DataSunrise Activity Monitoring for YugabyteDB
DataSunrise provides you an opportunity for continuous activity monitoring for YugabyteDB. Activity Monitoring tool enables you to accurately watch any actions of database users, including undesirable and fraudulent activities. Our advanced query analyzing technology lets you track all queries and even actions of privileged users. Moreover, this tool is a basis for your Yugabyte database security.
DataSunrise uses learning algorithms to monitor Yugabyte database transactions. Our Activity Monitoring analyzes the network traffic and prepares a white list of typical queries. One more advantage of the self-learning mechanism is that it can make the work of security teams and administrators easier.
Activity monitoring tool is used for detection of SQL – injections, abnormal access requests, and non-typical actions of privileged users. Moreover, rule settings have a feature of sending notifications via SMTP or SNMP when one of the security rules is triggered. This possibility helps database administrators take measures against hacking attempts in time and do not lose the first traces of data leakage.
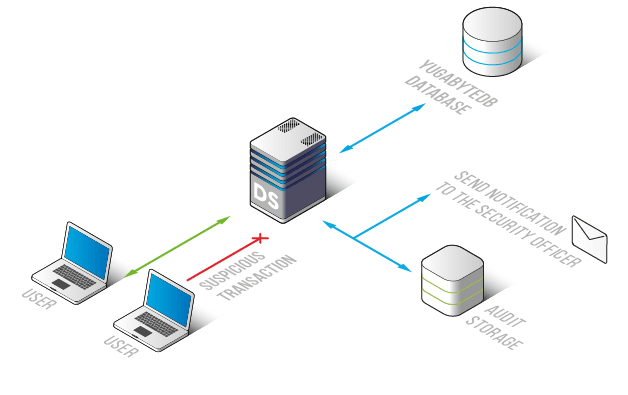
Also, with monitoring by DataSunrise you will be able to comply with such regulations and acts like SOX, HIPAA, GDPR, and others. Audit logs are very useful as it helps provide audit reports and also fulfill the basic requirements of these regulations.
Activity Monitoring helps you to maintain Yugabyte database security. It catches every non-typical action such as privilege escalation, brute force cracking, and unauthorized actions of privileged users. Thanks to it you can be aware of every suspicious activity in your Yugabyte databases.
Moreover, logs contain the following information:
- codes of queries;
- IP addresses;
- hostnames;
- used applications;
- SQL codes of executed queries;
- user authentication data, and others.
One of the main advantages of our activity monitoring for YugabyteDB is that all logs reports are stored in the outsourced databases. It means that malicious actors can not hide their traces or tamper the logs files. Also, there is an integration with SIEM-systems (HP ArcSight, IBM QRadar, Splunk, McAfee). Thanks to it you will get real-time notifications about security threats inspection.


