DataSunrise Database Activity Monitoring for PostgreSQL
DataSunrise provides for PostgreSQL monitoring solution with advanced query analyzing technologies that will keep you aware of all database activities in real time. Activity monitoring assists in identifying illegal, fraudulent or any other undesirable behavior according to the results of self-learning analysis. It tracks transactions including actions of privileged users and helps to maintain PostgreSQL database security.
PostgreSQL Monitoring
To monitor PostgreSQL database transactions DataSunrise uses sophisticated learning algorithms that analyze corporate network traffic over multiple platforms and prepare a whitelist of typical queries. Self-learning algorithms save time for administrators and simplify further security software optimization.
PostgreSQL monitoring solution by DataSunrise helps you to be aware of actions of privileged users like superusers, database administrators, developers, system administrators, helpdesk and outsourced personnel.
Convenient audit and skip rules simplify database managing processes and provides detailed data on user transactions and configuration changes.
DataSunrise Activity Monitoring for PostgreSQL helps to address regulatory mandates (SOX, HIPAA, PCI DSS).
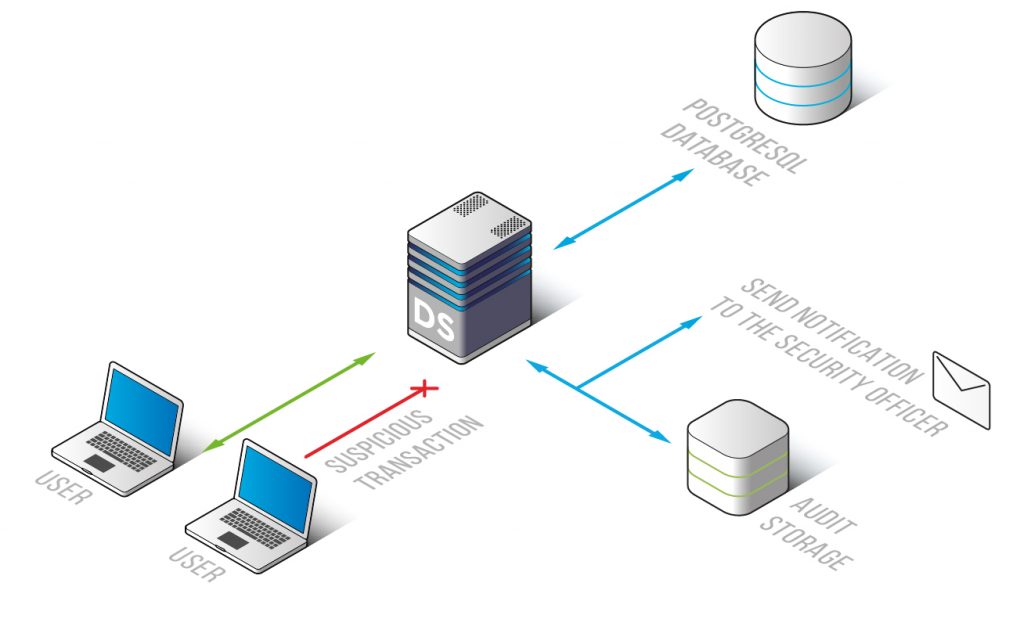
Hazard Detection
According to results of traffic analysis, DataSunrise identifies non-typical transactions, attack attempts, privilege escalation, brute-force cracking and unauthorized actions of privileged users. Each audit/skip rule has a feature to send notifications via SMTP and SNMP.
PostgreSQL monitoring solution keeps you aware of suspicious operations executed in your corporate network and helps to maintain database security.
PostgreSQL Monitoring and Logging
Recorded results of monitoring are stored in the outsourced database, eliminating the possibility for an intruder to hide traces of malicious activity. They also can be used as a vital evidence of illegal operations. There is an opportunity to integrate with SIEM-system and get comprehensive real-time security threats inspection.
Logs contain codes of queries, IP addresses, hostnames, used applications, settings changes made by administrators, user authentication data, SQL codes of executed queries, etc.


