DataSunrise Database Activity Monitoring for Amazon Redshift
DataSunrise is an Advanced Amazon APN Technology Partner in data and database security. Amazon Redshift monitoring tool by DataSunrise is an effective solution to keep you aware of all user transactions being conducted in your database. It provides an insight into what exactly database users do and when. There is a learning mode that assists during deployment process by creating a list of typical for certain users SQL queries. DataSunrise detects malicious queries and notifies administrators. Use Amazon Redshift monitoring tools for cyberattack protection, privileged user and application activity monitoring.
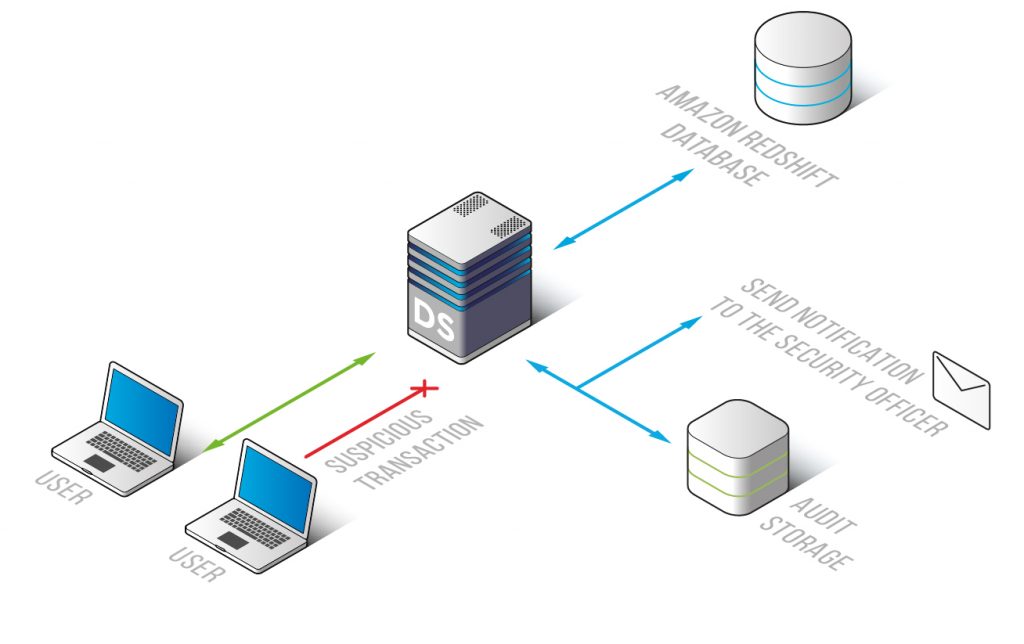
Amazon Redshift monitoring tool by DataSunrise provides full visibility of database queries allowing to ensure that all corporate security policies are being enforced correctly.
In self-learning mode DataSunrise generates a list of common transactions according to scrutinized analysis of user queries. All other queries are assumed to be potentially dangerous. Using sophisticated algorithms it reveals anomalies, attempts of hacking activity, SQL injections and alerts administrators of a security rule violation.
In case an employee copied the database to a hard drive, Redshift monitoring tool gives you the opportunity to see who made it and take actions in order to prevent further dissemination of valuable information. Also, you can set DataSunrise to notify administrators of certain operations.
Regulatory organs in information security sphere demand affected parties to apply database monitoring and audit systems (SOX, PCI DSS, HIPAA and others).
Amazon Redshift monitoring tool by DataSunrise provides management over a number of databases, which saves a lot of time and gives a big picture view of all corporate transactions. The solution has flexible features that simplify working with the system, while there is no any negative effect on database performance. The ability to integrate with SIEM systems provides real-time security alert analysis.
Detailed logs contain session data (IP addresses, hostnames, applications), changes made to the database, SQL codes of processed queries, what was the answer to the query, security policy update, user privilege assignment, authorization attempts, etc.
Providing full visibility of database activities and detecting various types of malicious queries, Redshift monitoring tool provides sufficient components for building a comprehensive database security system and complying privacy and security mandates.


