What is the Goal of a Database Security System?
What is database security?
Database security refers to dedicated means used to protect data stored in databases or database management software from hacker attacks and insider-driven threats. It includes a multitude of processes, tools and strategies that ensure security of a database environment.
Why is Database Security Important?
As practice shows, security breaches and data leaks can be very costly for not only your company’s reputation but also the bottom line.
According to IBM’s 2019 Cost of a Data Breach Report, the global average cost of a data breach for 2019 is $3.92 million, a 1.5 percent increase from the 2018 study. The average total cost of a data breach climbed from $3.5 million in 2014, showing a growth of 12 percent between 2014 and 2019. Just as it was last year, the most expensive country in terms of the average total cost of a data breach is the U.S. at $8.19 million, more than twice the global average. Healthcare was again the most expensive industry for data breach costs, with the total cost of a data breach in 2019 averaging $6.45 million.
What Is Security Risk? What Risks Can I Face?
Database threats can be caused from inside and outside. Outsider-driven threats are hacker attacks mostly. This includes exploitation of database bugs and system weaknesses, SQL Injections, etc. Insider-threats include unintentional data leaks and intentional abuse of access rights etc.
Some security risks to database systems include:
- Intentional or unintentional activity or misuse by authorized database users, privileged users, or by unauthorized users or hackers (unauthorized access to sensitive data, metadata or functions within databases, or inappropriate changes to database programs, structures or security configurations);
- Virus infections causing incidents such as unauthorized access, leakage or disclosure of personal or proprietary data, damage to the data or programs, DDoS attacks, attacks on other systems;
- Overloads, performance decrease and capacity issues resulting in the inability of authorized users to use databases as intended;
- Data corruption and/or loss caused by the entry of invalid data or commands, inappropriate database or system administration processes, sabotage, etc.
What Can I Do to Prevent a Security Breach?
All software-related threats can be mitigated with dedicated security software such as DataSunrise.
DataSunrise includes three database security components: Database Firewall, Dynamic and Static Data Masking, and Database Activity Monitoring.
The Database Firewall protects the target database from security threats such as SQL injection attacks (hacker attacks) and access rights abuse. It blocks queries prohibited by the firewall administrator basing on query code and query source (database user, host, IP address, etc.).
The Dynamic Data Masking protects the data in the target database from insider-driven data leaks. It replaces the actual database entries with some neutral yet realistic data. This enables you to restrict certain database users from viewing the actual database contents without warning them. Static Masking enables you to prevent a data leak when you need to give access to your database to third-party developers or analysts. It creates a copy of your database with obfuscated data inside. Such a copy can be given to outsourcers without any threat of data leakage.
DataSunrise’s Data Audit component enables you to perform database activity monitoring and audit. Security-wise, it can help you to reveal a breach in progress, suspicious user behavior, create allow and deny lists.
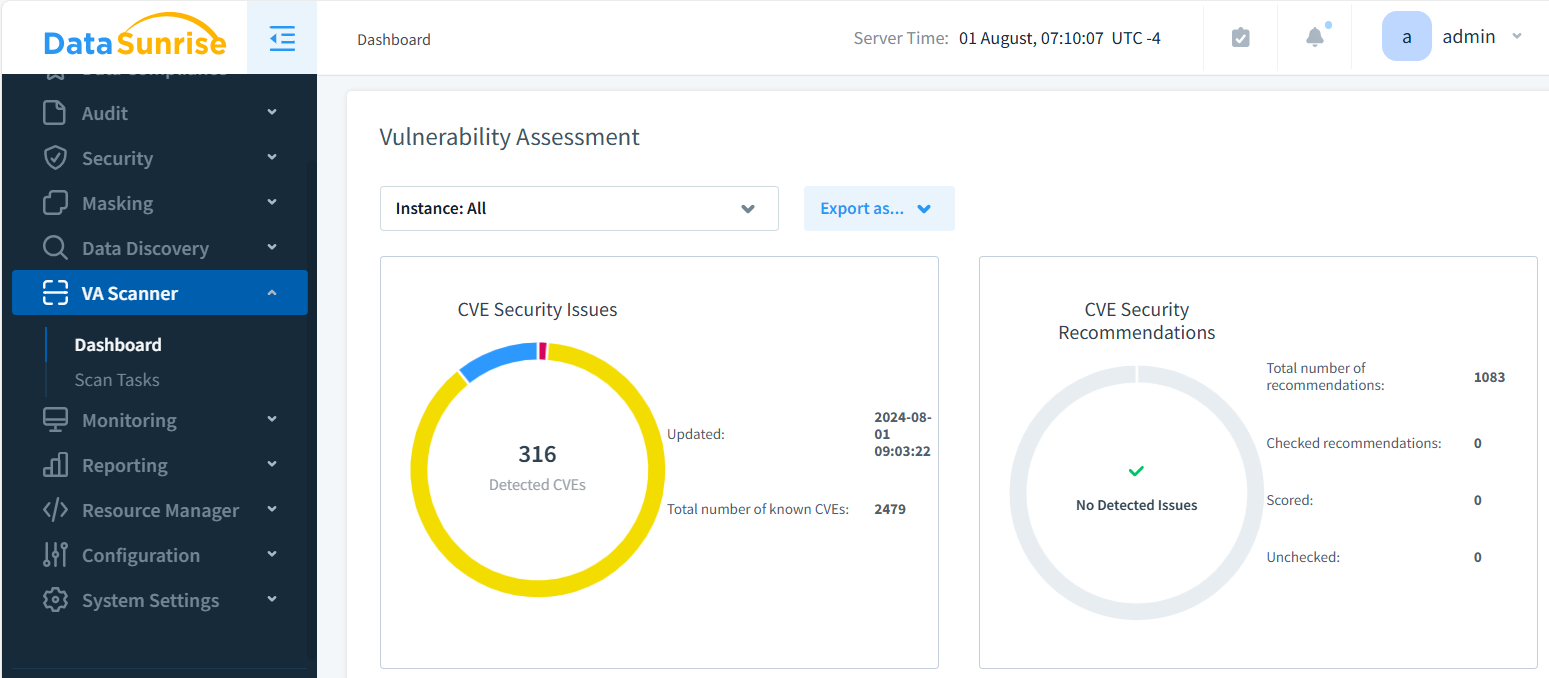
Vulnerability Assessment From DataSunrise
This feature enables you to view all known vulnerabilities for the databases included in your DataSunrise’s configuration. The list of vulnerabilities can be downloaded from the DataSunrise web site in the form of an SQLite database file. First, you should create a dedicated periodic task to check the availability of the vulnerabilities database and download the required files. If there is a new version of the database file is available and the internet connection is available, DataSunrise downloads it from update.datasunrise.com and saves in the AF_HOME folder. Then the periodic task browses DataSunrise’s configuration and forms a list of vulnerabilities for each of the databases included in the configuration. This information is saved in the task’s results.