
Data-Inspired Security: DataSunrise Enhances Audited Data Protection
The Data Audit task always precedes audit data analytics gathering. But how can we simplify this process? DataSunrise offers a feature that connects raw audit data with data-inspired security decisions: Event Tagging.
With Event Tagging, users can label events with details about the data the query touched. This makes analysis easier. Instead of sifting through all logged queries, you can focus on gathering statistical insights from transactional trails.
Beyond enhancing logged data, DataSunrise uses this additional information for dynamic masking, Audit and Security Rules. This article delves into two key features: Event Tagging and data-inspired rules. While we explore Dynamic Masking Rule in greater detail, we also touch on the Data Filter by Information Type for both Audit and Security rules.
Event Tagging and Information Types
Let’s start with Information Types, which you set in Data Discovery – a crucial step. DataSunrise uses these Information Types to differentiate data in query results.
Information Types provide a description of the data, helping you locate specific data during discovery. But they do more than that. The same Information Types defined in Data Discovery can be used to tag or label data as it’s logged in Audit Transactional Trails. Afterward, you can export the logs with tagged data. As mentioned earlier, the Dynamic Data Masking feature can also trigger masking rules based on these data types.
Here is how the tagged data appears in the downloaded CSV report:
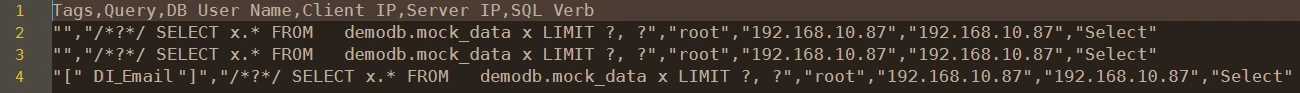
Note the line containing “DI_Email” Information Type.
In summary, having the correct Information Type is essential for effective Event Tagging. In the next section, we’ll explain how to create an Information Type.
Information Type in a Nutshell
Navigate to Data Discovery and select Information Types. Here, you’ll find all available Information Types in DataSunrise. Keep in mind that many are complex and may not suit your specific needs. That’s why, for this discussion, we recommend creating a simple, custom Information Type.
An Information Type is defined by its attributes, and it can have multiple attributes. Matching any of these attributes links query data to the Information Type. For our example, we’ll create the simplest Information Type with just one attribute (DI_EmailAttribute) — data in the query results containing an email string like daniel.d@gmail.com.
We won’t go into too much detail here. The attribute setup is illustrated below:
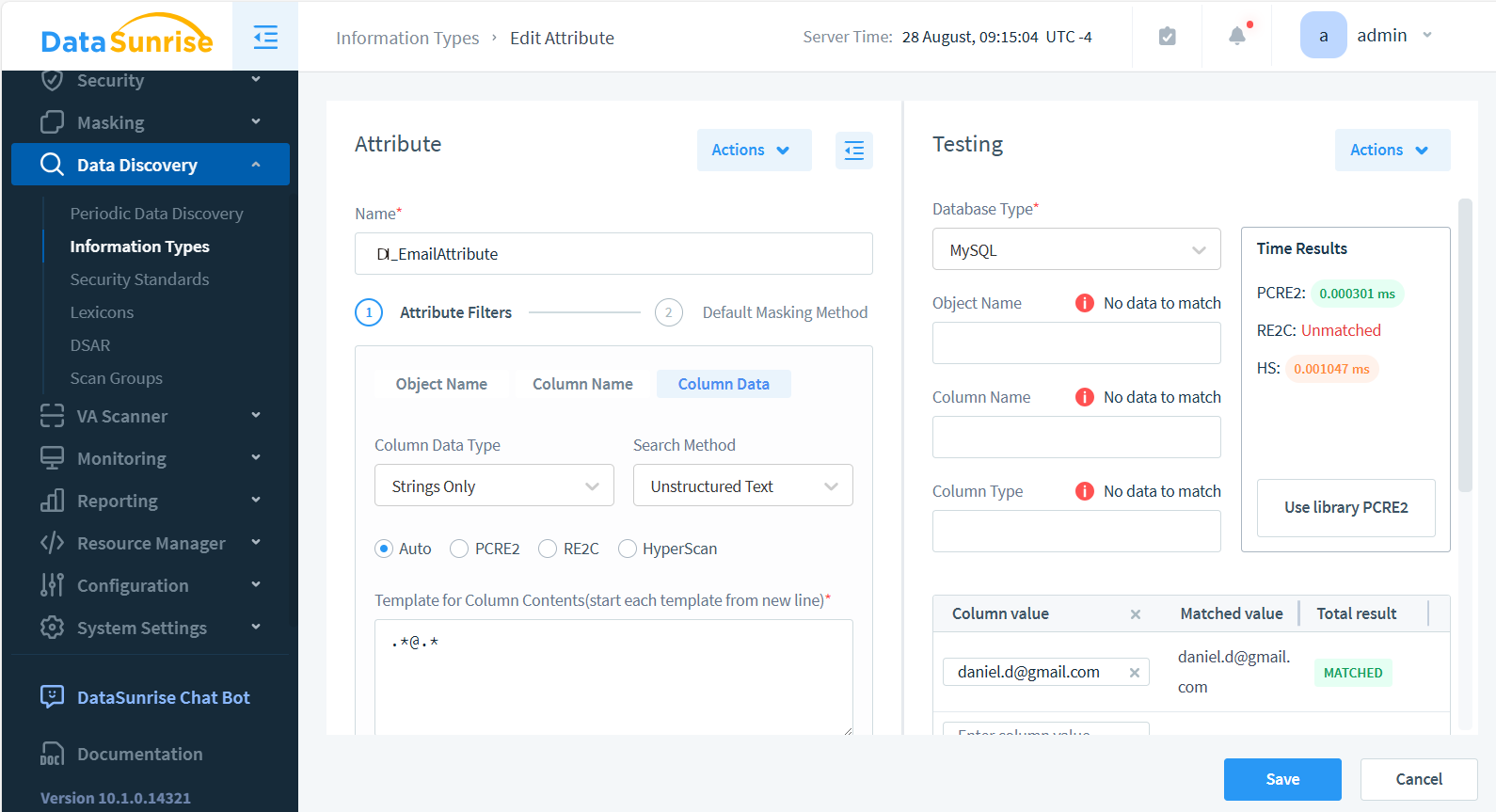
Take note—you can test attribute matching in the panel on the right. For example, we tested the string daniel.d@gmail.com against the regular expression .*@.*, which is set in the column’s data Attribute Filter.
As a result, we’ve created the custom DI_Email Information Type with a regex-based attribute named DI_EmailAttribute. This is shown below:
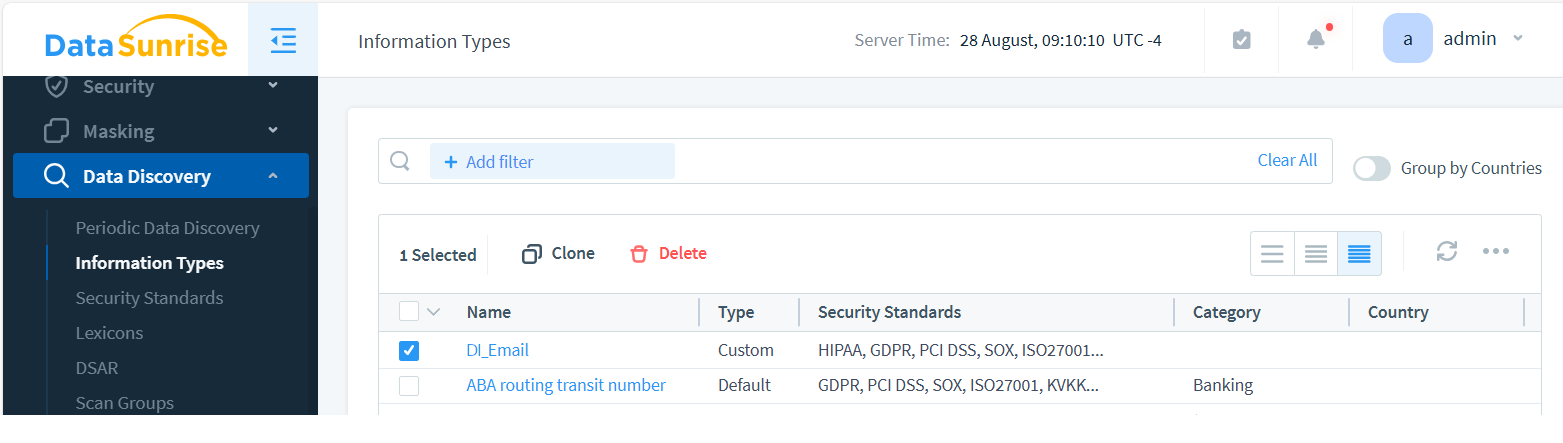
Once a query enters the proxy with Event Tagging enabled, the data is labeled. This valuable information can then be utilized in Audit, Security Rules, and Dynamic Masking.
Keep in mind that for both tagging and dynamic masking in data-inspired security, the Information Type feature works exclusively with data-based attributes.
Event Tagging in Audit
Let’s dive into the first data-inspired security feature: Event Tagging. This feature allows you to mark Transactional Trails logs with additional tags that describe the Information Type affected by the Audit Event Record. This significantly streamlines data-driven decisions on audited instances and eliminates the need for users to parse query results manually.
To enable Event Tagging, first, ensure that the Information Type is functioning correctly. You can test this by running a Data Discovery task. If everything checks out, you can proceed to create an Event Tag.
Add Event Tagging for The Instance
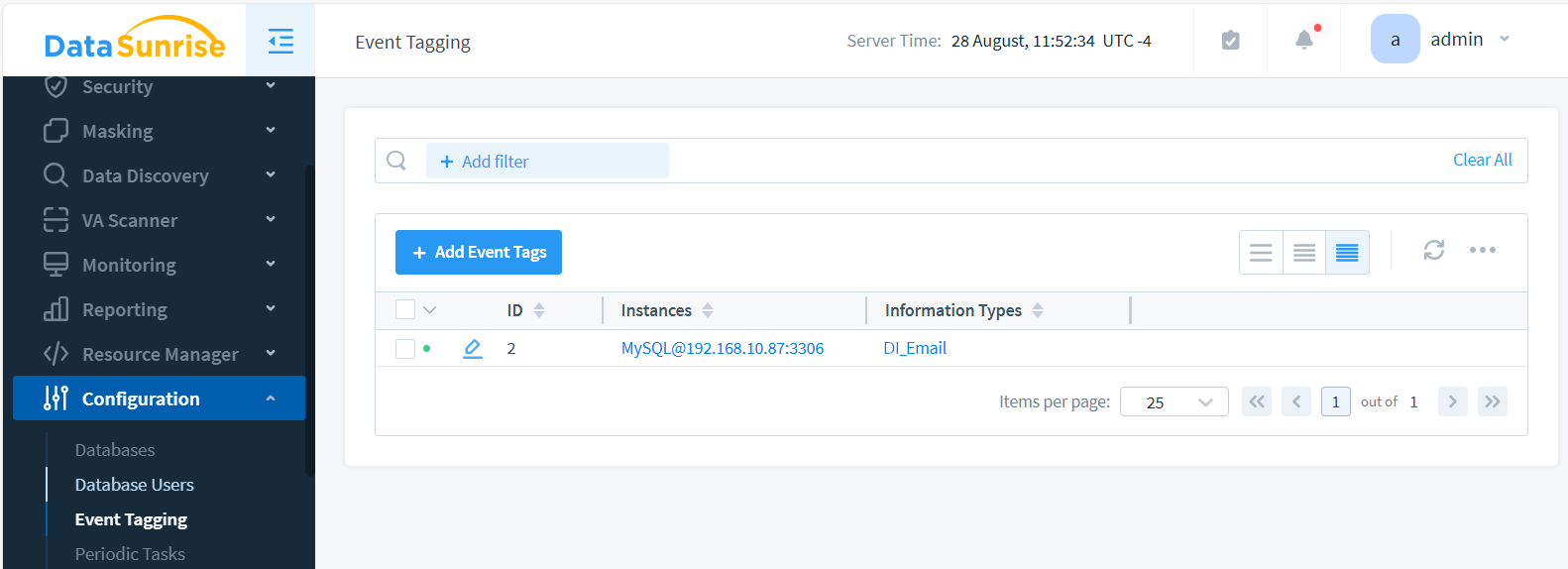
Navigate to Configuration > Event Tagging and click the +Add Event Tags button. Select the checkboxes next to the database instance(s) where you want to audit the data, as well as the Information Type. Since we created the DI_Email Information Type earlier, we’ll use it to create the Event Tag. After saving, your list of tags should look like this:
Audit Rule to Generate Tagged Audit Log
Navigate to ‘Audit’ > ‘Rules’ > ‘+ Add New Rule’ to create an Audit Rule. Name it ‘EmailAuditRule’. Enable ‘Log Query Results’ and select the Instance where you previously configured Event Tagging.
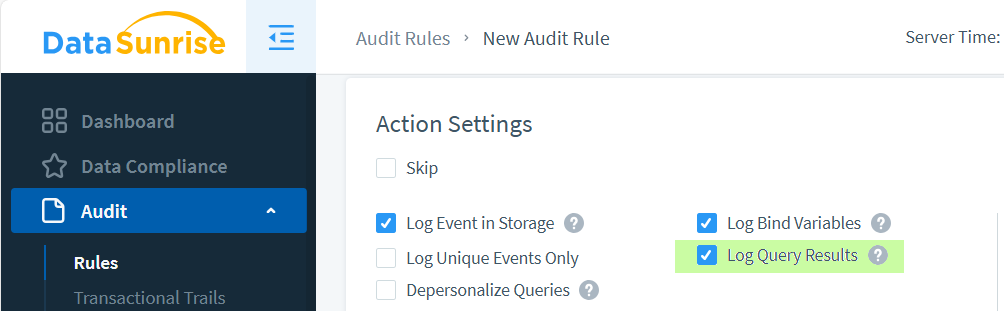
We’re ready to test Event Tagging.
Make a request for email data to the instance. Now, when query results are saved in audit trails, you’ll see this tag in the Transactional Trails:
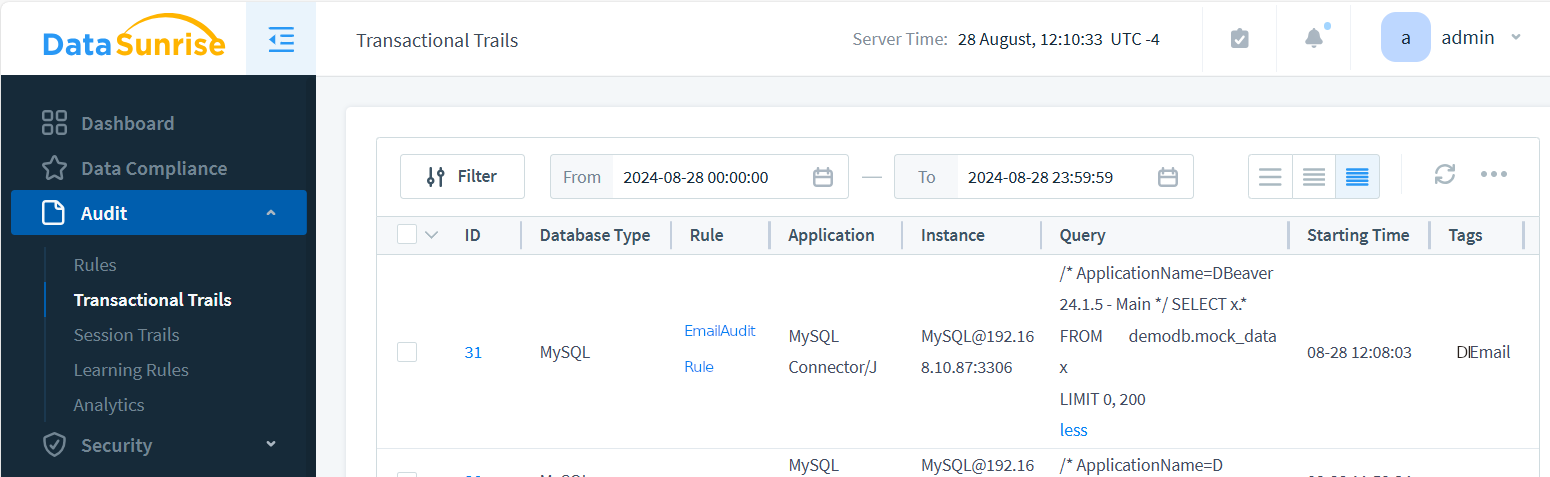
The image above shows EmailAuditRule triggered by a SELECT * query to MySQL@192.168.10.87 instance. This query returned emails among other data from the mock_data table, so the audit event is tagged with the DI_Email Event Tag we created.
Important note: If the data-inspired masking rule discussed below is enabled, the event tag will not label the audit trail event.
Masking for Data-Inspired Security
In the previous chapter, we set up an audit rule and observed how a tag was assigned to an event when it matched our custom DI_Email Information Type. However, tagged data has far more valuable applications beyond simple audit reports.
Now, let’s explore another use of event tagging. When the DI_Email Information Type is detected by the proxy, you can configure various rules to use this as input. Audit, Security, and Masking rules can all be triggered or filtered using these additional tags. In this section, we’ll explain how DataSunrise masks labeled data on the fly, returning masked emails to the database client.
To achieve this, you simply need to create a Dynamic Masking Rule with a Data Filter in the Masking Settings. Let’s walk through the details.
Create the rule as you normally would on the Masking > Dynamic Masking Rules page. Select the database instance where you set up Event Tagging — MySQL@192.168.10.87 in this case. Enable the ‘Log Event In Storage’ checkbox.
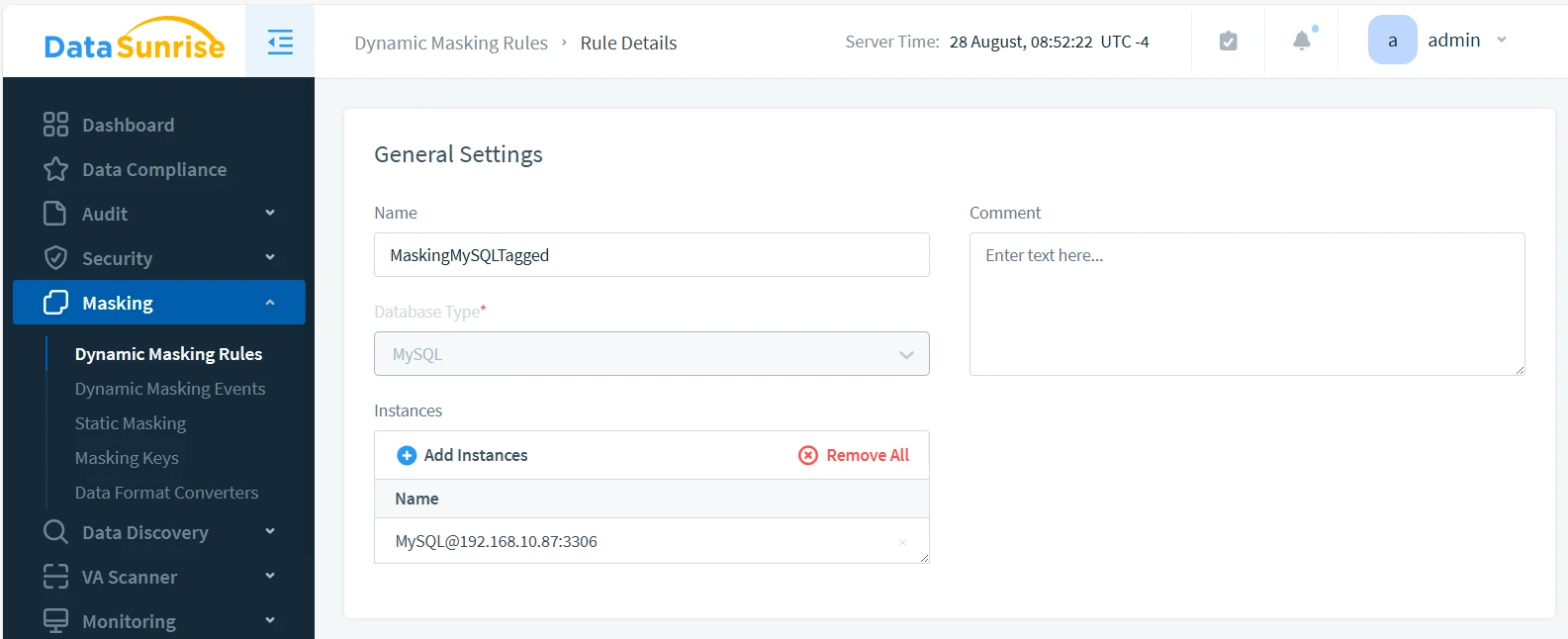
In the Masking Settings shown below, we’ve set the Masking Settings By dropdown selector to Data Filter. This allows us to use Information Types for masking.
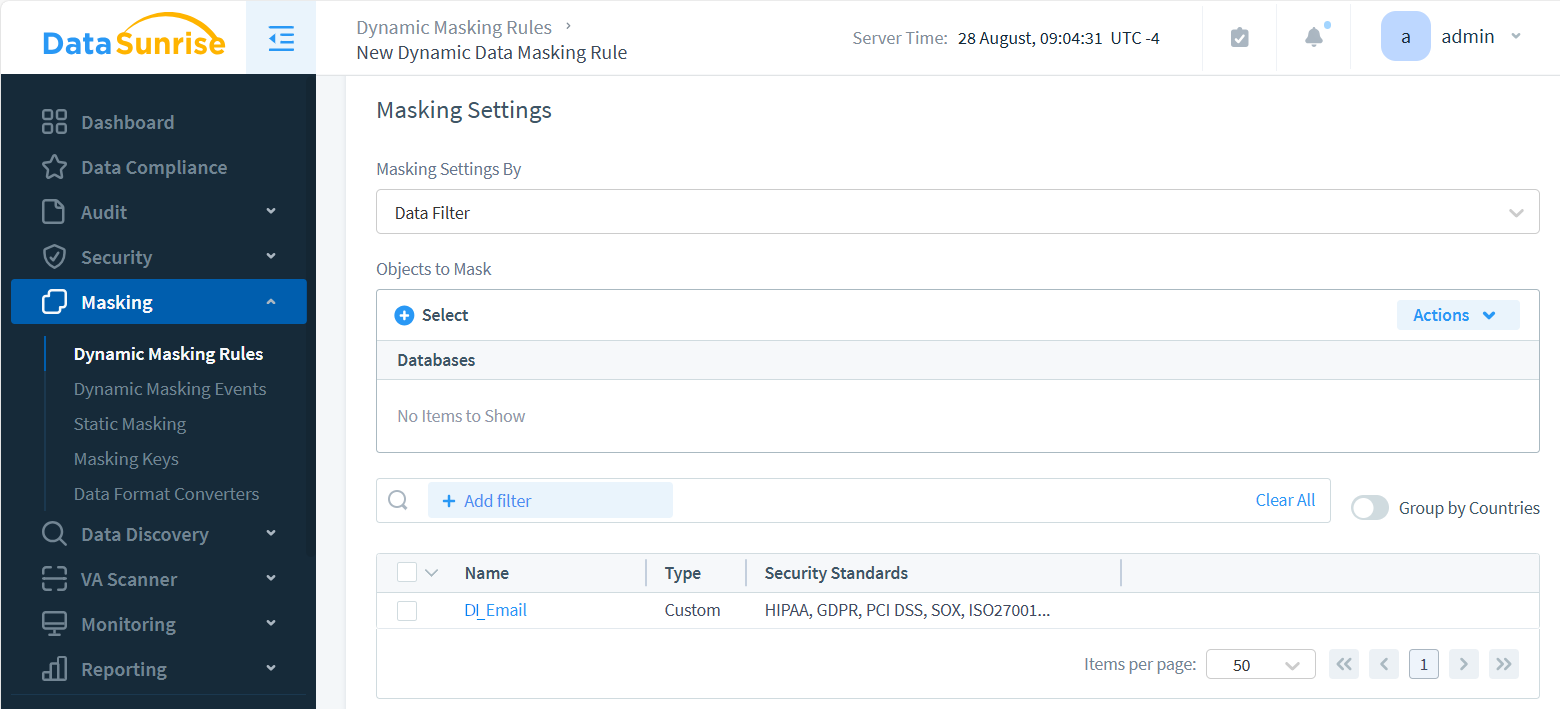
Notice that the Objects to mask selector is left empty. This means that all objects queried from the masked instance are checked for a match with DI_EmailAttribute. If they match, DataSunrise masks them. Use the Object Selector to add specific database objects as additional conditions for masking operations.
The illustration below shows the result. We queried the data through the proxy using the DBeaver database client application. DataSunrise automatically detected and masked the emails in the response based on the Information Type found in the query results:
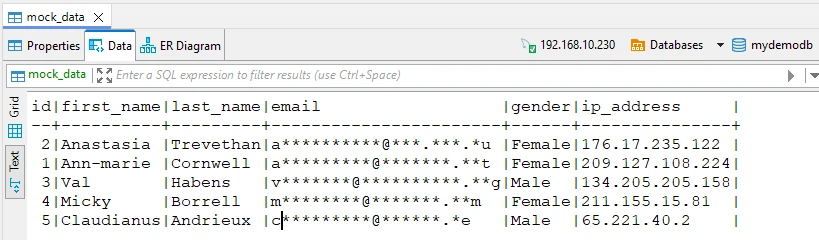
Data-Inspired Security for Audit and Security Rules
With DataSunrise, you can leverage Information Types and Event Tags within Audit Rules and Security Rules to determine whether a query should be audited or blocked. The images below show how to set up Data Filtering for both Audit and Security rules.
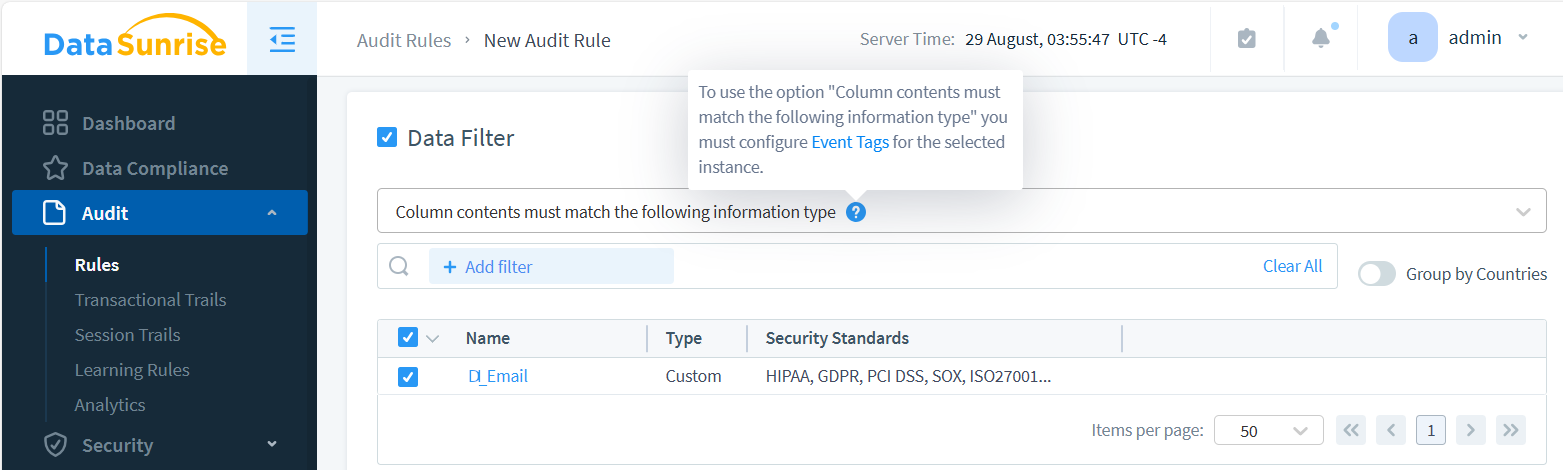
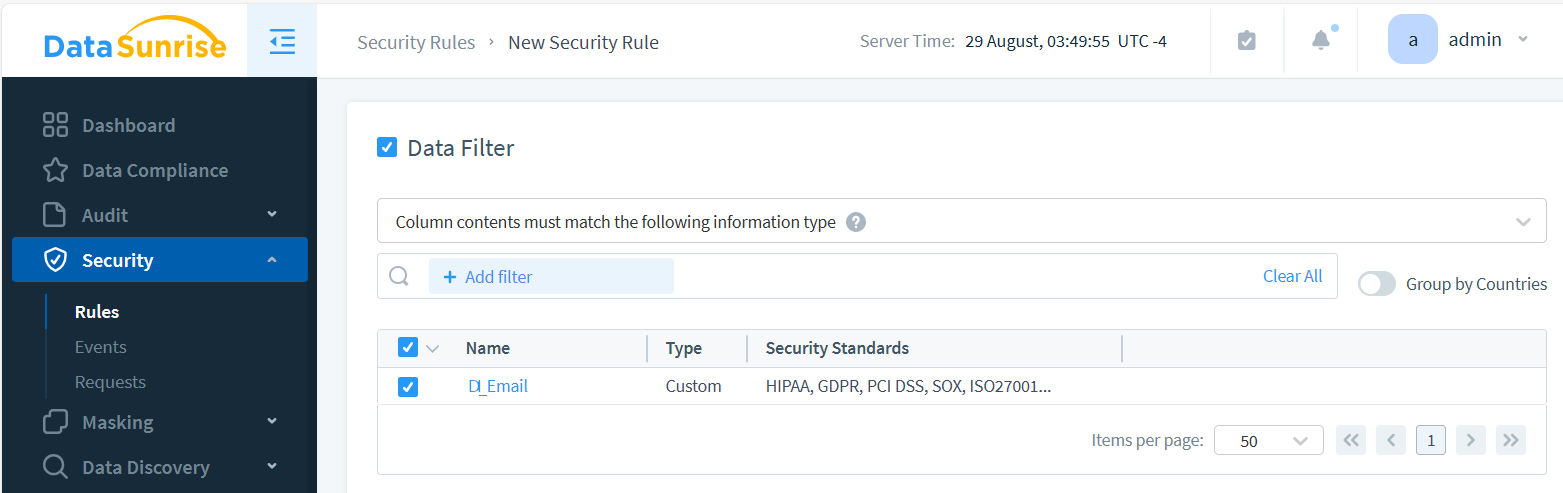
Note that if Event Tagging isn’t configured for the selected database instance, the Information Type option won’t be available in the Data Filter section. Enable the ‘Log Event In Storage’ checkbox in the security rule, as this is required for the data-inspired feature to function.
Conclusion
Data-inspired security begins with tagging data intercepted by the proxy from client-database traffic. Event Tagging allows you to create easy-to-use audit log files, which can be integrated into your data pipelines. As you advance in data-inspired security, dynamic data masking leverages Information Type checks to inform security decisions, such as masking sensitive data.
DataSunrise offers a comprehensive, cutting-edge data security solution that covers data compliance, SQL injection detection, masking, and auditing. Additionally, it includes features like data discovery, vulnerability assessment, and LLM data security. Ready to explore the latest in data security? Visit our website to schedule an online demo or download a free two-week trial of our data security suite.
Next
