What Is Snowflake Audit Trail
In today’s data-driven landscape, implementing robust audit trails for Snowflake has become a critical security requirement. According to recent cybersecurity statistics from IBM’s 2024 Data Breach Report, organizations with comprehensive audit trail systems identify potential security threats 94% faster and reduce breach-related costs by up to 57%. For enterprises using Snowflake’s powerful data platform, proper audit trail implementation has transformed from a technical consideration into a business necessity.
With data breach costs reaching an average of $5.7 million in 2024 and organizations facing an ever-increasing number of regulatory requirements, traditional manual audit approaches simply cannot keep pace. This article explores how to implement effective audit trails in Snowflake environments, using both native capabilities and enhanced solutions for comprehensive security monitoring.
Understanding Snowflake Audit Trails
A Snowflake audit trail is a chronological record of all activities and operations performed within your Snowflake environment. This systematic recording captures who accessed what data, when they accessed it, what changes were made, and from which locations. Proper audit trail implementation provides complete visibility into your data warehouse activities, enabling security teams to detect unauthorized access, monitor sensitive data usage, and demonstrate regulatory compliance.
The importance of comprehensive audit trails has grown significantly as organizations migrate more sensitive workloads to cloud platforms. Snowflake’s architecture introduces several unique considerations for audit trail implementation:
- Multi-Regional Data Storage: Different regulatory frameworks apply simultaneously across regions, creating complex compliance requirements.
- Distributed Access Patterns: Users connect from various networks and devices, requiring sophisticated access monitoring.
- Diverse Query Methods: Activities occur through SQL interfaces, APIs, and partner tools, necessitating unified audit capture.
- Scale Challenges: High-volume environments generate massive audit logs that require efficient storage and analysis strategies.
- Compliance Complexity: Organizations must satisfy multiple regulatory frameworks (GDPR, HIPAA, PCI DSS, SOX) simultaneously.
Native Snowflake Audit Trail Capabilities
Snowflake includes several built-in features for implementing audit trails. These capabilities provide the foundation for tracking user activities, data access, and system changes.
1. Account Usage Views
Snowflake’s ACCOUNT_USAGE schema contains several views that provide historical audit data through standard SQL queries:
-- Query login history for the past 7 days SELECT USER_NAME, EVENT_TIMESTAMP, CLIENT_IP, REPORTED_CLIENT_TYPE, IS_SUCCESS FROM SNOWFLAKE.ACCOUNT_USAGE.LOGIN_HISTORY WHERE EVENT_TIMESTAMP >= DATEADD(DAY, -7, CURRENT_TIMESTAMP()) ORDER BY EVENT_TIMESTAMP DESC;
Key views include:
- LOGIN_HISTORY: Records all authentication attempts
- QUERY_HISTORY: Captures details about executed queries
- ACCESS_HISTORY: Logs object access events
- DATA_TRANSFER_HISTORY: Tracks data movement operations
2. Time Travel and Data Retention
Snowflake’s Time Travel feature enables point-in-time analysis of data changes, providing an additional audit mechanism:
-- View table data as it existed 4 hours ago SELECT * FROM my_table AT(OFFSET => -240*60); -- Create a dedicated audit table preserving historical changes CREATE TABLE audit_history AS SELECT *, CURRENT_TIMESTAMP() AS audit_timestamp FROM my_table AT(OFFSET => -240*60);
By leveraging Time Travel with dedicated audit tables, organizations can maintain detailed records of data states for compliance and forensic purposes.
3. Object Tagging and Classification
Snowflake’s tagging capabilities help identify and track sensitive data for enhanced audit focus:
-- Tag columns containing sensitive data
ALTER TABLE customers MODIFY COLUMN social_security_number
SET TAG sensitivity = 'high', data_type = 'PII';
-- Query tagged objects for audit configuration
SELECT
table_name,
column_name,
tag_value AS sensitivity
FROM
table(information_schema.tag_references('sensitivity', 'table'));
These tags enable targeted audit strategy implementation, focusing detailed monitoring on high-risk data while applying more general audit approaches to less sensitive information.
4. Web Interface for Audit Review
Snowflake’s web-based interface provides intuitive access to audit information without requiring SQL expertise:
- History Tab: View recent queries with filtering capabilities
- Users & Roles: Monitor access control changes
- Usage: Track resource consumption by warehouse
- Account: Review administrative configurations
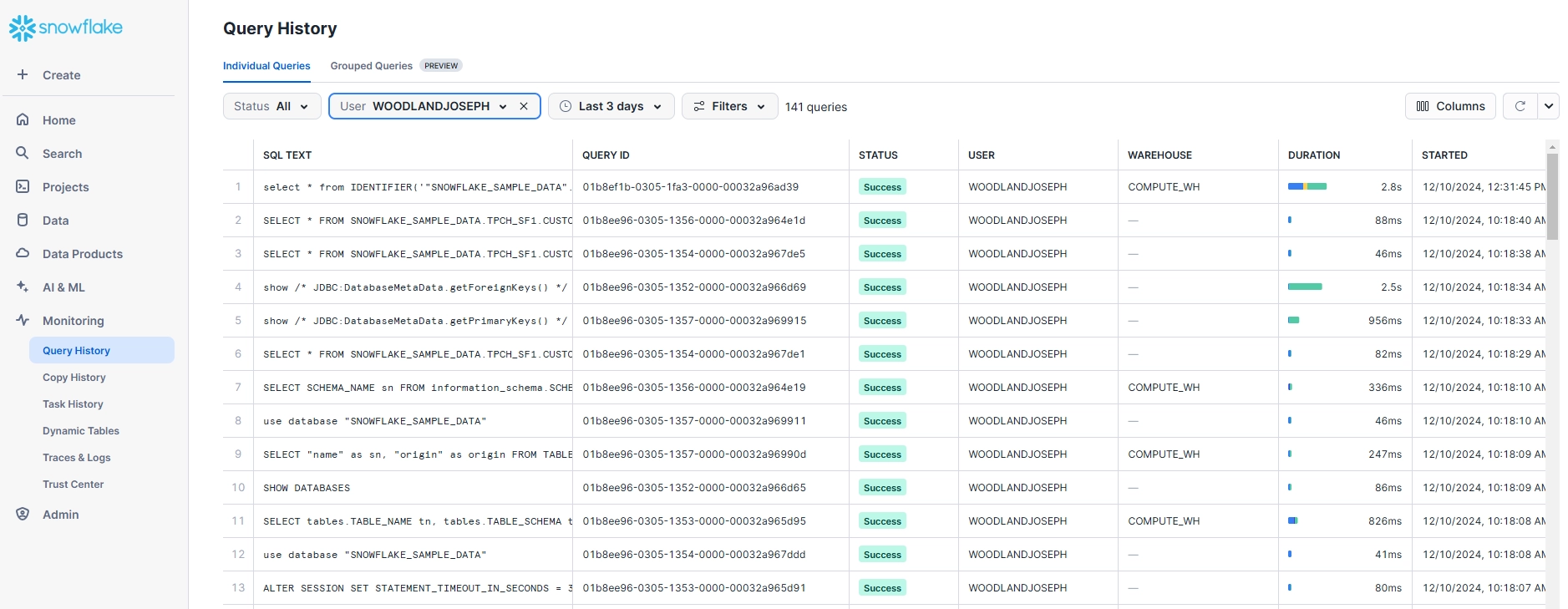
While these native capabilities provide essential functionality, organizations with advanced security requirements often encounter several limitations:
| Native Feature | Key Limitation | Business Impact |
|---|---|---|
| Account Usage Views | Limited retention periods (typically 1 year) | May not satisfy long-term compliance requirements |
| Query History | Basic logging without behavioral analysis | Difficulty identifying sophisticated attack patterns |
| Object Tagging | Manual configuration process | Critical data may remain untagged and under-audited |
| Access Controls | Complex configuration and maintenance | Administrative overhead increases with scale |
| Alerting | No native real-time notification system | Delayed response to potential security incidents |
Enhanced Snowflake Audit Trail with DataSunrise
While Snowflake’s native audit capabilities provide a foundation, DataSunrise significantly enhances audit trail implementation through its comprehensive security platform. DataSunrise’s Database Regulatory Compliance Manager transforms Snowflake audit trails with Zero-Touch Data Protection and sophisticated automation features.
1. Connecting Snowflake to DataSunrise
The first step in implementing enhanced audit trails is connecting your Snowflake instance to DataSunrise. This establishes a secure connection that enables DataSunrise to monitor all Snowflake activities without impacting performance or requiring extensive configuration changes.
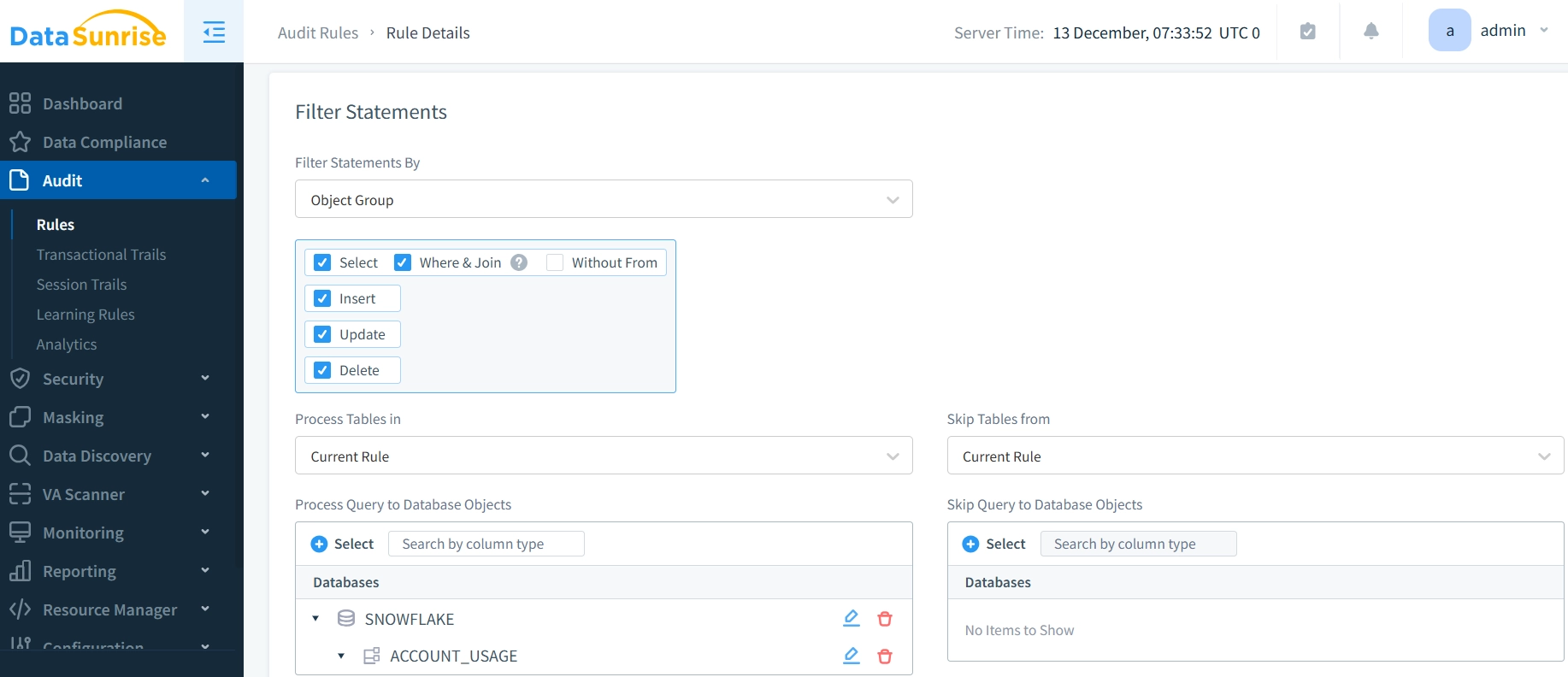
2. Creating Customized Audit Rules
Once connected, you can create detailed audit rules tailored to your specific security and compliance requirements. DataSunrise’s No-Code Policy Automation enables security teams to define sophisticated audit policies through an intuitive interface without writing complex SQL statements. This approach dramatically reduces implementation time from weeks to hours.
3. Reviewing Comprehensive Audit Trails
DataSunrise captures detailed audit trails that provide complete visibility into all Snowflake activities. The platform’s Transactional Trails feature provides comprehensive visibility into all database operations, enabling security teams to quickly investigate potential issues and demonstrate compliance with regulatory requirements.
Key DataSunrise Features for Snowflake Audit Trails
DataSunrise enhances Snowflake’s native audit capabilities through several advanced features:
1. Auto-Discover & Classify Engine
DataSunrise’s proprietary algorithms automatically scan your Snowflake environment to identify sensitive data according to regulatory frameworks like GDPR, HIPAA, and PCI DSS. This intelligent classification ensures that all sensitive data receives appropriate audit coverage, eliminating blind spots that might exist in manually configured systems.
2. Intelligent Policy Orchestration
The platform’s No-Code Policy Automation capabilities allow security teams to create sophisticated audit policies without specialized SQL expertise. These policies can be consistently applied across multiple Snowflake environments, ensuring uniform audit coverage throughout your organization.
3. Real-Time Monitoring and Alerts
Unlike Snowflake’s native features, DataSunrise provides real-time notifications with immediate alerts for suspicious activities. These real-time alerts enable security teams to respond quickly to potential security threats, significantly reducing the detection and response time for suspicious activities.
4. User Behavior Analysis
DataSunrise’s advanced behavior analytics establish baselines of normal user activity and identify anomalies that might indicate security threats. This behavioral monitoring transforms audit trails from passive records into proactive security tools that can identify potential threats before they escalate into serious incidents.
5. Automated Compliance Reporting
DataSunrise streamlines compliance reporting with pre-configured templates for major regulatory frameworks:
- GDPR Compliance: Tracking of personal data access and processing
- HIPAA Compliance: Monitoring of protected health information
- PCI DSS Compliance: Auditing of payment card data access
- SOX Compliance: Recording of financial data modifications
These automated reports dramatically reduce the time and effort required for audit preparation, transforming days of manual work into automated processes that complete in minutes.
Best Practices for Snowflake Audit Trail Implementation
To maximize the effectiveness of your Snowflake audit trail implementation, consider these best practices:
1. Strategic Monitoring Approach
Implement a tiered audit strategy based on data sensitivity:
- Comprehensive Monitoring: Apply detailed auditing to PII, PHI, and financial data
- Standard Auditing: Monitor access to operational data and aggregate information
- Basic Tracking: Maintain general logs for non-sensitive system operations
This approach balances security needs with performance considerations, focusing resources where they deliver the greatest risk reduction.
2. Retention Management
Establish clear audit data retention policies that align with regulatory requirements:
- Active Retention: Keep recent audit data (30-90 days) readily accessible
- Archival Storage: Implement compressed archiving for historical records (1-7 years)
- Legal Hold Provisions: Define procedures for preserving audit data during investigations
Proper retention policies ensure compliance while optimizing storage costs and query performance.
3. Documentation and Training
Maintain comprehensive documentation of your audit implementation:
- Architecture Diagrams: Document audit data flow and storage systems
- Policy Documentation: Maintain clear records of audit configurations
- Training Materials: Ensure security teams understand how to interpret audit data
Thorough documentation supports knowledge transfer, consistent operations, and demonstrates due diligence during compliance reviews.
4. Regular Audit Review
Establish routine processes for reviewing audit information:
- Daily Security Checks: Review high-priority alerts and anomalies
- Weekly Pattern Analysis: Examine trends and potential emerging threats
- Monthly Compliance Validation: Confirm continued adherence to regulatory requirements
Regular reviews transform audit data from a reactive investigative tool into a proactive security resource.
5. DataSunrise Implementation
Leverage DataSunrise’s specialized capabilities to enhance your audit implementation:
- Intelligent Classification: Use automated data discovery to identify sensitive data
- Behavioral Analysis: Implement user behavior monitoring to detect anomalies
- Centralized Management: Manage audit policies across multiple environments
DataSunrise’s comprehensive platform significantly enhances Snowflake’s native capabilities, providing enterprise-grade protection with minimal administrative overhead.
Conclusion
As organizations increasingly rely on Snowflake for critical data operations, implementing robust audit trails has become essential for security and compliance. While Snowflake’s native audit capabilities provide valuable functionality, organizations with complex requirements benefit significantly from enhanced solutions like DataSunrise.
The combination of Snowflake’s powerful data platform and DataSunrise’s advanced security features creates a comprehensive audit infrastructure that protects sensitive information, ensures regulatory compliance, and provides actionable security intelligence. By implementing these technologies with strategic best practices, organizations can confidently migrate even their most sensitive workloads to Snowflake while maintaining complete visibility and control.
Ready to enhance your Snowflake audit capabilities? Schedule an online demo today to see how DataSunrise can transform your audit strategy while reducing administrative overhead.
