What is Non-Human Identity Security?
Your browser uses an encrypted connection with the server as you read this. There are numerous algorithms and methods that authorize your application on the server, often without you noticing. As a result, in today’s digital landscape, securing systems has become more complex, driven in part by the rapid rise of non-human identities.
As organizations adopt cloud services, automation, and LLM APIs, non-human identities — such as applications, APIs, bots, and services — play a pivotal role in day-to-day operations. Protecting these non-human identities is essential for securing sensitive data and preventing unauthorized access. One of the biggest challenges? Securing the API keys, tokens, and certificates used to authenticate and authorize these non-human identities.
In this article, we’ll explore the concept of non-human identity security, why it is crucial to protect API keys and tokens, and how tools like Data Security Posture Management (DSPM) can help organizations achieve this. With the rise of non-human identities, the stakes for data protection have never been higher.
What are API Keys or Tokens?
API keys and tokens are sensitive pieces of information used to authenticate and authorize access to services or systems. While they are not classified as personally identifiable information (PII) and are not yet protected under PII laws, they can still lead to significant data breaches if compromised. Here are a few examples of how these breaches can occur – hardcoding in public repositories (instead of environment variables), insufficient access control. The identity may look as follows:
Claude (Anthropic) API Key:
sk-ant-api03-ZGTFrtwQiHEhvUgP2BXgcNt10uf81TQ4pMf7p7S68zgjq25T...wCPAn9z-xgQgY...mMUoMHDDLpYpc1LfVsw-RPJ4rQYY
Open AI API Key:
sk-prod-jt5s1gettW5fxb4tU0DoWYk3Ztk3PESY8o9aBGdkb774ZuvXF...Edfd5NJmyyB8CLy_qpvWT3BlbkFJs9q9gws8SpFKAgmBm4hNwjRx-P167Vz0AzZYC8d5L0xuRMUdeIkCXAzki2KH5HOJ4ymXE3WqHH
Gemini (Google) API Key:
AIzaSyCR-xaBewyL8pl2FEhPc8CrdVFVykxfTSF
Google API OAuth secret key and token:
{"installed":{"client_id":"1097288213321-fduqo786hj08l...thd3qb7f76jiss.apps.googleusercontent.com","project_id":"gdoctohtml","auth_uri":"https://accounts.google.com/o/oauth2/auth","token_uri":"https://oauth2.googleapis.com/token","auth_provider_x509_cert_url":"https://www.googleapis.com/oauth2/v1/certs","client_secret":"GOSSPD-P6UhBjk...pEHgsY8Lw7SyhXN","redirect_uris":["http://localhost"]}}{"token": "ya29.a0ARW5m76GtzrP_VhAnukHEln2djhL511b...jn3JJxvPtajABY7es8TRUdKo9xE9ChSqYdnpY0eIZS2kNMKZVanon3Wz_lCvi6cldPGMCZitPjHP2WFq2r1RfJHt79PCibBVGDRAnxEiAEFmMSUJNpesTnE70B3mulh37XwAaCgYKARcSARISFQHTR2MiYLt3zOncChX3MdLlZuBQ3Q0177", "refresh_token": "1//09v7feFBmpvamCgYIARAAGAkSNwF-L9IrfujY0gCsx84I3...fNgs8pGsNkYzhNylYCtXiGqniCc7YbVMorIDc2DsCZeBSsSbOx0", "token_uri": "https://oauth2.googleapis.com/token", "client_id": "1097288213458-fduqo87al708lsl3opkhd3qb7f76jiss.apps.googleusercontent.com", "client_secret": "GOSSPD-P6UhBjkT7...gsY8Lfewo7SyhXN", "scopes": ["https://www.googleapis.com/auth/documents.readonly"], "universe_domain": "googleapis.com", "account": "", "expiry": "2024-12-25T12:41:12.781910Z"}Why is Non-Human Identity Security Critical?
Non-human identities often have extensive access to resources. These identities are used to run automation tasks, interact with databases, and even make decisions. Unlike human identities, these identities typically use API keys, OAuth tokens, and certificates for authentication. The misuse of these credentials can result in significant damage, as they often have broad access and control over resources. Therefore, protecting these keys and tokens is paramount.
The Rise of Non-Human Identities
The shift to cloud computing, microservices, and APIs has fueled the rise of non-human identities. Applications communicate with each other more frequently than ever, exchanging data and performing tasks without human intervention. As a result, the number of API calls and automated workflows has skyrocketed. In fact, non-human identities often outnumber human ones.
But with this rise comes increased security risks. Non-human identities rely on API keys, tokens, and certificates for authentication and authorization. If compromised, these credentials can be used to steal data, disrupt services, or launch further attacks. Organizations must prioritize non-human identity security to prevent these threats.
What is Non-Human Identity Security?
Non-human identity security refers to the process of discovering, securing, and managing the credentials used by non-human entities, such as applications, services, APIs, and bots. Unlike human users, non-human identities don’t log in with a username and password. Instead, they use API keys, OAuth tokens, and certificates to authenticate and interact with other systems.
The primary focus of non-human identity security is to:
- Discover non-human identities and the credentials they use.
- Protect API keys, tokens, and certificates from being compromised.
- Monitor usage and detect any suspicious activity.
Discovery: Finding Sensitive Non-Human Data
One of the biggest challenges in securing non-human identities is discovery. Many organizations have non-human identities scattered across their systems and cloud environments. These identities often go unnoticed, making them prime targets for attackers.
The first step in non-human identity discovery is to identify all the API keys, tokens, and certificates in use. This can be a daunting task, especially in cloud environments where applications interact with numerous services. Additionally, these credentials are often hard-coded into applications or stored in insecure locations, increasing the risk of exposure.
Automated discovery tools can help organizations locate and inventory these credentials. Once identified, it’s essential to ensure that they are properly protected, encrypted, and rotated regularly to prevent unauthorized access.
Discovery Automation with General Tools
Methods for token or API key discovery depend on the token’s character set. As seen in the examples below, entropy peaks when the analysis window spans the token characters.
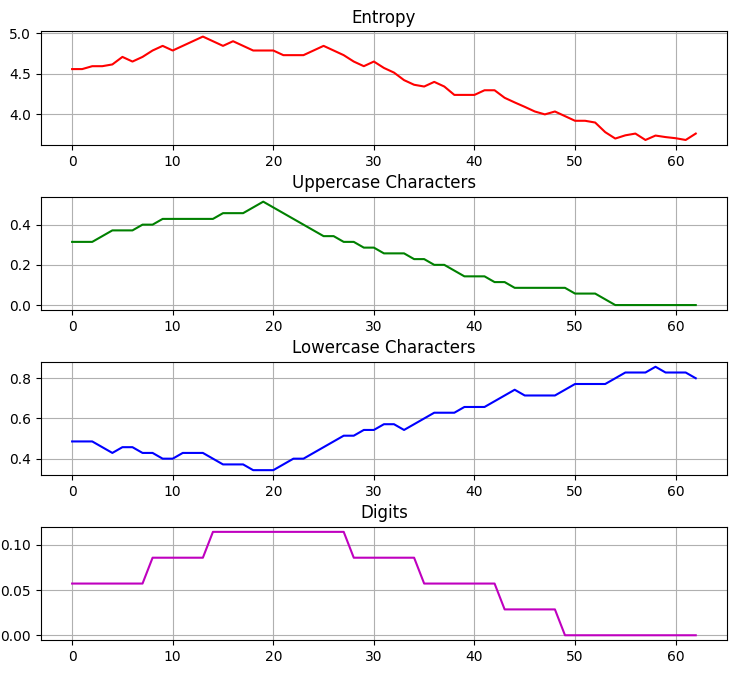
For most API keys, the frequency of uppercase, lowercase, and digit characters should be roughly equal when the sliding test window fully covers the key sequence.
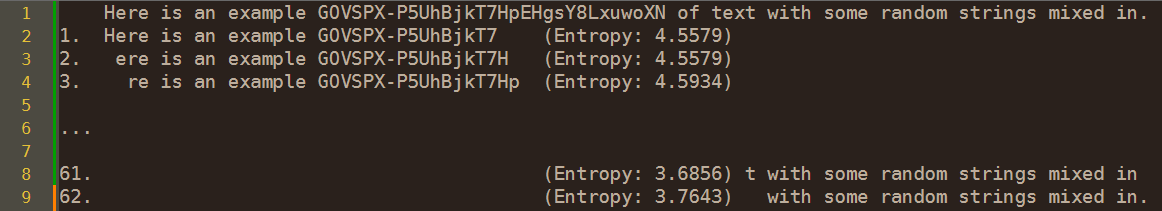
Additionally, regular expression approaches and direct searches are viable methods. While they are simple to implement, they require exact matches. This limitation can be mitigated by using variable symbol counters (‘{10,25}’ in the next example).
import re
# Example pattern for API keys (adjust as per your environment)
api_key_pattern = r"[A-Z0-9]{10,25}(-[A-Z0-9]{10,25})?"
text = "Here is a possible API key: GOVSPX-P0hBjkT7Hp and some junk: ABC123."
matches = re.findall(api_key_pattern, text)
print(matches)This should output:
'GOVSPX-P0hBjkT7Hp'
DataSunrise offers extensive options for defining regular expressions to match both structured and unstructured data. You can flexibly and consistently define Information Types and their Attributes, centralizing them for all potential API key or token variants.
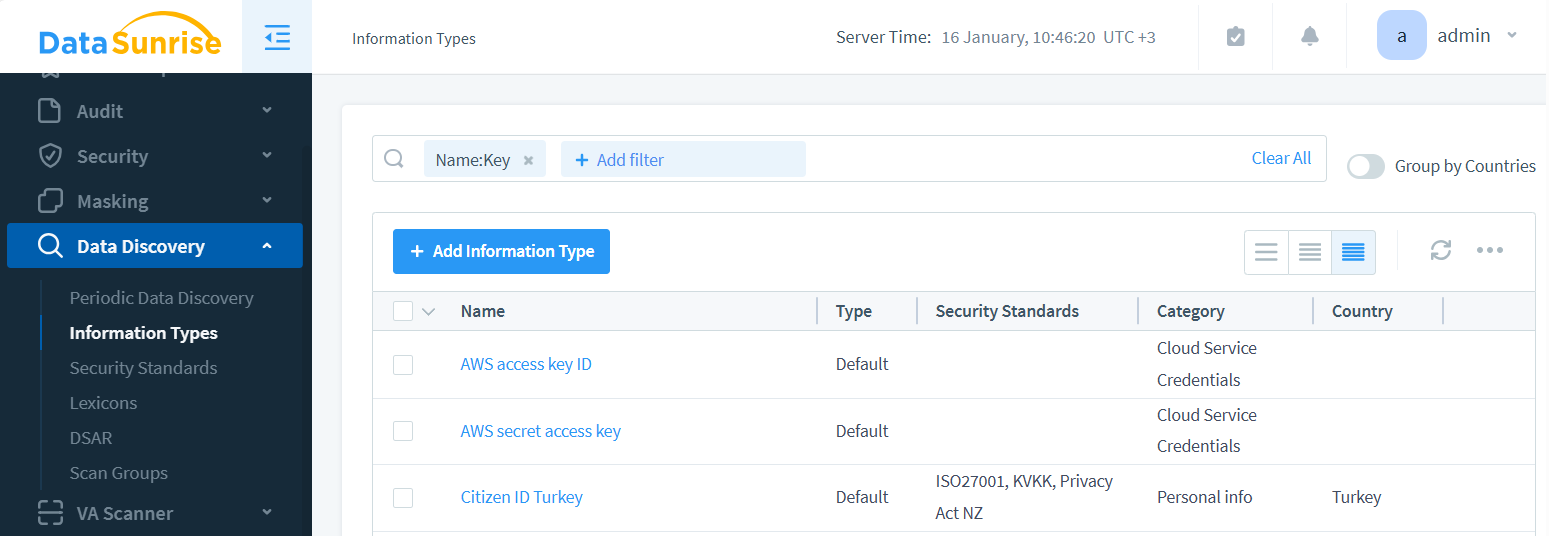
Securing API Keys and Tokens
Once the non-human identities and their associated credentials have been discovered, the next step is to secure them. API keys, tokens, and certificates are like passwords for non-human entities. If an attacker gains access to them, they can impersonate the application or service and gain unauthorized access to critical systems.
There are several best practices for securing API keys and tokens:
- Store keys securely: Avoid storing keys and tokens in code repositories or plain-text files. Instead, use secure storage solutions such as secret management systems.
- Encrypt sensitive data: Ensure that all keys, tokens, and certificates are encrypted at rest and in transit.
- Rotate keys regularly: Implement regular key rotation to minimize the risk of long-lived credentials being compromised. Most cloud providers offer centralized credential management (AWS example), where you can establish appropriate rotation policies.
- Limit access: Apply the principle of least privilege by restricting the permissions granted to API keys and tokens.
Protecting Non-Human Identity with Masking
Masking is another technique commonly used to protect sensitive non-human credentials. Specifically, data masking involves obfuscating sensitive data so that it’s hidden from unauthorized users, while still allowing the system to function normally. Masking can be applied to API keys, tokens, and other sensitive data to protect it from exposure in logs, error messages, or application interfaces.
By using dynamic masking, organizations can reduce the risk of accidental exposure of sensitive credentials and ensure that they remain hidden from unauthorized users. Maintaining data usability while masking is crucial. Effective masking requires well-defined privilege settings to ensure only authorized users trigger it, but it may not always be the ideal solution. In contrast, passive security measures, such as auditing and discovering non-human identities, are often easier to implement.
Using DSPM to Automate Non-Human Identity Security
Data Security Posture Management (DSPM) is a powerful tool that automates the protection of non-human identities in cloud environments. DSPM tools provide a centralized platform for discovering, securing, and monitoring sensitive data, including API keys, tokens, and certificates. This is important as the
In a modern cloud environment, keeping track of all non-human identities and their associated credentials can be overwhelming. DSPM tools simplify this by automatically discovering non-human identities and their credentials, providing real-time visibility into their usage, and alerting administrators to any suspicious activity.
How DSPM Works
DSPM tools work by scanning cloud environments to identify resources. Once discovered, DSPM tools help secure them by enforcing DataSunrise setup, masking, and ensuring that they are stored in secure locations.
In addition to securing non-human identities, DSPM tools also provide valuable insights into an organization’s overall security posture. By automating the discovery and protection of sensitive credentials, DSPM tools allow security teams to focus on higher-level tasks, such as threat hunting and incident response.
With DataSunrise, you can implement DSPM effortlessly, securing multiple cloud resources in just a few clicks. After an initial account scan and deploying the DataSunrise server, all resources are ready for protection.
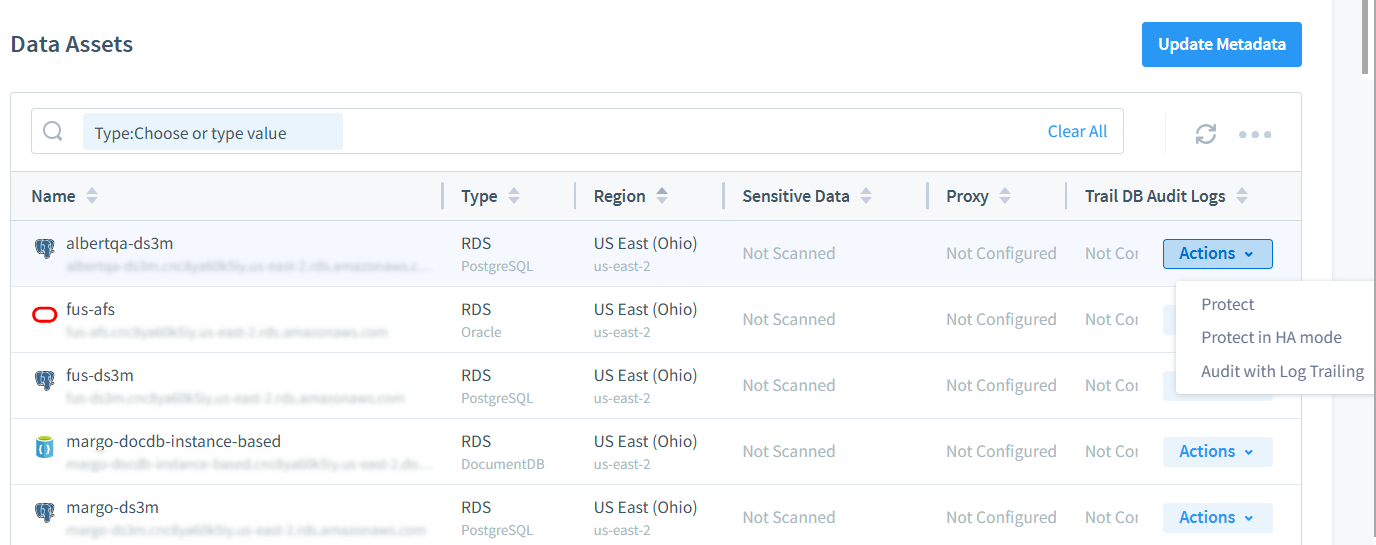
DataSunrise offers a range of discovery automation features, enabling you to use regular expressions or more advanced functions to detect API keys and tokens. It also includes data-inspired security features, allowing you to manage non-human identity protection even in cases of inconsistent formatting.
The Benefits of DSPM for Non-Human Identity Security
Using a DSPM tool to manage non-human identity security offers several benefits:
- Automation: DSPM tools automate the discovery and protection of resources with sensitive credentials, reducing the risk of human error.
- Centralized management: With DSPM, organizations can manage all non-human identities and their credentials from a single platform, making it easier to enforce security policies.
- Real-time monitoring: DSPM tools provide real-time visibility into the usage of non-human credentials, helping to detect suspicious activity before it leads to a breach.
- Compliance: By automating the protection of sensitive credentials, DSPM tools help organizations comply with industry regulations such as GDPR and HIPAA.
Summary and Conclusion
In today’s digital landscape, non-human identity security is more important than ever. Consequently, as organizations adopt cloud services, automation, and APIs, the number of non-human identities has grown exponentially. Protecting the API keys, tokens, and certificates that these identities use is essential for preventing unauthorized access and data breaches.
The key steps to securing non-human identities include discovering all non-human credentials, applying masking and encryption to protect them, and using DSPM tools to automate their security. By adopting these practices, organizations can ensure that their non-human identities remain secure and protected.
DataSunrise and Non-Human Identity Security
DataSunrise offers flexible and cutting-edge tools for database security, including Data Security Posture Management (DSPM). With features like activity monitoring, vulnerability assessment, and masking, DataSunrise ensures that sensitive data—including API keys, tokens, and certificates—remains secure. To see how DataSunrise can help protect your non-human identities, visit our website to schedule an online demo.
