Database Activity Monitoring for GaussDB
DataSunrise provides a solution for Database Activity Monitoring for GaussDB. With it, database administrators will be able to be aware of database activities in real-time by advanced query analysis technology. Activity Monitoring gives you the possibility to detect fraudulent, illegal, or any other unwanted activities due to the results of self-learning analyses. It tracks the actions of all users including privileged ones to maintain the appropriate security level of GaussDB.
Activity Monitoring is based on the learning algorithms that analyze network traffic and create the allowed list of typical queries. Usage of this algorithm saves time and resources for the security teams and simplifies further security software optimization.
With GaussDB Activity Monitoring you will be able to monitor the activities of all users including users with privileged access. Moreover, our tool records actions made to privacy policy and configurations. If there is an attempt of attack, the configured rule will be triggered and you will get an alert about certain security/audit rules. Activity Monitoring enables you to set notifications via SMTP or SNMP for every rule.
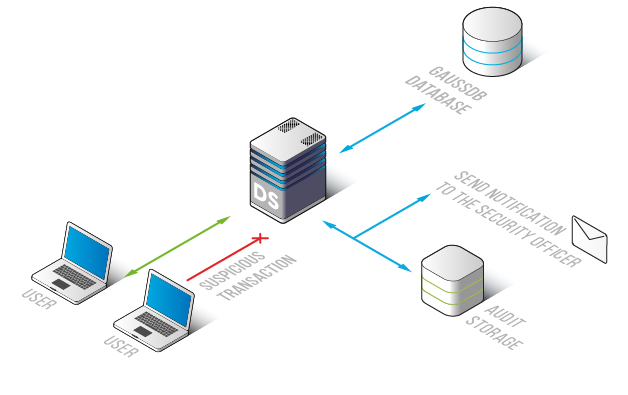
Activity Monitoring for GaussDB collects detailed logs of database activity that can be used for analyses. Logs contain the following information:
- User session data such as IP addresses, host, user, application names, list of processed queries, etc.
- Detailed event logs such as code of the query, result of query execution, etc.
- System data such as authentication data, errors that occurred, changes made to the privacy policy, etc.
This information can be used for investigations of illegal actions. Also, the information that activity monitoring gathers helps you comply with various data protection regulations such as SOX, HIPAA, GDPR, and others.
Recorded results are stored in the outsourced database that excludes the possibility to hide evidence of malicious activity. Integration with SIEM-system allows you to get real-time analysis of threats connected to security issues.


