DataSunrise Database Activity Monitoring for Cloudberry Database
DataSunrise provides the Activity Monitoring solution for the Cloudberry database with advanced query analyzing technologies, ensuring real-time awareness of all database activities. Thanks to this, database administrators can easily identify illegal, fraudulent, or undesirable behaviors through self-learning analysis. It meticulously tracks transactions, including those by privileged users, to maintain the security and integrity of your database.
To monitor Cloudberry database transactions, DataSunrise employs sophisticated algorithms that analyze network traffic across multiple platforms, creating a whitelist of typical queries. These self-learning algorithms save administrators’ time and simplify security software optimization, enhancing overall system efficiency.
The monitoring solution informs about the actions of privileged users such as superusers, database administrators, developers, and others. Convenient audit and skip rules streamline database management processes, providing detailed data on user transactions and configuration changes.
Cloudberry’s Activity Monitoring helps organizations comply with regulatory mandates like SOX, HIPAA, PCI DSS, and more.
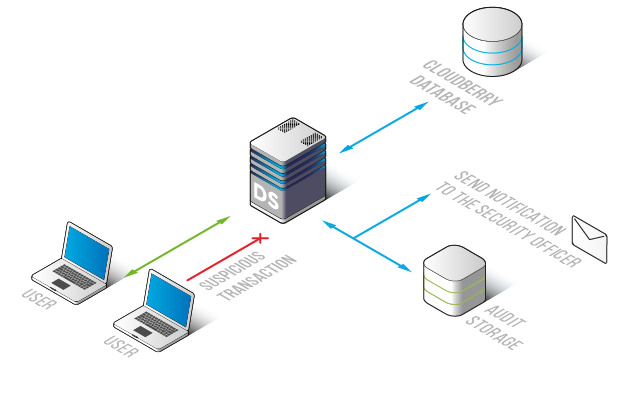
Through comprehensive traffic analysis, Cloudberry Activity Monitoring detects non-typical transactions, attack attempts, privilege escalation, brute-force attacks, and unauthorized actions by privileged users. Each audit/skip rule can trigger notifications via SMTP and SNMP, ensuring prompt awareness of potential threats.
Cloudberry’s monitoring solution keeps you informed of suspicious operations within your corporate network, bolstering database security.
Monitoring results are securely stored in an outsourced database, preventing intruders from erasing traces of malicious activity. These logs are vital evidence of illegal operations and can be integrated with SIEM systems for real-time security threat analysis.
Logs contain detailed information including query codes, IP addresses, hostnames, applications used, administrator configuration changes, user authentication data, and SQL codes of executed queries.


