIGGER AS $$
BEGIN
IF (TG_OP = 'INSERT') THEN
INSERT INTO cockroach_audit_trail (
user_name, action_type, table_name, query_text
) VALUES (
current_user, 'INSERT', TG_TABLE_NAME, current_query()
);
ELSIF (TG_OP = 'UPDATE') THEN
INSERT INTO cockroach_audit_trail (
user_name, action_type, table_name, query_text
) VALUES (
current_user, 'UPDATE', TG_TABLE_NAME, current_query()
);
ELSIF (TG_OP = 'DELETE') THEN
INSERT INTO cockroach_audit_trail (
user_name, action_type, table_name, query_text
) VALUES (
current_user, 'DELETE', TG_TABLE_NAME, current_query()
);
END IF;
RETURN NULL;
END;
$$ LANGUAGE plpgsql;
-- Apply trigger to sensitive table
CREATE TRIGGER user_data_audit
AFTER INSERT OR UPDATE OR DELETE ON user_data
FOR EACH ROW EXECUTE FUNCTION record_audit_data();
3. Creating Audit Views for Analysis
To simplify audit trail analysis, you can create specialized views that filter and organize audit data for specific security policies use cases:
-- View for suspicious activities
CREATE VIEW suspicious_audit_events AS
SELECT
timestamp,
user_name,
action_type,
table_name,
SUBSTRING(query_text, 1, 50) AS query_preview
FROM
cockroach_audit_trail
WHERE
(action_type = 'DELETE' AND table_name IN ('users', 'permissions', 'financial_data'))
OR (timestamp BETWEEN '2024-02-01' AND '2024-02-15' AND table_name = 'sensitive_info')
OR (user_name NOT IN (SELECT username FROM authorized_users));
This view automatically filters audit records to highlight potential security concerns, such as deletions from critical tables or access by unauthorized users.
4. Using the CockroachDB Web UI for Monitoring
CockroachDB’s web-based administrative interface provides additional monitoring capabilities that complement custom audit trails:
- Access the CockroachDB Admin UI (typically at http://localhost:8080)
- Navigate to the “SQL Activity” dashboard
- Monitor active sessions, query statistics, and transaction metrics
- Review statement execution history for suspicious patterns
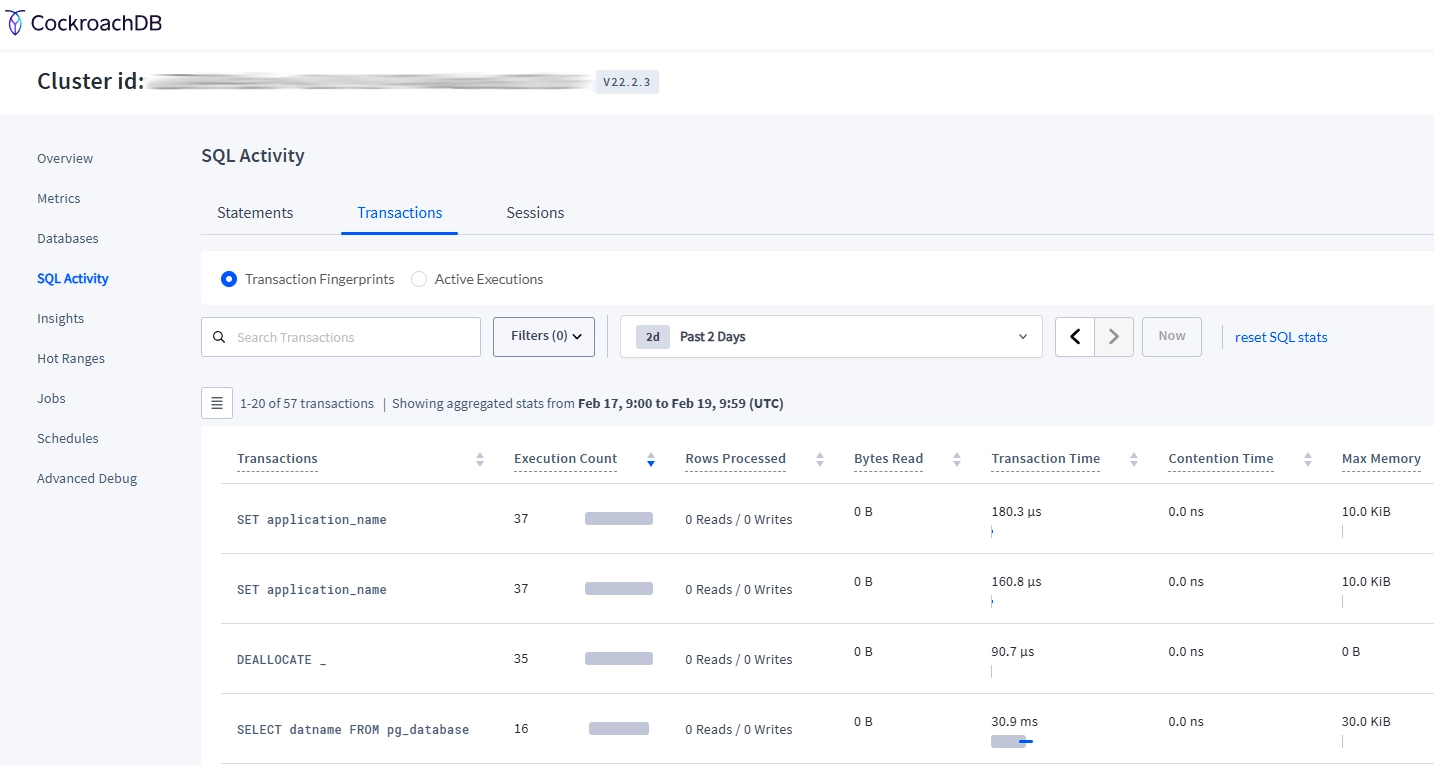
While the web UI doesn’t provide a comprehensive audit trail, it offers valuable real-time insights into database activity monitoring that can supplement your custom audit implementation.
Limitations of Native CockroachDB Audit Capabilities
Despite offering foundational audit capabilities, CockroachDB’s native features have several limitations that may challenge organizations with advanced security requirements:
| Limitations | Impact |
|---|---|
| Manual implementation required | Increases setup complexity and maintenance burden |
| Limited real-time alerting | Delays detection of suspicious activities |
| Basic reporting capabilities | Complicates compliance documentation |
| Performance considerations | May impact database operations if not optimized |
| No built-in audit encryption | Requires additional security measures for audit data |
For organizations requiring robust security monitoring, compliance manager, and advanced threat detection, these limitations necessitate exploring enhanced audit trail solutions.
Enhanced CockroachDB Audit Trail with DataSunrise
While CockroachDB’s native capabilities provide a foundation for basic audit requirements, DataSunrise offers a comprehensive security suite that significantly enhances CockroachDB audit trail functionality through advanced monitoring, protection, and compliance features.
Setting Up DataSunrise for CockroachDB Audit Trail
Implementing DataSunrise with CockroachDB involves a straightforward process:
1. Connect to CockroachDB
Begin by connecting DataSunrise to your CockroachDB instance through the intuitive dashboard interface.
2. Configure Audit Rules
Create customized rules priority to specify which database activities should be monitored.
3. Monitor Audit Trails
Access comprehensive, detailed audit logs through DataSunrise’s transactional trails interface.
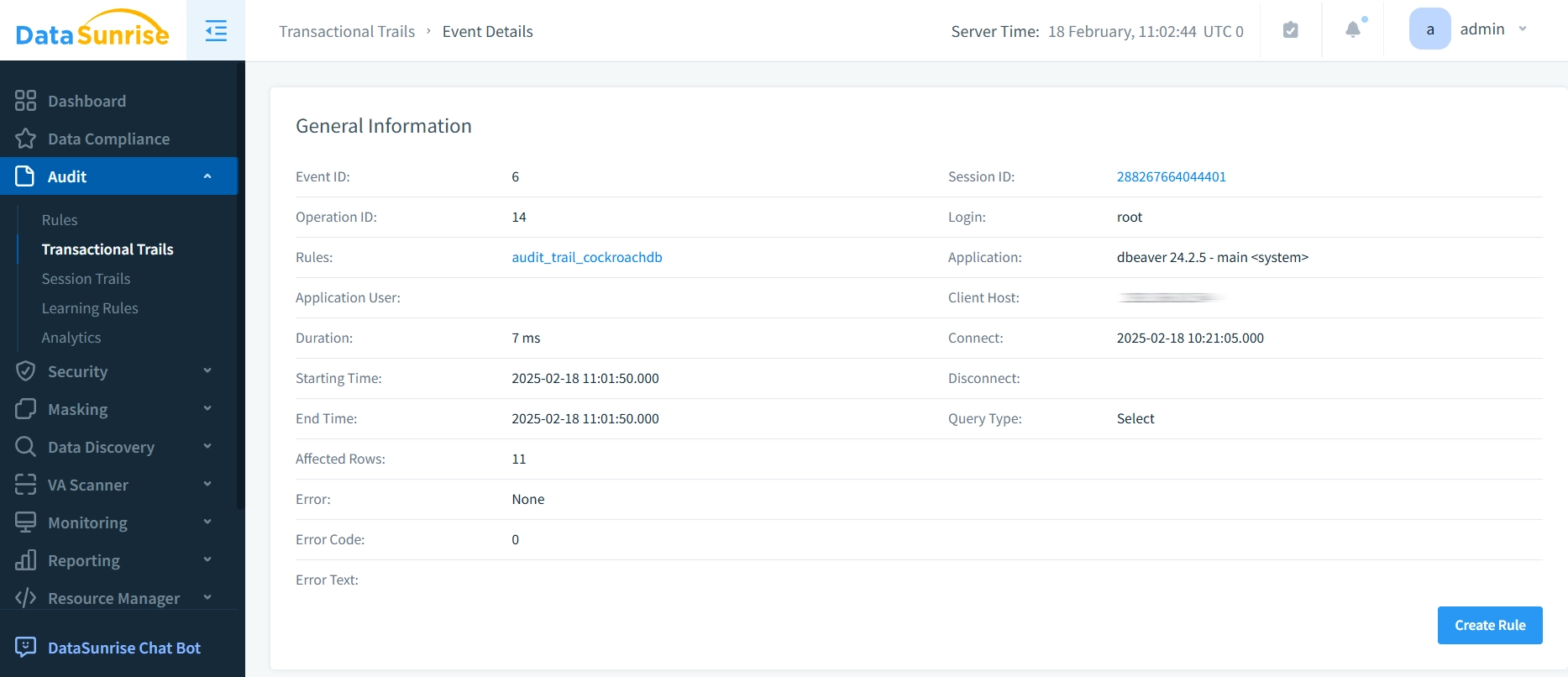
Key Advantages of DataSunrise for CockroachDB Audit Trail
DataSunrise extends CockroachDB’s native audit capabilities with advanced features designed for enterprise-grade security and compliance:
- Comprehensive Audit Guide: Define granular policies based on users, operations, objects, and time periods to capture precisely the audit data you need.
- Learning Rules and Audit: Continuous observation of database activities with immediate alerts for suspicious events, enabling proactive security management.
- User Behavior Analysis: AI-powered analysis of access patterns to detect anomalies and potential security threats before they escalate.
- Dynamic Data Masking: Protect sensitive information in audit trails while maintaining visibility for authorized personnel.
- Automated Compliance Reporting: Pre-built report templates for GDPR, HIPAA, SOX, and PCI DSS requirements that simplify regulatory documentation.
- Multi-Platform Support: Unified interface for managing audit policies across multiple database instances, ensuring consistent security practices.
Best Practices for CockroachDB Audit Trail Implementation
Implementing an effective audit trail for CockroachDB requires attention to several key areas:
1. Performance Optimization
- Selective Logging: Audit only essential activities to minimize performance impact
- Index Management: Create appropriate indexes on audit tables for efficient queries
- Batch Processing: Consider asynchronous audit logging for high-volume environments
- Storage Planning: Implement automatic archiving of older audit records to maintain performance
2. Security Implementation
- Access Controls: Restrict access to audit logs using RBAC
- Database Encryption: Encrypt audit data both at rest and in transit
- Principle of Least Privilege: Ensure audit administrators cannot modify the logs they oversee
- SQL Injection Protection: Implement mechanisms to detect unauthorized modifications to audit data
3. Compliance Management
- Retention Policies: Define clear retention periods based on regulatory requirements
- Documentation: Maintain detailed records of audit configurations and procedures
- Regular Validation: Periodically test audit log completeness and accuracy
- Chain of Custody: Establish clear protocols for handling audit data during investigations
4. Monitoring and Analysis
- Audit Goals: Establish scheduled audit log review procedures
- Slack Notifications: Configure real-time alerts for suspicious activities
- Baseline Establishment: Define normal behavior patterns to identify anomalies
- Report Generation: Create dashboard visualizations for security metrics and compliance status
5. Third-Party Solution Integration
- DataSunrise Firewall: Implement specialized security tools to enhance audit capabilities
- Vulnerability Assessment: Utilize unified platforms to manage protection across multiple databases
- MS Teams Notifications: Configure additional alert channels for security events
- LLM and ML Tools: Take advantage of advanced analytics for detecting emerging threats
Conclusion
A well-implemented CockroachDB audit trail is essential for maintaining database security, ensuring regulatory compliance, and supporting operational excellence. While CockroachDB’s native features provide a foundation for basic audit requirements, organizations with advanced security needs benefit from comprehensive solutions like DataSunrise.
DataSunrise Overview extends CockroachDB’s audit capabilities through real-time monitoring, sophisticated behavioral analytics, and automated compliance reporting. This integrated approach addresses the full spectrum of modern database security challenges while maintaining performance and operational efficiency.
Ready to enhance your CockroachDB security posture with advanced audit trail capabilities? Schedule a demonstration to see how DataSunrise can strengthen your database security and simplify compliance management.
