
Authentication Proxy for DBaaS
Database-as-a-Service platforms provide access to the database without the need for implementing physical hardware and installing software. Many organizations choose cloud databases due to their scalability, advantageous pricing, and rapid provisioning. However, there are some essential issues that could dissuade them from using DBaaS. Cloud database providers are responsible for the security of data stored on hosted databases but they cannot protect against impersonation and account hijacking attacks.
Cloud databases are available through the network and can be accessed using only the login and password provided by a DBaaS vendor, which draws the attention of hackers and poses a threat to data privacy.
DataSunrise presents a database authentication proxy to largely reduce the risk of unauthorized access and maintain a secure connection to Amazon Redshift, Greenplum, PostgreSQL, Vertica, Netezza and other cloud-based databases. DataSunrise maintains the organizational authentication policies of Microsoft Active Directory and Kerberos protocol. Once user mapping is configured, users will be able to connect to the cloud database through the DataSunrise proxy using Active Directory user credentials.
When a machine, integrated into an Active Directory domain, tries to access the database through the DataSunrise proxy, DataSunrise binds with Active Directory service and checks whether the computer is in the AD domain. Performing full Kerberos authentication based on ticket exchange, DataSunrise ensures a secure connection to the database. Kerberos protocol messages are protected against eavesdropping and replay attacks. DataSunrise supports MD5, SHA-256, and SHA-512 encryption algorithms to store passwords.
Active Directory users to be mapped to one database user (Figure 1.b) or each AD user can be mapped to a separate database user (Figure 1.a).
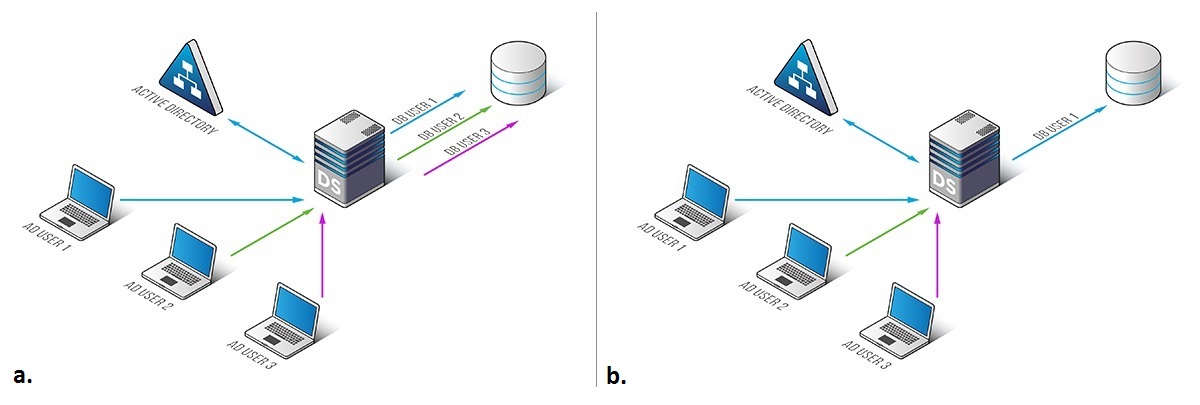 Figure 1. DataSunrise Authentication proxy.
Figure 1. DataSunrise Authentication proxy.
By default, cloud database platforms have a crucial security flaw in database authentication which can be easily eliminated by implementing third-party authentication solutions that support Kerberos or LDAP protocol, such as DataSunrise Database Security Suite.
Contact us, to get the instruction manual on how to configure user mapping on DataSunrise.
