DataSunrise Monitoring for Oracle
Oracle Database Activity Monitoring by DataSunrise continuously examines incoming transactions and differentiates normal queries from dangerous ones. Database activity monitoring for Oracle helps to detect SQL injections, abnormal access requests and non-typical operations of privileged users. Complying standards of regulatory agencies, it provides transparency of Oracle database transactions without interfering with business processes.
Oracle Database Activity Monitoring by DataSunrise provides comprehensive monitoring of database activity enabling to see who and how viewed or updated certain information, revealing signs of SQL injections, fraudulent insider activity, other suspicious operations and database vulnerabilities.
The Oracle Monitoring rule settings have a feature to send notifications via SMTP or SNMP when a certain security rule is triggered. It saves a lot of time, as administrators don’t have to look through all operation logs. Moreover, it enables them to take measures against hacking attempts proactively.
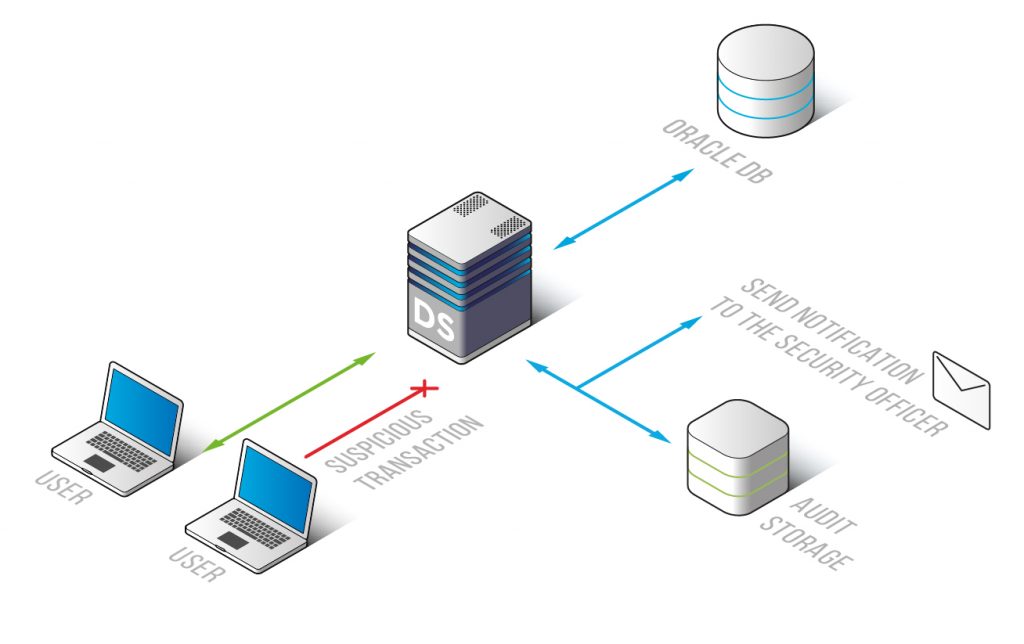
DataSunrise collects information necessary for enabling compliance controls and investigation of cyber frauds. Logs cannot be edited as they are automatically sent to the outsourced database or SIEM system (HP ArcSight, IBM QRadar, Splunk, McAfee). It contains:
- Codes of SQL queries, responds to queries;
- Session data on Oracle database users;
- Applications used to query the database, IP addresses, host names;
- Configuration changes (security rule update, database errors, authorization attempts, etc.)
PCI DSS, SOX, HIPAA and some of the other regulations require affected parties implement database monitoring tools.
The interface of our product is designed to simplify the work of administrators and automate auditing and skipping processes.
Oracle Database Activity Monitoring by DataSunrise identifies database vulnerabilities and malicious transactions, helping to minimize risks of data leakage. Database Activity Monitoring for Oracle is one of the essential measures for preventing data theft, meeting security mandates and protecting data integrity.


