DataSunrise Database Activity Monitoring for Azure SQL
Database Activity Monitoring for MS Azure SQL by DataSunrise continuously analyzes and records all database operations. Solution helps in complying PCI DSS, HIPAA, SOX and other mandates. Self-learning feature examines typical queries and generates a list of safe SQL queries. Using advanced algorithms, DataSunrise detects potentially hazardous operations and notifies administrators, so that they can timely respond to the threat.
Working in a sniffer mode DataSunrise keeps track of every transaction made by privileged and common users of MS Azure SQL database, while no impact on database performance is being made. In most of the cases data leaks are the result of malicious actions of company members or their negligent attitude towards confidential information. That’s why it is so important to place greater focus on employee transactions.
Self-learning mode helps to generate a group of SQL queries typical for a certain environment and makes its further customization easier. In case the processed query is not on the list or in case it interferes with security rules defined by administrators, DataSunrise blocks the query and notifies of a certain rule being triggered.
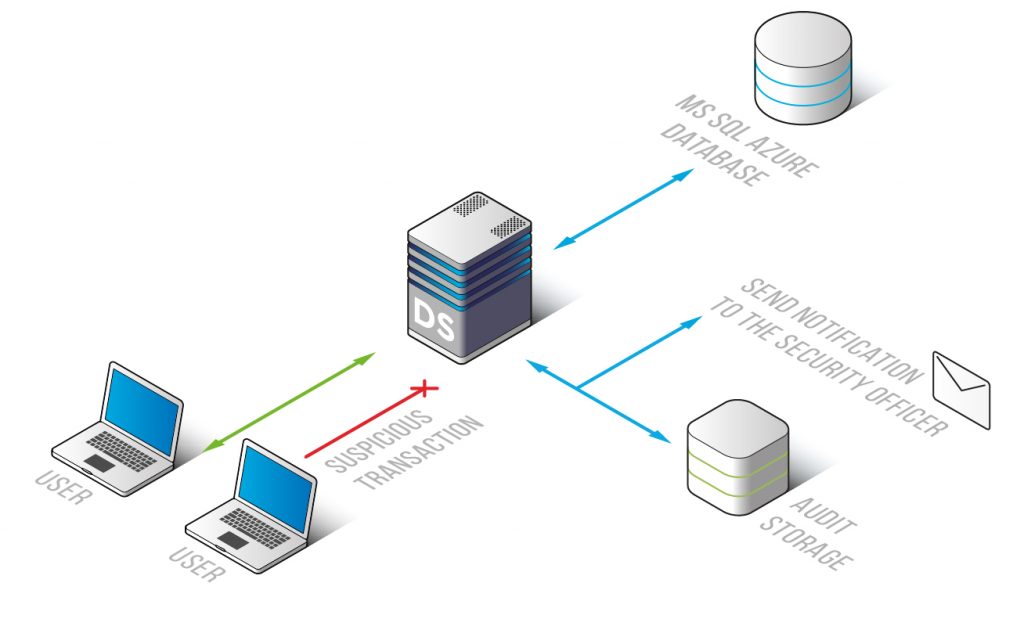
With our database activity monitoring tool you always know who used certain data and when. The convenient interface has a set of customizable features that allow to adjust the solution to a variety of purposes. It allows to see codes of SQL queries and results of their execution, changes made to security/ audit rules and firewall settings, attempts of entering the system, user session data, including hostnames, IP addresses and applications used to query the database.
Syslog protocol support enables integration with security information and event management (SIEM) products, such as McAfee, Splunk, IBM QRadar, HP ArcSight and others. SIEM systems analyze security alerts in real-time.
DataSunrise Database Activity Monitoring for MS Azure SQL is a simple-to-use and effective solution to keep track of user activity and detect potentially dangerous operations. It complies requirements of regulatory agencies and helps to build a comprehensive security system of on-premises or cloud database.


