DataSunrise Database Activity Monitoring for Google Cloud SQL
DataSunrise Database Activity Monitoring for Google Cloud SQL is aimed at the continuous real-time tracking of transactions made within multiple databases and alerting of hacking attempts and potentially dangerous attempts. Advanced filtration system helps to detect malicious code execution and SQL injections. An effective solution to minimize the risk of data leaks and manage compliance of corporate security policy.
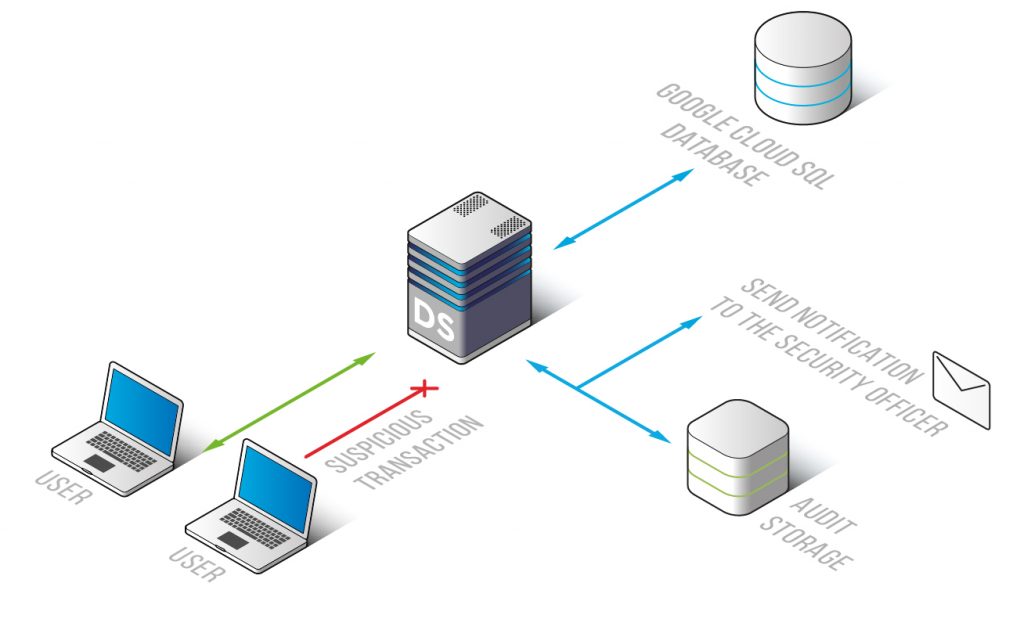
DataSunrise provides for Google Cloud SQL database activity monitoring solution with the ability to detect SQL injections and differentiate between normal and malicious transactions in real time. It identifies typical user queries with help of learning rules and reveals anomalies, even if they are not specifically against policy.
Database activity monitoring system makes it easy for administrators to get the full picture of database activities by automatically analyzing data and providing understandable reports. Moreover, there is an opportunity to switch on notification feature and add email addresses to receive alerts on fraudulent operations.
All functions of DataSunrise are managed within a user-friendly unified graphical interface. Flexible settings allow you to automate the monitoring process. Integration with SIEM-systems (HP ArcSight, McAfee, Splunk, IBM QRadar and others) enables real-time analysis of security alerts. It also assists to address requirements of government and regulatory agencies (PCI DSS, HIPAA, SOX and others).
DAM system logs contain:
- Codes of executed queries and number of affected rows, columns;
- Session data (applications used to query the database, IP addresses, host names);
- System events (authentication data, database errors, security/audit rule updates).
DataSunrise Database Activity Monitoring for Google Cloud SQL is a reliable system to keep under observation transactions performed by privileged and non-privileged users. Another step up in reinforcing your database security system by revealing SQL injections and other signs of hacking activity.


