
Active Directory Authentication for MySQL Database
MySQL databases don’t contain a built-in mechanism to support the Active Directory (AD) authorization. However, it is possible to configure AD authorization using third-party plugins and modules, with some restrictions. Such solutions are not available for all MySQL versions and usually complex in implementation and maintenance.
This article explains how AD authorization could be easily performed with DataSunrise Software, namely, with the Proxy Authentication feature.
It is assumed that you have the following configuration:
- The Active Directory box reachable from the DataSunrise host.
- DataSunrise software configured to work in the Proxy mode.
- A MySQL database protected by the DataSunrise firewall.
The following steps outline the configuration of AD authentication for MySQL and define the pre-requisites for the configuration.
Step 1: Configure DataSunrise to Interact with DC Using LDAP Protocol
Log in to DataSunrise using the web interface and go to the System Settings. In the AD/LDAP parameters specify the following parameters:
- LDAP Server Host. Specify the IP or the host name of the Active Directory box.
- LDAP Server Port. Specify the LPAD server port. Usually port 389 is used for TCP and UDP connection and 636 for LDAP over SSL.
- SSL. Enable the checkbox if an SSL connection is used, otherwise, leave it unchecked.
- LDAP Domain. Specify an Active Directory domain name.
- LDAP Login. Specify an Active Directory user that has access to AD groups.
- LDAP Password. Specify Active Directory user password.
- Type of Authentication to DataSunrise UI. Select “Simple” as authentication type value.
- User Filter. A parameter to search for a user name on LDAP servers.
- Base dn. Distinguished name of a database.
Press the Test button to make sure the parameters you have specified are correct.
In my environment I’m not using an SSL connection, thus the configuration looks like this:
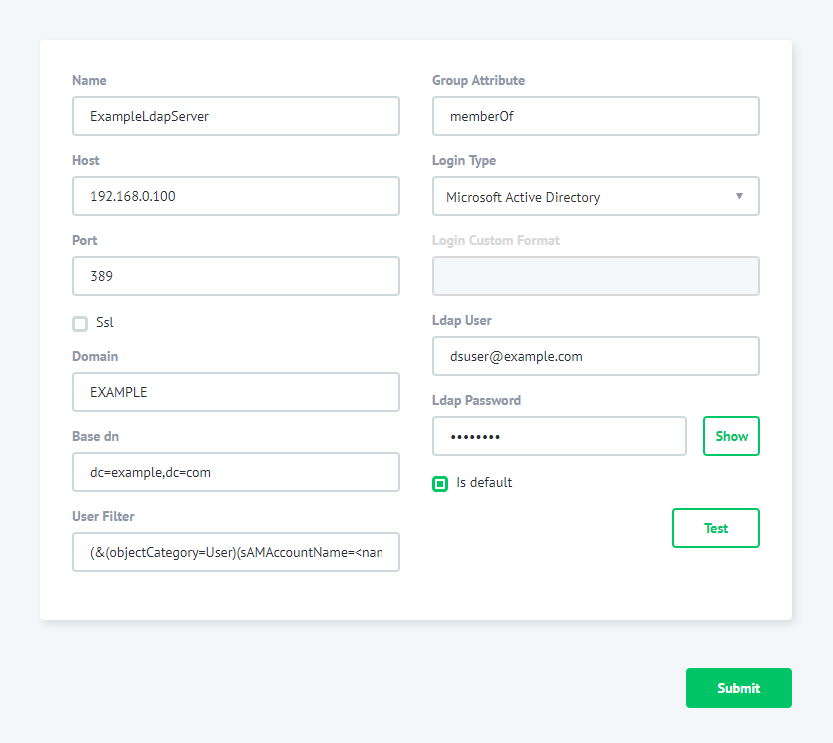
The 192.168.0.100 is the IP address of my AD box. The EXAMPLE is a domain name. dsuser@example.com is an AD user.
To configure “Base dn for LPAD search” in the Web interface go to System Settings->Additional. Find the LdapBaseDN parameter and specify a value for Base DN Search and press the Save button.
Step 2: Enable Active Directory Accounts MappingUsing the Web interface go to Configuration->Databases. Select the database and press Edit. In the Database Edit page press the Auth Proxy Setting button. Press the Enable button and specify Type as “Config”:
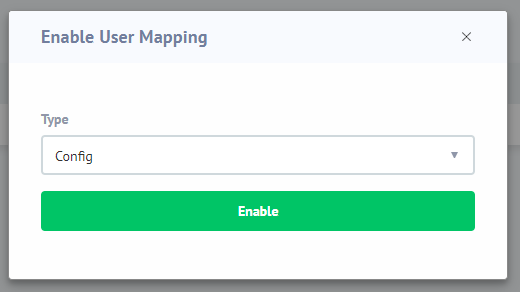
Press the Enable button.
Step 3: Specify User Mapping
Press the Mapping + button and specify the mapping parameters for Active Directory and Database:
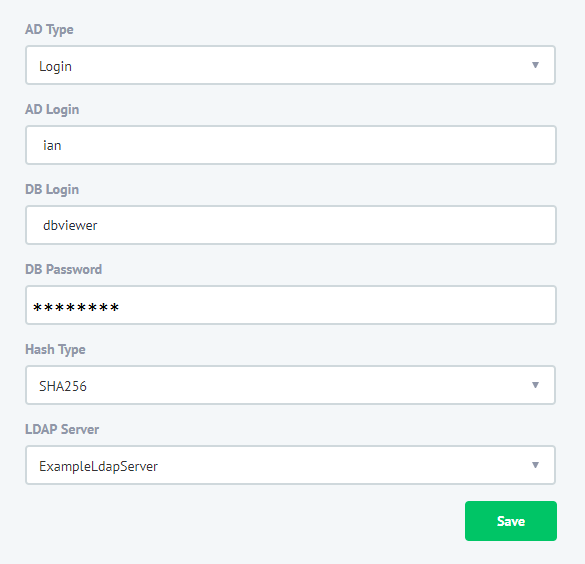
- AD Type. Specify “Login” to map an individual AD account to the database account. To map an AD group to the database account, use the “Group” value.
- AD login. Specify an AD user login. Note that we do not provide domain as a part of the login.
- DB Login. Specify a database user to be used to establish the database connection. DB Password. Specify the password for the database user.
- Hash Type. Select the “SHA-256” value.
- LDAP Server. Self-explanatory.
Now the configuration is complete, so to test it just log in with the domain credentials:
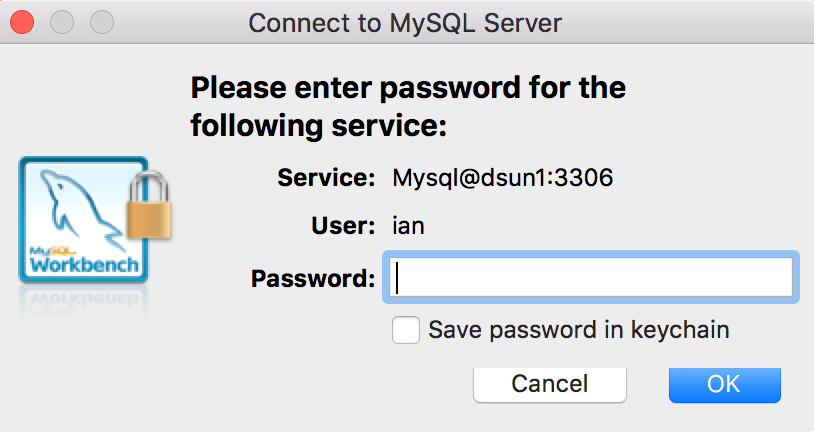
The above guide to the Active Directory Authentication for MySQL Database when using DataSunrise Database Protection Suite shows that it’s an easy 3-step process aimed at making database protection experience simpler for our customers.For MySQL databases you can have Activity Monitoring, Dynamic Masking, Firewall, Performance Monitoring, etc.
