
Aim of a DB Audit Trail
As the number of data leaks continues to rise, government bodies, commercial companies, medical and financial institutions, educational organizations try to protect their sensitive data from being stolen by bad guys. Most industries need to support compliance, security and operations. Laws and regulations controlling the use of electronic records such as SOX, HIPAA, PCI DSS, GDPR make audit trails an important element of protection against security breaches, supporting compliance with regulations and passing various kinds of audits. In other words, any company, government agency or educational organization that deals with sensitive data will benefit from maintaining accurate audit logs.
Purpose of the Database Audit Trail
The general idea of database auditing is to know who and when accessed your data, and what modifications were done to it.
Typically, auditing is used for:
| Aim of a Database Audit | Description |
|---|---|
| Accountability | Tracks who modifies specific schemas, tables, rows, or content to maintain responsibility |
| Prevention of Inappropriate Actions | Discourages improper behavior by showing users we can trace all actions to their identity |
| Suspicious Activity Investigation | Helps identify culprits in data breaches and prevents future occurrences through investigation trails |
| Intrusion Detection | Identifies ongoing data breaches and tracks suspicious long-term activities |
| Access Control Assessment | Helps detect authorization problems and abuse of access rights for proper user permission management |
| Activity Monitoring | Gathers statistical information about specific database activities for analysis |
Key questions addressed by database auditing include:
- Who accessed and modified sensitive data in your system?
- When were specific data changes made?
- How did a particular user gain access to this data?
- Were these changes authorized?
- Did privileged users misuse their extensive access rights?
Theoretically, all these demands can be fulfilled using either native database audit mechanisms or a dedicated software. But the point is that not all audit logs are equally valuable to the auditors. Let’s dwell on this subject for a while.
Using Database-Integrated Audit Mechanisms
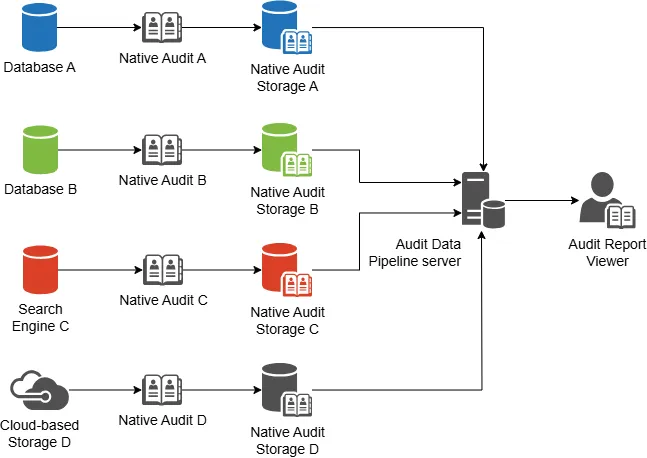
Native audit capabilities vary across different databases. To support multiple data sources, audit administrators need to implement various types of data ingestion, transformation, and storage methods. This approach may potentially duplicate existing audit data.
The matter is that when you use native audit tools it can be too complicated to find certain information about events that you need for an audit. Moreover, logs from native tools are not designed for audit purposes. They are collected for database administrators, so they could know about database bugs and performance problems.
Native Audit Challenges
When you use only native tools for auditing, you will face some difficulties during the work:
- Native audit capabilities that store audit data in the same database can lead to large audit log archives consuming a significant portion of the database storage.
- Native tools often collect information in formats that are not easily readable for auditors and security teams, hindering their ability to analyze logs effectively. Third-party solutions frequently provide customizable reporting capabilities to address this issue.
- Both native and third-party solutions may create overhead on the database server, potentially impacting performance. However, some third-party tools, such as DataSunrise, offer configurable audit subsystems that can operate in different modes, allowing users to minimize or even eliminate performance impact.
If you need to satisfy the auditors’ needs and simplify the work of your security team, just use dedicated stand-alone software. It should be enough to answer the most critical questions that arise when performing a data audit.
The Requirements for a Dedicated Audit Trail Application
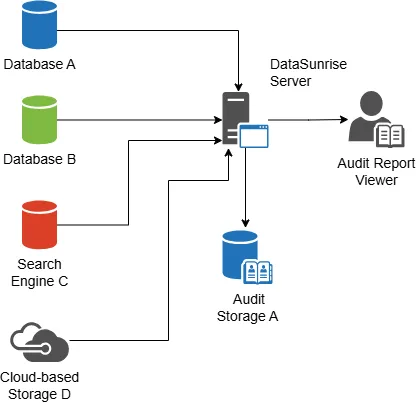
Dedicated audit solutions typically offer a centralized and uniform approach for auditing all supported data sources.
We’ll make it simple, so here are just three major demands for an advanced auditing software:
- It should monitor privileged users who have access to sensitive data.
- The audit log for these data and users should be stored for the required period of time and proper reports should be generated periodically.
- Such a system should include access-preventing and alerting mechanisms activated when an unauthorized activity is detected.
DataSunrise Audit Solution
Based on the requirements we mentioned above, let’s take a closer look at DataSunrise’s capabilities.
DataSunrise’s Data Audit component is capable to audit ALL user actions and queries sent to the target database. Auditing just doesn’t depend on database user type. Thus it is able to audit both regular users’ queries and privileged users’ queries.
DataSunrise stores its auditing results in an integrated SQLite database or in an external database such as PostgreSQL, MS SQL Server, Vertica, Redshift, Aurora MySQL, MySQL. Thanks to DataSunrise’s Report Gen advanced reporting component, you can present your audited data as a customizable report suitable for your auditor’s needs. You can also create reports periodically on schedule.
This comprehensive suite includes a Data Security component capable of preventing unauthorized user access to the target database and notifying security personnel or administrators via email or instant messaging. The system can identify and prevent SQL injections in real-time. Additionally, it features both dynamic and static data masking tools to help prevent accidental data leaks caused by insiders.
Thus, DataSunrise combines three components critical for database security. Data Audit for auditing, Data Security for access control and Data Masking for both dynamic and static data masking.
