Simple Data Masking with DataSunrise
The Data Masking feature is about protecting sensitive data of any kind by replacing it with special characters or fictive useless data. It is a commonly occurring measure when working with credit card numbers. Most receipts provide only the last four numbers of the card, replacing other numbers with asterisks (*) or Xs.
As the name suggests, the DataSunrise Data Masking tool is used to mask the data a database contains. In this article we will highlight some data masking related points.
Why Do We Need Masking?
The main reason to apply dynamic Data Masking is to protect personally identifiable data or commercially sensitive data. Companies storing critical data bear responsibility for the privacy and confidentiality of their client’s data. Federal laws and regulations such as GDPR, SOX, HIPAA and PCI DSS place exacting demands on organizations to keep the data secure. Data masking is one of the ways to comply with those requirements. Especially when you work with third-party employees who need to access your database for reporting, testing or developing purposes.
In most cases, software developers don’t need the actual data from the database, a “dummy” database with consistent fictive data is enough. It is also a helpful tool when you need to mask only certain columns of the database. Sophisticated masking algorithms make it impossible for a user to retrieve the original data by means of reverse-engineering.
Compared to encryption, masked data remains partially readable. With the help of masking patterns, you choose which part of the content has to be masked.
Comparison of the Main Features of Dynamic and Static Data Masking
DataSunrise can perform Static Data Masking. These are the features of Static Data Masking:
- A full copy of the database with masked information is created.
- Additional space for the copy of the database is required.
- The database can be out-of-date if the original data is edited. It may be necessary to update the copy database periodically.
- It is completely impossible to retrieve the original data, as the database content is changed, not just masked. But before masking the real data must be extracted from the database, which poses an exposure threat.
DataSunrise can perform Dynamic Data Masking. These are the features of Dynamic Data Masking:
- The data is masked on-the-fly at the moment of request. Dynamic Data Masking software intercepts the client query and changes the database response.
- Doesn’t require any additional server resources.
- The database is always up-to-date.
- No need to extract the whole database. The original content is changed before leaving the database.
Shortcomings of Dynamic and Static Data Masking
Dynamic Data Masking has its shortcomings. Stored procedures can’t be dynamically masked because their execution algorithms are stored within the database and client applications just request the execution according to an already existing plan. Thus, masking of stored procedures requires rewriting the query results, not the query itself as DataSunrise currently does.
The shortcoming of Static Data Masking is the need to retrieve data from the database for analysis before starting masking. At the same time, there is a risk of data disclosure, therefore, the security level of the procedure is reduced. Another shortcoming is that creating a large database can be costly, as an additional server may be required.
Dynamic Data Masking with DataSunrise
As you can see, the Dynamic masking method is much more versatile and that’s why we use it in our product.

DataSunrise Database Security Suite works as a proxy — it intercepts SQL-queries to the protected database and modifies these queries in such a way, that the database outputs not actual, but random or predefined data.
Before you use DataSunrise Dynamic Data Masking you need to determine which database entries need protection and where they are located. Note that DataSunrise can mask a complete database as well as data in separate columns only. DataSunrise logs all the actions, so you can check what is happening anytime.
Using the DataSunrise masking tool is very easy. All you need to do is to enter the DataSunrise dashboard and create some masking policies.
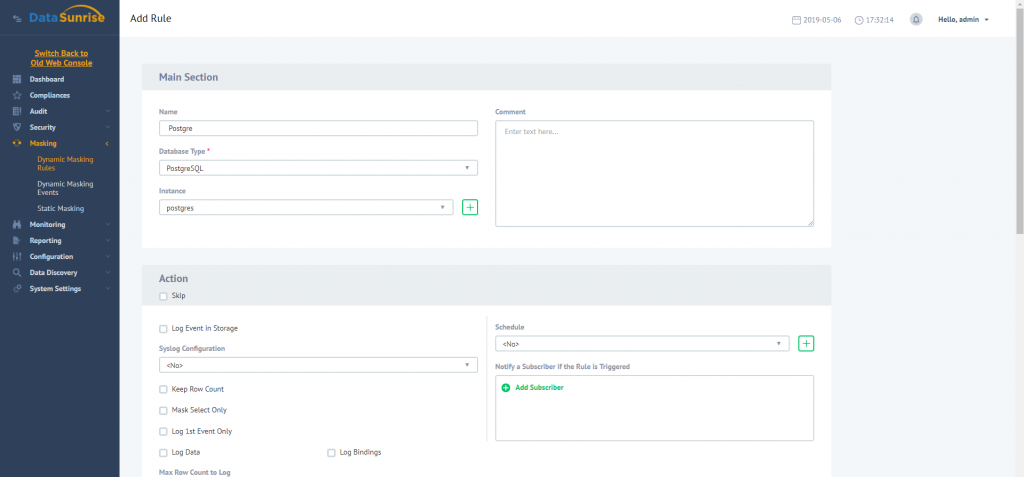
Here you need to enter information required to create a masking rule. You can define application which requests will be processed by the firewall. Then you need to define SQL-statements to be filtered and select masking type to be implemented. It means that you can select a method of generation of fake entries.
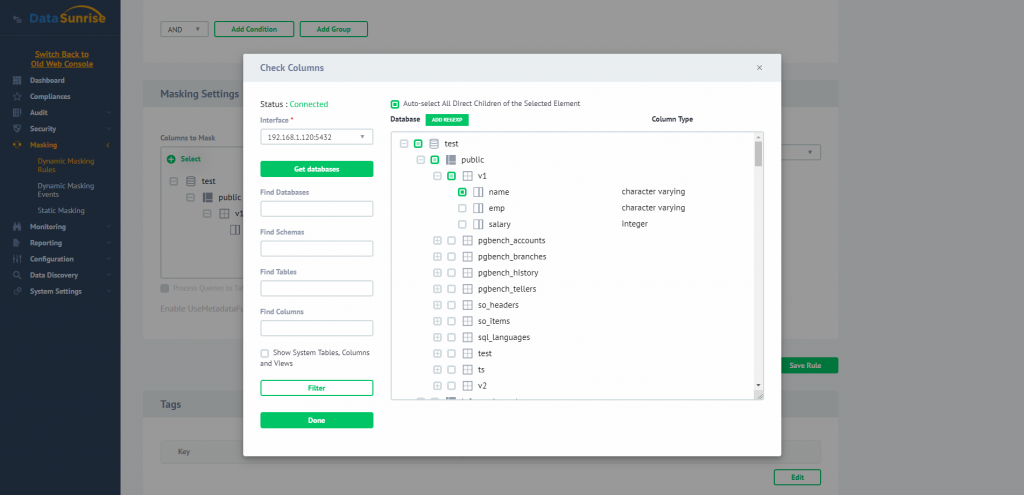
Then you should select the database elements (schemas, tables or columns) to be protected. It can be performed manually via handy database elements explorer or by using regular expressions.
And that’s all. Quite simple.
Static Data Masking with DataSunrise
DataSunrise also has Static Data Masking capability.
As it was previously mentioned, static masking enables you to create a fully functional copy of a production database but with masked data inside. You can use such a copy for testing or development purposes.

First, to employ static masking you need to create an empty copy of the target database. Then open DataSunrise Web Console, Static Data Masking subsection.
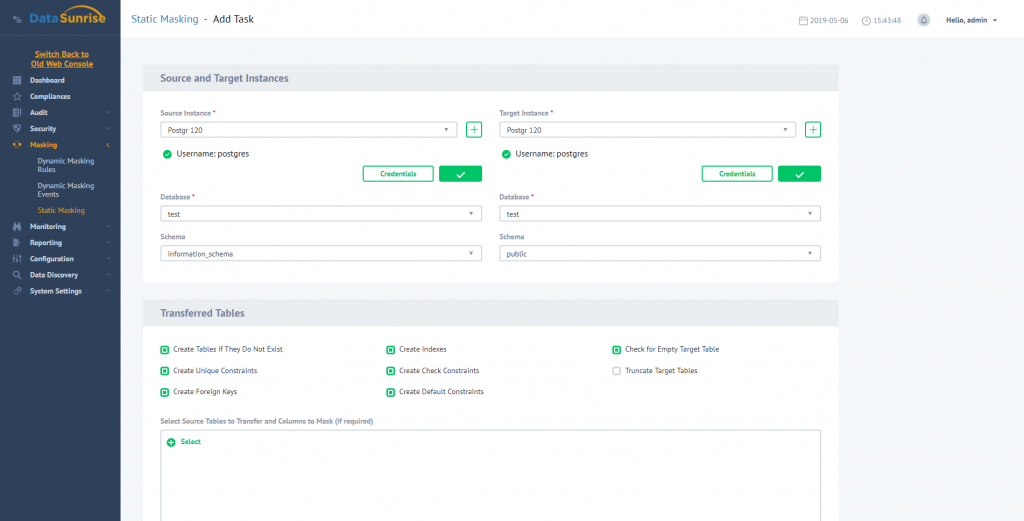
Here you need to specify which database should be used as a source of data and which one is the target one (the “dummy”).
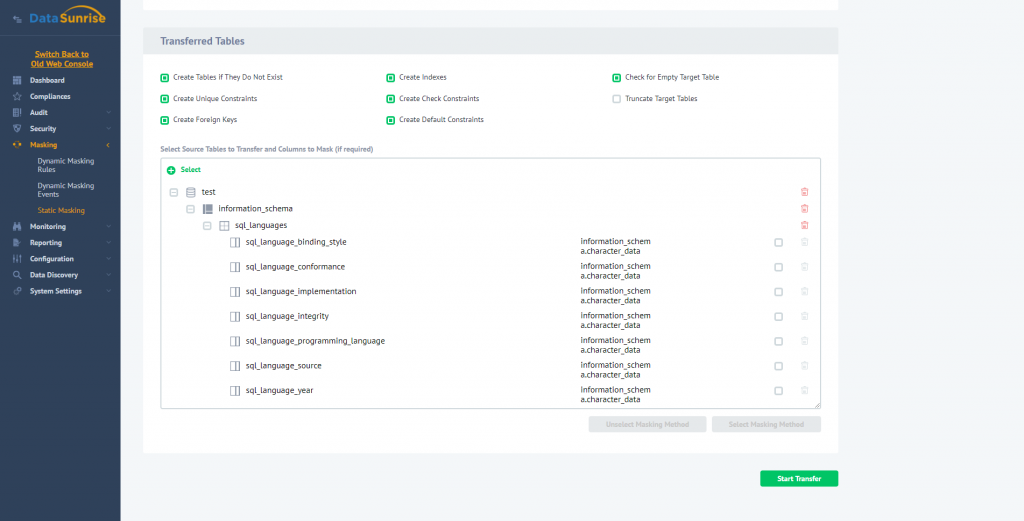
Selecting columns to be masked and masking types. Having it done, specify a table which should be transferred to a new database, and masking algorithms to apply (“Card” and “Email” columns here). Then you can start the masking process and compare original and masked data. Original:
| Order | FirstName | LastName | Address | State | ZIP | Card | |
|---|---|---|---|---|---|---|---|
| 4667 | Alma | Wade | 21 Green Lane, Newport | NE | 21771 | almwa@nprt.com | 6011-0551-9875-8094 |
| 6768 | Patric | Chang | 7 Marina View, Bergenfield | OR | 46368 | changgg@cheu.com | 5529-9038-2746-5861 |
| 5356 | Mona | Cherry | 31 The Village, Cranford | GA | 60515 | cherry@vill.com | 4539-7765-7903-5426 |
And with obfuscation applied:
| Order | FirstName | LastName | Address | State | ZIP | Card | |
|---|---|---|---|---|---|---|---|
| 4667 | Alma | Wade | 21 Green Lane, Newport | NE | 21771 | a****@****.**m | XXXX-XXXX-XXXX-8094 |
| 6768 | Patric | Chang | 7 Marina View, Bergenfield | OR | 46368 | c******@****.**m | XXXX-XXXX-XXXX-XXXX |
| 5356 | Mona | Cherry | 31 The Village, Cranford | GA | 60515 | c*****@****.**m | XXXX-XXXX-XXXX-5426 |
Note: of course, in reality you’d want to use more obfuscation, but it is a simple example just to get the idea.
Conclusion
DataSunrise Data Masking provides you with another reliable tool for data protection. Along with DataSunrise Database firewall and SQL injection prevention capability, it can become an additional line of defense against digital threats.
DataSunrise supports all major databases and data warehouses such as Oracle, IBM DB2, IBM Netezza, MySQL, MariaDB, Greenplum, Amazon Aurora, Amazon Redshift, Microsoft SQL Server, Microsoft SQL Azure, Teradata and more. You are welcome to download a free trial if would like to install on your premises. In case you are a cloud user and run your database on Amazon AWS or Microsoft Azure you can get it from AWS market place or Azure market place.
For more information about DataSunrise Database Security capabilities please refer to DataSunrise user guide or schedule an online demo.