DataSunrise Database Activity Monitoring for Hydra
DataSunrise provides the monitoring solution for the Hydra data warehouse. Using Database Activity Monitoring you will know how data is viewed, how it is changed, and who is viewing it in real-time. Activity monitoring reveals the fraudulent activity of privileged users and hacker attacks.
Database Activity Monitoring in a self-learning mechanism creates a group of SQL queries that are typical for a certain platform. This functionality prevents a false activation of a firewall and helps in data warehouse management.
DataSunrise collects results of traffic analyses, identifying non-typical queries, attack attempts, unauthorized actions of privileged users, brute-force attacks, and other potentially dangerous actions. Moreover, collecting activity logs can be useful for analysis and can be used as evidence of illegal activity during the cybercrime investigation. Collected logs can not be deleted or corrupted, as far as this data is stored in the outsourced database.
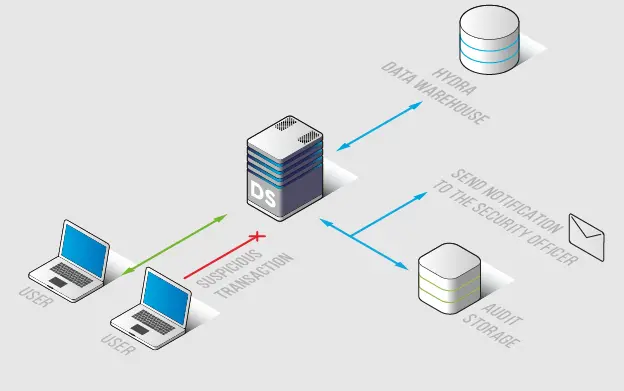
Also, DataSunrise can send logs for SIEM-systems such as Splunk, IBM QRadar, McAfee, and others. This possibility provides you with real-time analysis of information security threats. Logs contain the following information:
- User session data, including host, user, application names, IP addresses, session duration, list of processed queries, etc.;
- Detailed event logs (code of the query, result of query execution);
- System data (changes made to the privacy policy, authentication data, privilege assignment, errors occurred).
DataSunrise Database Activity Monitoring can also send alerts of non-typical operations that enable administrators to respond to suspicious activities and not search for suspicious activity among other transactions.
With Activity Monitoring, you will be sure that your data is safe and that you can be in compliance with different national and international data protection laws and acts.


